Introducing ICT systems
Use 'Print preview' to check the number of pages and printer settings.
Print functionality varies between browsers.
Printable page generated Friday, 26 April 2024, 2:52 PM
Introducing ICT systems
Introduction
This course will introduce you to some ideas about how information and communiction technologies (ICTs) systems work. We will look at how ICT systems convey, store and manipulate data, and how they process data. Finally, using the example of a supermarket, we will analyse how ICT systems are used.
This OpenLearn course provides a sample of level 1 study in Computing & IT

Learning outcomes
After studying this course, you should be able to:
understand the meaning of all the terms highlighted in the text
demonstrate an awareness of the main processes in an ICT system (sending, receiving, storing, retrieving, manipulating, conveying)
demonstrate an awareness of some of the hardware, software and communication components used in ICT systems
use a system map or a block diagram to identify the components of an ICT system
use the units for conveying data and those for storing data apporpriaterly, including use of the prefixes kilo, mega and giga.
1 Describing an ICT system
In this course I shall be introducing you to some ideas about how ICT systems work. Because this course is about ICT systems, I'll be starting with a discussion about what constitutes a system. I'll go on to introduce some diagrammatic ways of representing ICT systems. Then I'll look at some examples to illustrate how they carry out certain processes, namely conveying, storing and manipulating data. You will also find out about other processes performed by ICT systems.
In this section I'll start by discussing how taking a 'systems' view of ICT systems can help our understanding of them. Later in the session. I'll be focusing on the communication component of an ICT system.
2 Exploring systems
2.1 Introduction
There are many types of system – not just ICT systems. For example, we all have a nervous system and, as you are studying T175, you are in a higher education system. Our homes have plumbing systems and electrical systems.
Activity 1 (exploratory)
What systems do you come across in your daily life? Write down two or three examples under each of the two headings below:
| Systems in your home | Systems outside the home |
Discussion
Your examples of systems might be very different from mine, but here's my list:
-
In my home there are systems such as the stereo system, my (not very efficient) personal filing system, the central heating system.
-
Systems outside the home include: an appointments system to see the doctor, a library system for borrowing books and other media, a booking system for a concert or the theatre.
In the workplace there are systems such as the telephone system, the payroll system, the budgeting system, the internal mail system and, of course, the computer systems.
As you can see from my list, and probably from your own, the word 'system' can be used in a number of ways. At first glance, there may not be much in common between a nervous system and an education system or an ICT system, but they are all called 'systems' so it is likely that they share some features. One important aspect of a system is connectedness. A plumbing system, for example, involves components such as pipes, taps and valves, which are all physically connected in some way. The components are put together to perform a certain function, in this case to supply water to a building.
Systems do not always involve physical things; the components may be activities or even ideas. Putting on a concert, for example, involves activities such as hiring a hall, holding rehearsals and selling tickets. These activities can be viewed as a system for putting on a concert because they are put together in order to carry out that function.
2.2 A system map
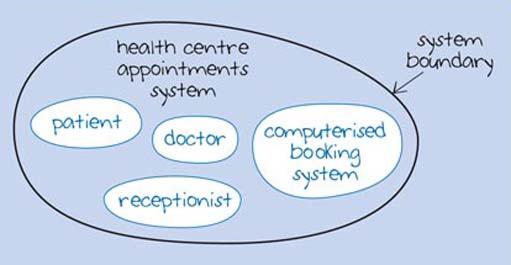
One way of explaining and analysing a system is to represent it in a graphical form, known as a system map. I'll use the example of a system for making an appointment with a doctor in a health centre to illustrate this point. In this example, the health centre uses a computerised booking system and the patient may phone or visit the health centre to make an appointment. Therefore, the system includes a patient, a receptionist, a doctor, and a computerised booking system. The example shown in Figure 1 shows how this system could be represented using a system map. I have called the system a 'health centre appointments system' and you can see a number of blobs called 'patient', 'doctor', 'receptionist', and 'computerised booking system'. These are the components of the appointments system. The thick line around these is the system boundary that defines which components are part of the system and which are outside it.
2.2.1 Subsystems
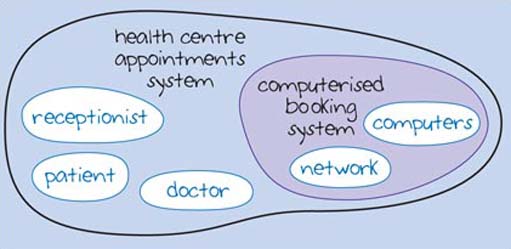
An important aspect of systems is that each component can be considered as a subsystem. In the health centre appointments system, the 'computerised booking system' may be a complex system in its own right involving a number of computers networked together. Figure 2 shows this view of the system with 'computerised booking system' composed of two subsystems: 'network' and 'computers'. Of course, these subsystems may also be complex systems in their own right, composed of further subsystems.
A complex overall system can therefore be reduced to more manageable proportions by grouping components together and thinking about it in terms of subsystems. You can think of the subsystems as being 'nested' inside a system or another subsystem, a bit like Russian dolls. No single one of them is 'the doll'; each one fits inside the larger one. A system map can help by allowing us to focus on the particular systems and subsystems that we are interested in.
2.2.2 Drawing the boundary
Deciding where to place the system boundary is an important consideration in that we have to think about what to include and exclude. This isn't always an easy decision to make and it often depends on the perspective of the person viewing the system.
The system maps in Figures 1 and 2 show the 'doctor', 'patient', 'receptionist' and 'computerised booking system' as part of the system. However, in Figure 3 the doctor and the patient are placed outside the system in an area that is called the system's environment; Figure 3 shows a perspective where the doctor and patient are not part of the system directly, although they influence it or are influenced by it. By placing them outside the system boundary, the focus is shifted towards the computerised booking system and how the receptionist uses it.
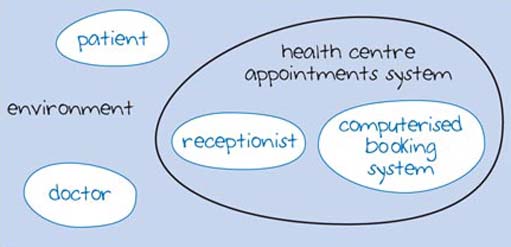
Figure 3
Figure 4 illustrates yet another view of the health centre appointments system. Here the doctor and patient are seen as irrelevant and so do not appear at all in the system map. This view of an appointments system embodies yet another shift in emphasis. It is a view that might be taken by engineers who are concerned with the hardware and software of a computerised system (these are discussed in more detail in sections 8–14). However, this view is too narrow, and therefore risky, when designing new systems or planning enhancements to existing ones. Ignoring some of the users of the system or 'stakeholders' could lead to a booking system that doesn't do the job it was intended to do.
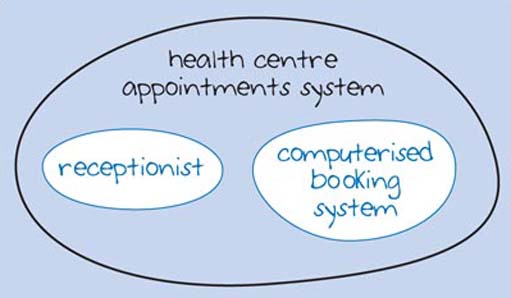
Figure 4
Activity 2 (exploratory)
An email communication system includes:
-
the sender
-
the recipient
-
the sender's computer
-
the recipient's computer
-
the internet
Draw a system map to represent this email communication system (roughly oval outlines will be fine). Do you think the users (the sender and the recipient) should be inside the system boundary or outside it?
Discussion
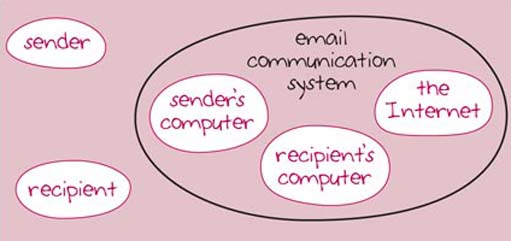
Figure 5 shows my system map. Where have you drawn the boundary? Does it include the sender and the recipient as the users of the system within the system boundary, or outside it? As you can see, I have drawn the users outside the system boundary, in the environment. Whether users of an email system feel outside or inside the system is an interesting question.
I've introduced system maps for two main reasons. Firstly, it is important to realise that systems are composed of subsystems and that these subsystems are often themselves composed of subsystems. This idea will help us as we explore ICT systems. Secondly, we may draw the system boundary in different places at different times. For example, if we want to discuss the social or economic impact of a particular ICT system, we will be drawing the boundary very widely indeed but if we want to look at how some subsystem in an ICT system works, then we will be drawing the boundary very tightly around the subsystem.
2.3 Models of an ICT system
To help me to introduce you to important ideas about ICT systems, I'm going to take a three-stage approach. ICTs involve conveying, manipulating and storing data. This is going to be the basis of my approach.
Firstly, in the next few sections, we'll look at ICT systems where the primary function is to convey data. We can think of these systems as communication systems and I'll use a mobile phone system as an example.
In sections 8–14, I'll focus on ICT systems where the chief function is to manipulate and store data. A computer is a primary example of this kind of ICT system, so I'll use a personal computer like the one you are using in your study of this course as an illustration.
Finally, in section 15–19 I'll show how the conveying, manipulating and storing of data can all come together in an ICT system. This convergence of conveying, storing and manipulating data has led to many new and exciting developments, as you will see during your study of this course.

