1.1 Plaintext and ciphertext
This section is part of the amber and green pathways.

As in previous weeks, there is some terminology we need to introduce:
- plaintext – information that can be directly read by humans or a machine (this article is an example of plaintext). Plaintext is a historic term pre-dating computers, when encryption was only used for hardcopy text, nowadays it is associated with many formats including music, movies and computer programs
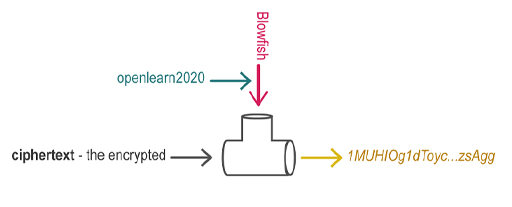
- ciphertext – the encrypted data
- a cipher – the mathematics (or algorithm) responsible for turning plaintext into ciphertext and reverting ciphertext to plaintext (you might also see the word ‘code’ used – there is a technical difference between the two but it need not concern us now)
- encryption – the process of converting plaintext to ciphertext (occasionally you may see it called ‘encipherment’)
- decryption – the process of reverting ciphertext to plaintext (occasionally ‘decipherment’).
Key = openlearn2020 Cipher = Blowfish |
|---|
Plain text: ciphertext – the encrypted data. Encrypted data is represented as a string of readable characters except that they are unintelligible |
Encrypted text: 1MUHIOg1dToyc/hDZDiRe8haDdQ82HjC7/bg7TRVIc8vahsGczll7is2wbxIAuYYDz4rNpwbLKArfrS3vjGGEcL5ZQvLqlQpVgq8TSXSDH/GWwWQ44QKEdSA3lzSl3Lsnl/gP9QsckF9uzVRMFFLvbe6xgGwG0YJvtWgtAnDKR2ZxsGvzXvbMevvQTJzsAgg |