3 Communication systems
3.1 Introduction
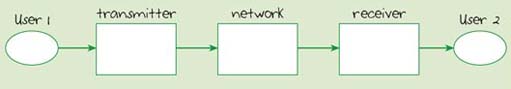
Generally, when we talk about communication between humans, we mean one person conveying information to another person. Figure 6 shows a basic model, or representation, of a communication system for getting a message from the sender to the recipient. The diagram shows the sender (User 1), the message, a 'means of conveying a message' and the recipient (User 2).
Figure 6 is an example of a block diagram, which is another graphical way of representing a system. Each block represents something in the real world, and the labels on the blocks tell you what that 'something' is. In this diagram I have chosen to represent people and inanimate objects in different ways. The oval shapes (which are still called 'blocks') represent the users of the communication system. The rectangular blocks represent inanimate objects in the communication system. The lines between the blocks represent the flow of something: here it is the message.

DESCRIPTION REQUIRED
Activity 3 (exploratory)
Suppose you were planning a birthday party for someone. How could you communicate the message – that is, the details of the date, the time and the venue – to your prospective guests? Jot down four methods of communication. In each case, think of what is needed to convey the message.
Discussion
The four methods of communication I thought of are as follows. If my guests live in the same house as me, or if I happened to meet the people concerned, I could just tell them the date, time and venue. If not, I could send them an invitation using the postal system. Alternatively, I could telephone them to give them the details, which involves using the telephone network. I could also email the people I wanted to invite, if I knew their email addresses, which would involve using a computer network – probably the internet.
In each of these situations we could say that communication involved a sender, a recipient, some form of message and some means of conveying the message. The various means of conveying the message in my answer include voice communication, the postal system, the telephone network and a computer network.
Activity 4 (self-assessment)
ICTs are the technologies used in the conveying, manipulation and storage of data by electronic means. Which of the four means of conveying the message in Activity 3 involve ICTs?
Answer
The first method of communication involves only voice communication. The second, the postal service, does not directly involve ICTs to deliver the message.
The means of conveying a message that directly involve ICTs are the telephone and email. The telephone system involves a telephone network and handsets. An email system involves computers and a computer network.
3.2 Looking into the 'means of conveying a message'
The diagram in Figure 6 shows that, for communication to take place, there needs to be some means of conveying the message between the sender and the recipient. I am now going to look at the essential components of 'means of conveying a message'. In other words, I shall treat 'means of conveying a message' as a system and look at its components.
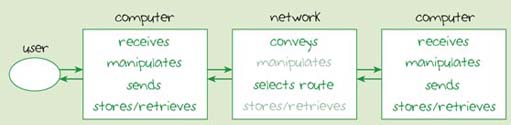
Three essential components of 'means of conveying a message are: a transmitter, a network and a receiver. Figure 7 shows these components in a block diagram. In a mobile phone system, for example, the 'transmitter' would be User l's mobile phone, the 'network' would be the mobile telephone network and the 'receiver' would be User 2's mobile phone.
4 System components
4.1 Introduction
I'll now look at what these components do in the communication system, using the mobile phone system as an example.

4.1.1 The transmitter
The transmitter receives a message from User 1 and manipulates it into data which can be sent into the network. The transmitter may also store or retrieve data relating to the message.
In the mobile phone system, the transmitter, which is User l's mobile phone, receives a message from User 1 in the form of sound. It manipulates the incoming sound into a data format suitable for sending into the mobile phone network. Even basic models of mobile phone handsets can store names and telephone numbers, so in this example the transmitter is also storing and retrieving data.
4.1.2 The network
The network is a communication channel in that it conveys data from the transmitter to the receiver. The network may also manipulate data in some way, and it may also store or retrieve data.
In a mobile phone system, the network conveys the message from User l's handset to User 2's. It will also store the identity of User 1 and the duration of the call. This data is used to work out the amount to charge User 1, which is a form of manipulation of data. A network can be very complex, so a call does not usually go directly from one caller to another in a single step. The network, therefore, will select the route for conveying a call through the network from the transmitter to the receiver.
4.1.3 The receiver
The receiver receives data from the network and manipulates it into a message to send to User 2. Sometimes the receiver may also store or retrieve data.
In the mobile phone communication system, the data received from the network must be manipulated back into sound before being sent to the user. In addition, some mobile phones can store and retrieve data about the user's contacts, so that when a call is received they can translate the phone number of the caller into a name which is then displayed.
5 The processes
My description of the three subsystems of 'means of conveying a message' has indicated some important processes that each carries out. These are shown in Figure 8. The key processes are those that will always be carried out and they are shown in bold; the other processes may or may not be performed. (I have used this scheme of bold text for essential processes in all block diagrams.)

DESCRIPTION REQUIRED
Activity 5 (exploratory)
-
Look at the processes listed for the transmitter in Figure 8.
-
Now reread my two paragraphs about the transmitter. Underline the processes carried out by the transmitter.
-
Repeat (1) and (2) for both the network and the receiver.
Discussion
Here is my paragraph about the transmitter, amended with the processes underlined.
'The transmitter receives a message from User 1 and manipulates it into data which can be sent into the network. The transmitter may also store or retrieve data relating to the message.
'In the mobile phone system, the transmitter, which is User l's mobile phone, receives a message from User 1 in the form of sound. It manipulates the incoming sound into a data format suitable for sending into the mobile phone network. Even basic models of mobile phone handsets can store names and telephone numbers, so in this example the transmitter is also storing and retrieving data.'
I'll leave you to underline the processes for network and receiver yourself.
6 Communication links
6.1 Networks
Next I'll be looking more closely at the 'network' block in Figure 8, and in particular at the links that must be present before communication can take place. I'll introduce you to just a few of the forms that these links can take; links may be physical ones, such as cables, or they may be wireless, such as radio links. I'll also discuss how we measure the capacity of a link for carrying messages.
Physical cables can provide a path for conveying data between two points. A common example is the telephone wires that are used to connect the 'landline' telephones in people's homes to the nearest telephone exchange. Cables are also used to carry television and often radio signals to the homes of cable TV subscribers. Fibre-optic cables are used to interconnect telephone exchanges. Cables are also used to connect computers together into various kinds of network.
There are two forms of wireless link in common use: radio links and infrared. Millions of people around the world now use mobile phones, and this involves radio links. You may also have come across 'Bluetooth' and 'WiFi' radio links in connection with computers. Bluetooth® is used for short-range wireless links between devices, for example to connect a computer and a printer. A WiFi link, with its slightly longer range, might be used to connect a WiFi-enabled notebook computer to a WiFi 'hotspot' (in a cafe or other public place), which provides a link to the internet.
The other sort of link is an infrared link, which you will have come across when using the remote control for your television set. Infrared can also provide a communications link between computers and devices such as printers. An important difference between wireless links and infrared is that an infrared link must be along a line of sight (for example, the remote control has to be pointed at the television), whereas a radio link need not be.
It is very important that a communication link has the capacity to cope with the messages it has to convey – that is, that it can convey the messages as quickly as they are arriving from the transmitter. The ability of a communication link to convey data is measured by a quantity known as its 'bandwidth'. But what is bandwidth? To answer that question I need to introduce you to the form in which data is normally conveyed in today's ICT systems. This form is a series of pulses – that is, data is conveyed by sending streams of pulses from one end of a communication link to another.
6.2 Working with bits
You may have met the term bit, perhaps in connection with computers. The term 'bit' is also important in communication systems. It is an abbreviation for 'binary digit'. A binary digit can have just one of two values: it can be either 1 or 0. Pulses can be represented by 1s and 0s, that is, as bits, and so it is convenient to think of streams of 1s and 0s being conveyed along the communications link.
The rate at which the 1s and 0s are conveyed is known as the data rate or bit rate. Every communication link has a maximum data rate it can support, and that's what we mean by the link's bandwidth. (You may possibly have met another meaning of the term 'bandwidth': a frequency range. That meaning is different from the one we are discussing here.) Data rate and bandwidth are both measured as a number of bits per second. For convenience, 'bits per second' is often abbreviated to bps. For instance the data rate might be 100 000 bps (i.e. 100 000 bits per second), 250 000 000 bps or much more.
Clearly we are going to have to deal with large numbers when talking about data rates, so I'm going to introduce a way of making these large numbers more manageable.
You will be familiar with the prefix 'kilo' in words such as kilogram, which is 1000 grams, or kilometre, which is 1000 metres. So it will come as no surprise that 1000 bits per second can also be described as a kilobit per second. The prefix 'mega' is similarly used for a million, so 1 000 000 bits per second is a megabit per second The prefix 'giga' is used for a billion (that is, a thousand million).
Activity 6 (self-assessment)
How many bits per second are there in a gigabit per second? Write your answer in both words and figures.
Answer
There are a billion bits per second in a gigabit per second. In figures this is 1 000 000 000.
All of these prefixes have standard abbreviations. For instance, instead of writing 'kilobits per second' we can write kbps – that is, we write k for kilo. Similarly, M is used for 'mega' and G for 'giga'. (Notice that by convention the k is lower-case but the M and G are upper-case.) Table 1 summarises all this information.
| Prefix | In figures this is: | In words this is: | Symbol |
|---|---|---|---|
| Kilo | 1000 | A thousand | k |
| Mega | 1 000 000 | A million | M |
| Giga | 1 000 000 000 | A billion (thousand million) | G |
You may have come across examples of data rates and bandwidths in connection with modems and broadband. At the time of writing (early 2005) a dialup modem typically provides a data rate of 56 kbps, which is 56 000 bps, and Internet Service Providers (ISPs) advertise broadband connections with bandwidths such as 1 megabit per second (which is 1 Mbps or 1 000 000 bps).
Activity 7 (self-assessment)
Have a go at answering these questions to test your understanding of what you have read so far about communication systems.
-
The maximum data rate that a communication link can support is called its____________.
-
The sort of communication link used by Bluetooth is a ____________link.
-
A WiFi link between a notebook computer and a 'hotspot' can handle data at up to 54 megabits per second (54 Mbps). How many bits per second is that?
Answer
-
bandwidth
-
radio
-
54 000 000 bps.
7 Describing an ICT system: conclusion
We have arrived at a model of a communication system that illustrates the processes needed for communication. We have also looked at the different kinds of communication link that can be used to convey data, and how to express the rates at which they can convey data. In sections 8–14, we shall be looking at a computer system as an example of an ICT system where data manipulation and storage are the most important features.

8 Computers
In sections 8–14, I am going to start by considering a stand-alone computer, which is a computer that is not connected to a network. In this type of ICT system, the key processes are the manipulation and storage of data. I'll be introducing some details about the way that a computer manipulates and stores data. Then I'll be discussing the processes that are carried out by computers when they are linked.
9 A stand-alone computer
The computer you are using for your studies is called a personal computer or PC. Although you have an internet connection for use in this course, your computer can probably also be used as a stand-alone computer. Your PC may be a desktop computer or a notebook computer (sometimes known as a laptop computer). Usually a desktop computer comes with separate devices such as a monitor, a keyboard, a mouse and speakers and it runs on mains electricity. Notebook computers are designed to be small and light in order to make them portable, so the screen and keyboard are part of the one course. Notebook computers have the same capabilities as a desktop computer, but can be run on an internal battery as well as from an electrical socket. Figure 9 illustrates some types of computer.

DESCRIPTION REQUIRED
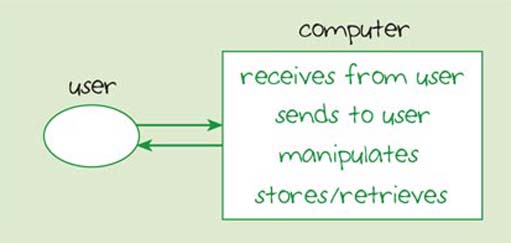
For a PC to manipulate data there need to be processes by which the computer receives data from the user and sends data back to the user. Hence, the block diagram in Figure 10 shows the first process associated with a stand-alone computer as 'receives from user' and the second as 'sends to user'. You will see that 'manipulates' and 'stores/retrieves' are also listed in the diagram. I'm not going to go into a lot of detail about the inner workings of a computer here, but it will be useful for you to know something about how a computer carries out these processes. My starting point will be the 'receives from user' and 'sends to user' processes. Then I'll introduce you to the way a computer carries out its main processes: manipulation and storage.
10 Sending and receiving data
10.1 Introduction
A stand-alone computer receives data from a user by means of input devices. The two most commonly used input devices are the keyboard and the mouse. A computer sends data to a user by means of output devices. Data may be output via devices such as a screen or a printer.
There are many different ways of getting data into a computer. For example, a scanner converts images and texts into a format that can be processed by the computer and displayed on screen. Devices such as touch screens and graphics tablets convert the pressure from stylus or finger strokes into data. Data from digital cameras and camcorders can also be received by a computer.
Some devices can be used for a number of purposes; for example a printer, scanner and photocopier can be combined as one physical device.

10.2 Ports
On the outside of a computer you will see a number of connection points that look like sockets. These sockets are known as ports and they provide connections between the computer and external devices such as a digital camera or printer. Ports control the flow of data between the computer and these devices, ensuring that data is sent and received quickly and reliably.
Modern ICT devices require increasingly large amounts of data to be sent between the computer and the devices. Therefore, it is important that the ports provide a high-speed connection. Two high-speed ports currently available are Firewire and Universal Serial Bus (USB). Firewire can provide a fast connection at a rate of up to 800 megabits per second (Mbps). USB ports come in two versions: USB 1.1 and the more recent USB 2.0. The latter is faster, at about 480 Mbps, while USB 1.1 is only 12 Mbps.
You may also find older types of ports on your computer, such as a serial port, which was often used for a modem, and a parallel port, used to connect the computer to a printer.
Activity 8 (self-assessment)
-
Which of these devices provide a means by which a computer can receive data from a user: keyboard, scanner, printer, monitor, mouse?
-
Which type of port provides a faster connection between a computer and an input or output device: Firewire or USB?
Answer
-
keyboard, scanner, mouse
-
Firewire.
11 Manipulating data
11.1 Introduction
A stand-alone computer needs two main components to manipulate data: a processor and a working memory.

11.2 The processor
The processor can be thought of as the 'brain' of the computer in that it manages everything the computer does. A processor is contained on a single microchip or 'chip'. A chip is a small, thin slice of silicon, which might measure only a centimetre across but can contain hundreds of millions of transistors. The transistors are joined together into circuits by tiny wires which can be more than a hundred times thinner than a human hair. These tiny circuits enable the processor to carry out calculations and other manipulations of data.
Processors can have different speeds, and this influences how quickly the computer can carry out its operations. Processor speeds seem to be increasing all the time. There are many different types of processor available: such as Pentium®, Celeron®, Athlon™, Centrino™ and PowerPC®.
11.3 Memory
An essential component of a computer is the memory which it uses to hold data currently being used by the processor. This is the random access memory (RAM), the computer's working memory in which programs and data are stored so that they can be accessed very quickly by the processor. The processor stores data in RAM and retrieves data from it as it carries out its manipulations. The more RAM a computer has, the faster the computer programs will run. RAM memory is used and reused and any data held in RAM is normally lost when the computer is turned off.
To ensure that essential data is not lost when the computer is switched off, all personal computers have a hard disk (sometimes called a hard drive) which can store data permanently. Part of the starting-up process of a computer is to copy start-up programs and data from the hard disk into the RAM, and all important data in the RAM is copied to the hard disk during the closing-down process. I'll discuss hard disks in more detail in Section 12.
There are other important components needed to make a modern computer work effectively, but the ones I've mentioned will suffice to illustrate the main ICT processes involved in a computing system.
11.4 Computer software
The electronic components and other equipment that make up your computer system are known as hardware. In order to make the computer do things, such as help you to produce your TMAs, edit photographs or draw diagrams, you also need computer programs, which are called software.
11.5 Programming languages
A computer program is written in a programming language and contains the instructions that tell the computer what to do. Developers write new software using specialised programming languages. The resulting programs (or 'source code') can be converted into the low-level instructions understood by the processor. There is a wide range of programming languages to suit different types of task; if you look at advertisements for programming jobs in newspapers or online you will get an idea of which languages are being widely used. Languages such as C++, Visual Basic and Java are in demand at the time of writing (early 2005).
Computer software falls into two main categories: operating systems and applications.
11.6 Operating systems
A computer requires software just to look after itself and to manage all its components; this is called the operating system. The operating system handles communication with the other software on the computer and with the hardware resources of the machine, such as the processor and memory. The operating system provides a means of running the computer's application programs. It also provides a standard user interface with windows, buttons and menus so that users can interact with the computer.
You are probably using a computer with the Microsoft Windows operating system, as required by the computer specification for this course. However, other operating systems can be used with personal computers. Apple Computer Inc. developed the Apple Macintosh OS system to run on Macintosh computers. Operating systems are usually commercial products and protected by copyright, but the Linux operating system is available free. Anyone can make improvements to Linux programs, provided they make the details of the programs available to other programmers. This is known as open source programming.
11.7 Applications
Most people buy computers in order to run applications. There are many different examples of software application, including word processors and spreadsheet, database and graphics packages. Some are combined together in 'office' suites, such as the StarOffice applications you can find on the Open University's Online Applications disk.
Word-processing software, such as Microsoft Word, allows you to create, edit and store documents. You can produce very professional-looking documents using a word processor, with different typefaces (known as 'fonts') and incorporating graphics, such as drawings and photographs.
Spreadsheet software, such as Excel, allows you to perform calculations based on the numbers and formulae that you enter. You can keep track of a household budget on a spreadsheet, but what makes a spreadsheet a powerful tool is its modelling ability. Depending on how a spreadsheet has been set up, when new values are entered, the whole spreadsheet can be automatically updated. Spreadsheets are often used in business organisations to model financial activities.
Database software, such as Microsoft Access, stores information in a form that can be organised and searched. Databases range in size and complexity. An example of a small database might be an address book that you keep on your own computer to store the names and contact details of friends and family. There are much larger databases in use by institutions containing specific types of information, such as library catalogues, banks' records of customers' accounts, and hospital medical records.
Graphics and image editing software allows you to create and edit drawings and images. Digital photography has become very popular and image-editing software allows you to crop and resize your photos, touch-up blemishes and then print the results.

Education and training software is intended to help children and adults learn. There are a number of programs intended to teach children basic mathematics and English skills. Other examples include programs designed to train people in computer skills or to help them learn new languages.
Games represent a large sector in the computer software market. While many run on dedicated game consoles rather than PCs, some make use of the PC's computing power to achieve high-quality graphics and complex game play. In fact, technological developments for games have resulted in improvements for personal computers. You can play games alone on your PC, but others provide multi-player environments via the internet.
Email software manages your electronic mailbox on your computer to allow you to compose, send, read and delete messages. Email applications often include tools such as a filing system for storing messages, a calendar and an address book.
Web browser software allows you to view web pages and, among other things, use the links in them to 'jump' from one page to another and from one part of a page to another. The two most popular browsers at the time of writing are Microsoft Internet Explorer and Mozilla Firefox.
There are also other applications which provide a means of sending and receiving data. For example, screen readers 'read' the accessible text aloud, while speech recognition software enables the computer to respond to the human voice.
12 Storing data
12.1 Introduction
Data must be stored somewhere when it is not being manipulated. Modern ICT systems require increasingly large amounts of data to be stored for later use, and it is important that the data can be accessed quickly. Data may be stored on the stand-alone computer's hard disk in the form of files.
You may want to move files from one stand-alone computer to another. In addition, you may want to move files from a device, such as a digital camera, to a computer. These activities require some form of external storage.
I'll introduce you to some different storage media in this section. However, I'll first explain the units in which we measure how much data is being stored.
12.2 Bytes of data
You will recall from Section 6.2 that a binary digit, or bit, can have one of two values: either a 0 or a 1. In a computer, bits are assembled into groups of eight, and a group of eight bits is known as a byte. The abbreviation used for a byte is B, so 512 bytes would be written as 512 B. Although this course will use 'b' for bit and 'B' for byte, you should be aware that not everyone makes this clear distinction.
A byte of data can represent many different things in a computer. For example, a byte can represent a text character, like the letter 'a', or a number, or a space or a punctuation mark. Just to give you an idea of what this means, the phrase 'storage technology' would require 18 bytes of storage space (there are 18 characters: 17 letters and one space).
Activity 9 (self-assessment)
How many bytes would be needed to store the following phrase? information and communication technologies
Answer
11 + 3 + 13 + 12 for the letters in the words + 3 for the spaces=42 bytes.
The capacity of computer RAM is measured in bytes. A computer may. for example, have 512 megabytes of RAM. From our discussion in Section 6.2, you might expect this to be 512 million bytes. Unfortunately, things are not quite so simple. For memory and file sizes, a megabyte is 1 048 576 bytes, not 1 000 000 bytes! Similarly, a kilobyte is 1024 bytes, not 1000, and gigabyte means 1 073 741 824 bytes, not 1 000 000 000. These numbers are all 'powers of 2', which means 2 multiplied by itself a number of times. Probably no one would choose to define memory and file sizes in this way if they were starting over again today, but there are historical reasons why sizes were originally defined in this way.
As Table 2 shows, an upper-case K should be used for 'kilo' when it means 1024. This is in contrast with the lower-case k you met earlier in relation to data rates, where 'kilo' meant 1000 (see Table 1). Unfortunately not everyone sticks to this rule, and there is no such distinction made for the two versions of 'mega' and 'giga'. For these prefixes upper-case M and G are always used.
| Prefix | In figures this is: | This is approximately: | Symbol |
|---|---|---|---|
| kilo | 1024 | A thousand | K |
| mega | 1 048 576 | A million | M |
| giga | 1 073 741 824 | A billion (a thousand million) | G |
The golden rule is: kilo, mega and giga have the meanings in Table 2 if they refer to memory or file sizes; if they refer to data rates then kilo, mega and giga have the meanings given in Table 1.
Activity 10 (self-assessment)
If a kilobyte is 1024 bytes of data, how many bits of data does this represent?
Answer
There are 8 bits in a byte, and 'kilo' here means 1024. So a kilobyte is 1024×8=8192 bits.
13 Different types of storage
13.1 Introduction
I'll now introduce you to some different storage media and devices. As the uses for ICTs have expanded and developed, so has the need to store ever larger amounts of data. I've quoted some figures for storage capacity in this section but, given the rapid rate of development in ICT systems, some of these figures may be out of date when you read this course.

13.2 Magnetic storage
As I mentioned earlier, your computer has a hard disk which provides a permanent storage area for your computer's programs and the files you create. When you save files to your computer's hard disk, you are using a magnetic storage medium. Data stored in magnetic form can be changed once it has been stored, so if you run out of space you can delete some files to make room or, if you want to edit a file, you can make the necessary changes and then save it again. At the time of writing, a medium-priced computer has a storage capacity of up to 100 GB. A floppy disk can store about 1.44 MB, but this type of storage has largely been replaced by new storage media with larger capacities. A zip disk is a high capacity form of magnetic storage which is portable. Zip disks are available in capacities of 100 MB, 240 MB and 750 MB.
13.3 Optical storage
A CD-ROM (Compact Disk Read Only Memory) uses a laser-based optical form of storage. This type of disk has been used for many years to distribute music and computer software. A CD-ROM drive is needed to read the disks. Data is locked into the disk during manufacture, and cannot afterwards be changed.
There are two other types of CD device for computers: CD-R (CD-recordable) and CD-RW (CD-rewritable). With the right sort of CD drive in your computer, you can 'burn' data (that is, write data) to either type. Data written to a CD-R disk cannot be changed afterwards, although further data can be added. Data written to a CD-RW disk can be erased and the disk reused.
CD-ROMs can store up to 800 MB of data, 90 minutes of audio or 60 minutes of video. CD-R and CD-RW disks vary in their capacity, but typically it is in the region of 700 MB.
DVD (Digital Versatile Disk) works in a similar way to CDs, but the data is held in a more compact format. In addition, DVDs can have more than one layer of data. A single data layer can hold about 4.4 GB. At the highest quality, roughly two hours of video can be held in a layer, and with reduced quality about three hours. As with CDs, there are 'R' and 'RW versions to which the user can write data. The 'Blu Ray' system, using a blue laser (instead of a red one), stores data even more compactly. This system promises to increase the capacity of a layer to 27 GB.

13.4 Flash memory
Flash memory is an electronic form of memory which can be used, erased and reused. A flash memory card is a small storage device used to store data such as text, pictures, sound and video. These cards are used in portable devices such as digital cameras and in small portable computers, such as Personal Digital Assistants (PDAs).
A USB flash memory, sometimes called a 'memory stick', is a small storage device which is completely external and connects to the computer via a USB port. This portable memory comes in different capacities, e.g. 256 MB, 512 MB, 1 GB and 2 GB.
Activity 11 (self-assessment)
Are these statements about storage true or false? Mark each one with a 'T' for true or 'F' for false.
-
The hard disk in a computer is used to store data.
-
The storage capacity of a floppy disk is several gigabytes!
-
Data files that you want to update regularly should be stored onl CD-R optical disk.
-
A DVD is a form of magnetic storage!
-
A USB memory stick holds much more than a floppy disk.
Answer
-
T
-
F
-
F
-
F
-
T
14 Networked computers
14.1 Introduction
Now that I have introduced you to the processes carried out by a stand-alone computer, I will move on to discuss what happens when computers are linked.

14.2 Modelling networked computers
You met a block diagram showing a model of a communication system in Figure 8. In this model, a transmitter sends data into a network which conveys it to a receiver; but how does this model work when the transmitter and receiver are computers?
Sometimes the computer's user is communicating with another computer user, (for example when using an online 'chat' system). In that case we can consider the users and their linked computers as forming a communication system similar to that shown in Figure 8.
Sometimes, however, the computer's user is communicating with another computer (for example, when browsing a website). Figure 11 models that situation; the blocks are 'user', 'computer', 'network' and then another 'computer'.
To explore the model shown in Figure 11, I'll use the example of sending a message from your computer at home to an Oepn University FirstClass conference. FirstClass is the system used by the Open University to enable registered students to communicate online with teaching staff and fellow students by email and take part in online conferencing.
4.2.1 First computer (your computer)
In the block diagram, the computer receives data from the user and sends it into the network. It will manipulate and also store and retrieve data.
If you send a message to a FirstClass conference, your computer receives the message from you as data via the keyboard. The computer manipulates the data into a form that can be sent into the network, in this case the internet via your internet service provider (ISP). Your computer will also store or retrieve relevant data, such as details of the FirstClass computer's internet address.

4.2.2 Network
In the same way as in the network shown in Figure 8, this network conveys the data to the receiver, selecting the most appropriate route for it to travel. In order to do this, the network may need to manipulate and store or retrieve data.
Your computer sends the FirstClass message into the internet, via your ISP connection, and the internet conveys the message to its destination, which is a computer at The Open University. The devices which make up the internet work together to select the most appropriate route for conveying the message. The internet is very complex so this will involve manipulating, retrieving and possibly storing data on the way.
4.2.3 Second computer (the FirstClass server)
The computer on the right of Figure 11 receives the data, manipulates it and then stores it. The computer then typically sends some kind of response back via the network, which may require the computer to retrieve some stored data.
The computer in this example is one of the Open University's FirstClass servers. A server is a computer whose hardware and software is dedicated to making data available to other computers. The FirstClass server receives the data from the network and stores it. It carries out the manipulations necessary to add your message to those already in the conference, retrieving other details about the conference as it does so. It also sends data back to you, showing you that your message is now in the conference.
14.3 Personal Digital Assistants
Personal Digital Assistants (PDAs) or handheld computers are small, portable computers. They each contain a small processor and have specially written operating systems. Two popular types of PDA at the time of writing (early 2005) are those running the Palm OS operating system and those using the Windows Mobile operating system, (also called Pocket PC). There is a range of applications purposely written for PDAs, but many also use special versions of popular applications like Microsoft Word, Excel and Outlook.
Some PDAs have very small keyboards to input data, whilst others use touch screens which can be tapped with a finger or a stylus. Many can accommodate flash memory cards to increase space for data storage. Many PDAs can be used to view digital photographs or sometimes video, and can be used to play music in MP3 format. Some PDAs even have integral digital cameras.
PDAs are designed to connect with personal computers and other PDAs to transfer data between them using a range of communication links, such as Bluetooth and infrared. At the more expensive end of the range, some PDAs have built-in mobile phones and can connect to the internet to send and receive email.
Activity 12 (self-assessment)
This activity is intended to help you consolidate your learning from sections 8–14 and give you some practice in working with the technological content of an article. The article in the attached pdf (Revel, 2004) illustrates the way PDAs, an example of an ICT system, can be used in education.
You should read this article and then answer the following questions.
-
How can a child input data to his or her own PDA?
-
How is data conveyed between PDAs?
-
How does the PDA output data to the child?
-
Give an example from the article of how the PDA manipulates data.
Note: In case you're not familiar with it, the National Grid for Learning is (at the time of writing) a government initiative in the UK that provides a network of educational resources on the internet. These resources are available for use by children, parents and teachers as well as librarians and those involved in adult education.
Click on the 'view document' link below to read Phil Revell's 'Miniature Computers Are Adding Up To Fun'
Answer
-
The PDA has a digital camera for images, a voice recorder for sound, a touch screen and 'Graffiti' software which converts handwriting to text.
-
The article mentions infrared and Bluetooth as the means by which data is 'beamed' between PDAs.
-
The article mentions a screen and headphones.
-
This process is a little less obvious than the others. The examples I came up with are:
-
some children are playing noughts and crosses, which involves manipulation of images on the screen;
-
the children incorporate pictures and text in their stories, which involves the manipulation of graphical and textual data;
-
the children's handwriting is converted into text using the 'Graffiti' software;
-
a maths program is mentioned;
-
the children play music, which involves manipulating sound files.
-
15 Computers and communication systems working together
The combination of communication systems and computers has produced powerful new systems not possible when these technologies are used separately. In section 15–19, I'll be using an ICT system in a supermarket as an example, as it is something that you have probably experienced. The material in this study session is not intended to be a comprehensive examination of how ICT systems are used in supermarkets; I'll just be focusing on some of the supermarket's activities in order to highlight the ICT processes involved.
16 ICT systems in a supermarket
16.1 Introduction
Supermarkets make use of ICT systems for a range of purposes. In the following sections, we'll look at the processes of receiving, storing, retrieving, manipulating and sending data at the checkout, and then we'll move on to the larger context of the supermarket.

16.2 Processes at the checkout
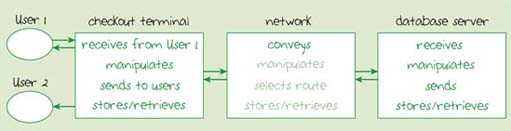
From the point of view of the customer and the checkout operator, a supermarket's ICT system is like the stand-alone computer you saw in Figure 10 in Section 9. The system map in Figure 12 represents this view. The boundary of the system has been drawn tightly, so that we can focus on the important processes being carried out at the checkout. I've called the system the 'checkout system' and there are three components: the customer, the checkout operator and the checkout terminal.
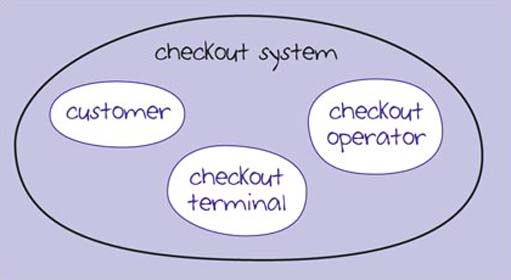
Figure 12
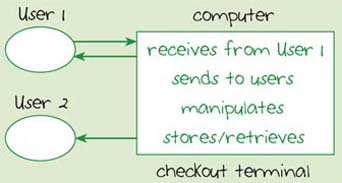
I've also adapted the diagram of the stand-alone computer you saw in Figure 10 to show the checkout system as a block diagram (Figure 13). The computer is now the checkout terminal. However, there is an important difference between the two diagrams in that this computer has two users, the checkout operator (User 1) and the customer (User 2). The reason for this should become clearer as we discuss the processes involved at the checkout.
16.2.1 Receiving data
In a supermarket ICT system, there needs to be some way for the computer to receive information about the items a customer is buying.
Activity 13 (exploratory)
Think back to a recent visit to your local supermarket and how you made your purchases at the checkout. How did the checkout operator input information about your purchases?
Discussion
This probably involved the checkout operator using a bar code reader to scan the bar code printed on the label of each of your purchases. If an item doesn't have a bar code or, if for some reason, the bar code can't be read, the checkout operator has a keypad for entering the data.
A bar code is a pattern of narrow and wide stripes which can be read by a machine. A bar code reader is a device which optically scans the bar code and converts the stripes into numerical data which can be automatically input to the checkout computer.
16.2.2 Storing and retrieving data
As each item is scanned, the checkout computer looks up its price. The running total for each customer's purchases is stored temporarily in the checkout terminal. Other data may also be stored, such as the amount of money that has been taken at that checkout during the day.
16.2.3 Manipulating data
Once all items have been scanned, the checkout computer manipulates the data to produce the total cost. If you are paying with cash and require change, the checkout operator will enter the amount you have tendered (an example of the computer receiving data from the user) and the computer will calculate any change required.
16.2.4 Sending data
As the items are scanned into the checkout computer, information about the price of each item may be shown on a small display so that the customer can see the price. Sometimes there is a beep as each item passes the bar code reader, to tell the checkout operator the item has been identified. Once all the items have been scanned, the total amount is displayed. Once the customer has paid, they are given a printed till receipt which shows all the items purchased, the price of each and total expenditure.
Activity 14 (self-assessment)
In Table 3 I have listed some of the different activities carried out at the checkout. Match each of these with one of the ICT processes associated with a stand-alone computer: receives, sends, stores, retrieves and manipulates.
I've completed the first as an example.
| Activity | Process | |
|---|---|---|
| 1 | Scanning a bar code | Receives |
| 2 | Providing a receipt | |
| 3 | Calculating total cost of items purchased | |
| 4 | Subtracting the total cost from money tendered by the customer |
Answer
-
Receives – the checkout terminal receives data from the bar code scanner.
-
Sends – the checkout terminal sends data to the user.
-
Manipulates – the checkout terminal manipulates the data to obtain the total cost.
-
Manipulates – the checkout terminal manipulates the data to obtain by subtraction the amount of change required.
16.3 Networked computers in the supermarket checkout system
All these processes are very helpful for the purposes of dealing with an individual customer's purchases. However, when computers are linked in a network, many new uses are possible.
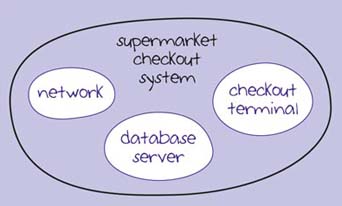
Now, I am going to draw a different system boundary. The components of this supermarket checkout system are the checkout terminal, the network and the database server. A database server is used to make the data in databases available to other computers on the network, and therefore to users. You met a specialised form of database server in Section 14.2: the FirstClass server. In the following sections, I'll focus on the network first and then look at the database server.
The system map for the supermarket checkout system is shown in Figure 14. You might be wondering about the users of the system: the customer and the checkout operator. For the time being, we are focusing on the computers and network, rather than thinking about the end users, so in this system map they are not shown.
16.4 The network
The term 'network' is used to describe some very different interconnected systems. In a home setting, you might have just two computers linked together to share documents and devices (such as a printer and a scanner) and to use the same internet connection. This setup is a network, albeit a small one. At the other end of the scale is a multinational company with a network of computers distributed all over the world.
A network belonging to a single organisation, where the computers are close to each other on a single site, is known as a Local Area Network or LAN. In a Wide Area Network, or WAN, the computers may be spread over a large geographic area such as a city, a country, or even across continents. The computers in a WAN are usually linked via private communication links leased by the organisation.
When your computer is connected to a network, you have access to network resources such as shared printers and software, and to data and possibly storage space on other computers. A network can also support email and other communication services for its users.
The checkout terminals in a supermarket will almost certainly be linked to each other in a LAN within the building. There will probably also be links to other networks within the supermarket organisation. For example, there will be links to a network at the head office which may be many hundreds of miles away.
Activity 15 (exploratory)
Have another look at what you have just read about networks. Write two or three sentences to explain the advantages of networked computers.
Discussion
You may have mentioned advantages such as sharing documents, devices and an internet connection in a small-scale network. In a larger network, resources such as software applications, data and printers could be shared, and access provided to an email service.
16.5 The database server
A database is used to store data in a form that can be organised and searched. A supermarket may use a number of different databases in order to carry out its activities. I'll now discuss two examples of database use: firstly, pricing and stock control and secondly, loyalty cards. I'll use these examples to illustrate how data is manipulated in a supermarket ICT system.

16.6 Pricing and stock control
A supermarket has a large database of information about its goods, such as the name, price, size and quantity held in stock.
If the price of a particular item changes, the relevant data in the supermarket's database can be easily updated. When the bar code for an item is scanned, the checkout computer searches the database for the item and retrieves the new price. Because the checkout computers are networked, they all use the same data on the database server, so it is not necessary to change prices on individual checkout computers.
Once goods have been sold in a branch, the database is updated. If, for example, you buy a box of your favourite breakfast cereal, the entry in the database for that particular item is decreased by one. When stock levels are getting low, the supermarket can quickly restock its shelves and reorder goods where necessary. The database can then be updated with the new stock levels.
Data about your purchases, and other people's, can be stored in the database and manipulated so that the supermarket knows what sort of goods people buy in that particular branch. The supermarket's management team can use this information in making decisions about which products to stock.
16.7 A loyalty card scheme
Supermarkets, and other types of retailer, use loyalty cards to encourage customers to use their particular shops. Points are awarded when a customer spends money in the shop. Supermarkets 'reward' their customers by converting loyalty card points into vouchers. They may also give them discount vouchers for a range of products.
Supermarkets use their loyalty card schemes to collect data about their customers. Data about each customer is held in a large database where each customer is identified by a unique number. This number is stored in a magnetic strip on the back of the customer's loyalty card.
When the customer presents their loyalty card at the checkout, it will be 'swiped' through a card reader to capture data from the magnetic strip. The number in the magnetic strip is read, allowing the customer to be identified. Points are added to the customer's loyalty points account once all shopping purchases have been entered into the computer.
Activity 16 (exploratory)
What personal data might the supermarket want to hold about you?
Discussion
The supermarket might want to hold basic data such as your name and address so that you can receive vouchers and other promotional material. Some supermarkets also ask for other personal information such as your telephone number, mobile number and email address.
16.8 Linking data
We now have two sets of data held by the supermarket: the data about its own products and the personal data about customers. Individually, each of these two sets of information has important uses. However, when they are linked, they provide a very powerful tool for the supermarket.
The personal data from a loyalty card scheme can be used to compile targeted mailing lists, because data about your purchases can help build up a profile of how you spend your money. For example, the supermarket knows from data held about your spending patterns whether you buy products for babies, children or pets, and whether you prefer particular brands. This information allows the supermarket to send you appropriate information and special offers.
The mailing lists that supermarkets gather from loyalty card schemes may also be sold to other businesses. However, in the UK the Data Protection Act (1998) applies to the personal data gathered by loyalty card schemes, which means that customers must be asked for permission to use information about them.
16.9 Identity in an ICT system
In a supermarket we might see the following data on an item: 5018190009067. On their own, the digits do not mean very much, but these numbers are typical of the type of data input to a computer system. In this instance, they are numbers from a bar code on a jar of coffee. I have described the numbers here as 'data' because in themselves they do not really tell us anything.
When the bar code is moved past a bar code reader at a checkout counter, the checkout terminal will display details on the screen, such as these:
Café Direct coffee, 100 g
This is information which can be used by a person.
In this example, we see that the bar code 5018190009067 refers to a 100-gram jar of Café Direct coffee. We can say that the bar code identifies the jar of coffee in the supermarket's database. However, the bar code doesn't give a unique identity to the individual jar of coffee, only to this particular category of item.
Activity 17 (exploratory)
It would be important that any points I earned by shopping at a particular supermarket were assigned to me and not to someone else. In the supermarket loyalty card scheme, what is it that uniquely identifies a customer?
Discussion
A customer could be identified by his or her name, but this is not unique as there may be many people with the same name using the supermarket's branches. Therefore, the supermarket chain needs to use a unique customer identification number, which is stored on the card and in the database.
A unique identifier is normally used for individual people and things in an ICT system. For people this is often a number, such as the Personal Identification Number (PIN) which may be used to identify individual customers in a loyalty card system. A unique identifier may also be a combination of letters and numbers, such as your Open University Personal ID.
Radio Frequency Identity (RFID) technology provides a means of identifying individual items. This contrasts with the bar code system, which identifies only categories of items (such as all 100-gram jars of Cafe Direct coffee). Each tag is unique so that each item, whether it is a razor blade or an item of clothing, can be tracked individually.
An RFID tag works in conjunction with a device called an RFID reader. In response to a signal from the reader, the tag transmits data to the reader using a radio link. The data could be just an identification number, which is then used to look up further data in a database. Alternatively, the tag itself could hold details such as price, colour, packaging and expiry date.
This technology has now been brought to some supermarkets. There are a number of attractions for supermarkets in using RFID technology. As the tags can be tracked by RFID readers, there is no need to scan items at the checkout. RFID technology can be used to set up 'smart shelves' that can sense when products are running low, enabling the supermarket to keep track of stock levels.
17 Taking an overview of ICT systems
17.1 Introduction
I'm going to pause here to try to put together some of the ideas we have encountered so far. I deliberately chose the example of a supermarket to illustrate some of the key processes involved in an ICT system. Figure 15 is a modified version of the block diagram for computers in a network (Figure 11). I have changed the labels in order to represent the networked computers in a supermarket. I have also added the second user, as in Figure 13. I'll now take each block of the diagram in Figure 15 in turn and examine what is involved. This is a 'walkthrough' of the networked computer system and it will help us to highlight the important processes that take place in each block.
17.2 The checkout terminal
The first computer block represents the checkout terminal. The processes at the checkout (receiving, storing, retrieving, manipulating and sending data to the user), are the same as I described earlier. However, the checkout terminal also sends data via the supermarket's network.

17.3 The network
The network conveys the data on items purchased through to the database server. It also conveys data such as revised prices and special offers from the database server back to the checkout terminal. In both cases this may involve selecting an appropriate route through the network and manipulating, storing or retrieving data.
17.4 The database server
The computer block on the right represents the database server, which is dedicated to managing a database and making the data available to other computers in the network. The database server receives data via the network. It stores, retrieves and manipulates data, for example by retrieving your previous points total and adding to it the number of points you have 'earned' on this visit. This data is also sent back via the network to the checkout computer to show you the total number of points you have accumulated.
Clearly, Figure 15 shows a very simplified version of the supermarket's ICT system. For example, a supermarket is likely to have many more checkout terminals, and there will be at least one computer for use by the manager and office staff.
Figure 16 shows a block diagram of a more comprehensive ICT system for a supermarket. This may look complex, but you will see that it can be built up from the smaller systems that we have been considering. As Figure 16 shows, each of the supermarket's branches has a number of checkout terminals and at least one 'back office' computer. These computers are linked via a network to each other and to the supermarket's database server, which will probably be located in the head office.
This type of system will be replicated in each branch throughout the supermarket chain. There may also be regional warehouses with their own networked systems to supply the branches, and there will be a networked system in the head office to assist in the management of the whole supermarket chain. All these networks will be linked together.
Treating a system as being composed of different subsystems has enabled us to deal with a complex ICT system in a supermarket. Our system maps have helped us to deal with complexity by drawing the system boundary so that we can investigate a particular subsystem. In this way, we can 'look into' a specific part of a complex system.
In this section, we started by considering a system with one checkout terminal and looked at the processes involved. We then expanded our view of the system to include one checkout networked to a database server. Lastly, we looked at a number of checkouts and the 'backroom' computers networked to the database server. As you may have gathered, we could go even further and look at all the supermarket branches, warehouses and head office networked together.
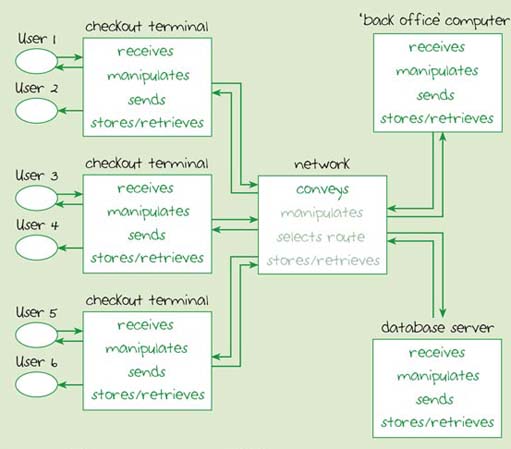
Figure 16
In the next section we will look at another way of using ICTs for shopping – electronic commerce.
18 Electronic commerce
18.1 Introduction
Most supermarkets now have an online ICT system which allows customers to select and purchase goods from the supermarket's website. Goods are then delivered to the customer's home. Buying and selling things using the internet is known as 'electronic commerce', often shortened to e-commerce.

18.2 Using e-commerce
Many people now have internet connections and this offers many benefits to both businesses and their customers.
From a customer's point of view, e-commerce has a number of advantages. Shopping can be done from home; you can probably find what you need without trudging from one shop to another and waiting in queues. You can also purchase goods 24 hours a day, every day.
From the point of view of a business, e-commerce also offers a number of advantages. There is a potentially wide customer base. Setting up a website and using it to do business can be more cost effective than using a conventional shop. There are fewer overheads in terms of, for example, heating, lighting and staffing. The costs of delivering goods are relatively low compared with those of running a shop. Businesses can use the Web to reach customers on a national or even international basis, rather than being confined to a shop's geographic location. The Web creates a more level playing-field in that smaller companies can compete against larger companies.
However, e-commerce works well only if the company has a good warehouse system and access to an effective distribution system. The company must have the goods in its warehouse in sufficient quantities and at the right time in order to meet its customers' orders. The company must also ensure that the goods can be conveyed to the customer as quickly as possible, which may involve using couriers and other special delivery services.
In many ways, the ICT system used in an online operation is very similar to that of a conventional supermarket. There are users' computers, networks and database servers. There are also web servers, which are computers that hold web pages and make them available to users over the internet.
Shopping online typically involves:
-
browsing an online catalogue, accessible from the organisation's web server;
-
adding a product to a virtual shopping basket;
-
going to a virtual checkout when you have completed your selections;
-
paying for the goods using a credit card or using a special system, such as PayPal.
Activity 18 (exploratory)
What concerns might a customer have about shopping online? Try to compare online shopping with face-to-face shopping.
Discussion
These are some concerns I have about online shopping. There may be security worries about using a credit or debit card in the transaction. How secure is the payment system? I might be concerned about whether the seller is genuine and reliable. I do not have an opportunity to examine the goods before I purchase them, so they might turn out to be unsuitable. I might have to arrange to be home in order to receive the goods. I might worry that the goods will not arrive on time (or not arrive at all!)
Activity 19 is intended to help you consolidate your learning for this section. Don't worry if you find this activity a challenge. What's important is that you have a go at applying what you've learnt to a different situation.
Activity 19 (self-assessment)
Think about the way you use your own computer to get information about goods and services from the Web. For example, you may have visited a shopping website to look at their online catalogue.
-
Figures 8, 10, and 11 each present a model of a different sort of ICT system. Which of these diagrams best models the situation where you are visiting an online shopping site? When you have decided, compare your answer with mine, before moving on to (b).
-
Complete the following 'walkthrough' of an online shopping ICT system to find examples of the processes involved; imagine you are already logged onto the internet, and you start by typing in the web address of the shopping site you wish to visit:
Data is received by my computer from me, the user, when I type the web address using the keyboard. My computer manipulates the data for my request into a suitable form …
Answer
-
Figure 11 best models this situation. The computer on the left would be my PC, the network is the internet and the computer on the right is the shopping organisation's server. (The organisation's web server and database server would probably be separate computers, but for the purposes of this activity you can assume that there is a single computer which acts as both.)
-
This is how I completed the walkthrough. Don't worry if what you've written is a bit different – what is important is that you have the same basic ideas.
-
Data is received by my computer from me, the user, when I type the web address using the keyboard. My computer manipulates the data for my request into a suitable form and then sends it into the internet. Data is also sent to me, the user, by displaying the web address on my computer's screen.
-
The internet selects a route and conveys the data for my request to the shopping website. The devices in the internet may need to manipulate, store or retrieve data as part of this process.
-
The online shopping organisation's server receives my request. It then retrieves the requested data, carries out some manipulation on it and sends it into the internet.
-
The internet conveys this data to my computer, where it may be stored on my computer's hard disk and will be sent to me by displaying the web page on my computer screen.
-
19 Conclusion
In sections 15–18, we examined the components and processes of an ICT system that is used for an everyday activity: shopping. We started by looking at a system map of the 'checkout system' before exploring the processes involved at the checkout. We considered some examples of networks and discussed the processes involved in a networked supermarket ICT system. Finally, we looked briefly at another way in which ICT systems can be used for shopping: e-commerce.

References
Acknowledgements
Except for third party materials and otherwise stated (see terms and conditions). This content is made available under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 Licence
Cover image: Karen Blaha in Flickr made available under Creative Commons Attribution-NonCommercial-ShareAlike 2.0 Licence.
Revell, P., 'Miniature computers are adding up to fun', Guardian Online, accessed 16 October 2006, © 2005 Phil Revell,Journeys Magazine
Don't miss out:
If reading this text has inspired you to learn more, you may be interested in joining the millions of people who discover our free learning resources and qualifications by visiting The Open University - www.open.edu/ openlearn/ free-courses
Copyright © 2016 The Open University