1.1 What happens when you enter a password?
This section is part of the amber and green pathways.
Transcript
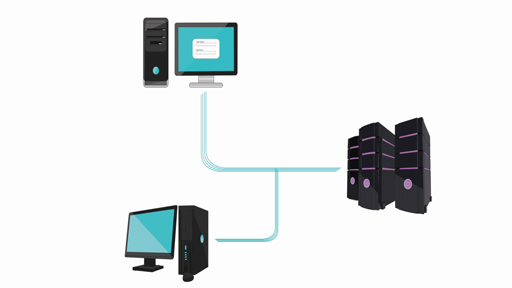
When a user enters a password it is sent to the server systems via a network (your broadband network, if you are home, or the mobile network). The server systems match the received password against the password stored by that website. If the passwords match, the user is granted access. Now, for a moment, think what would happen if your password was easily guessable!
There are a couple of potential weaknesses with this approach that you can probably recognise:
- The password is transmitted as plaintext (what you see is exactly what you get; it isn’t hidden in any way) – it could be intercepted as it travels across the network. You wouldn’t share secrets aloud, would you?
- The password is stored as plaintext – an attack on the server could not only reveal the user’s password, but all the passwords for all the users of the system. Similarly, the person in charge of the system would have access to the passwords and could use it maliciously.
The first problem is usually overcome by encrypting the communication between the user and the server. The most common form of encryption is the SSL standard (Secure Socket Layer). You’ll recognise that SSL is being used when you see ‘https’ at the beginning of a web page address instead of ‘http’, and by a padlock symbol in your browser. (You’ll look at encryption and SSL more fully in Week 4.)
The second problem can also be solved using a technique called hashing. A hash is the result of processing plaintext to create a unique, fixed length identifier – you’ll find out more in Week 5. It cannot be used to reconstruct the original data – even if the hash falls into hostile hands. In this scheme, a hashing function is used to create a hash of a password, which is stored on the server – the password itself is discarded. When the user enters a password, this is sent over the network and hashed on the server using a copy of the same hashing function. The resulting hash is compared to the hash stored on the password server. Only if they match will the user be granted access. Some implementations of this scheme will hash the user’s password before sending it across the network to be compared with the hash stored on the server.
The following table illustrates several different password strings of different lengths and their unique hash digests. Each digest is of a fixed length. These fixed length digests are stored on the system for authentication. (Note, these passwords are not good examples of passwords and are used for illustration only.)
| Password strings | Password hash digests stored on the system | |
|---|---|---|
| 1 | RainRainBrainDrain | 6b2a 8ff0 a43e 4848 f8cf 9d2f e413 06ab |
| 2 | Unguessable Password | c786 a46d 5c85 caed 4401 3a12 3a61 809e |
| 3 | secret pass phrases make good passwords | c5ef be64 6d8a 4c5f 3d2c 3474 d75b a4e6 |
| 4 | May151995 - bad password | 24d9 da96 0f48 42ef 023d 82b5 5d17 aec7 |
| 5 | Hashing computes a digest of a string using a hashing algorithm. There are several hashing algorithms. | adb7 08cd 39a0 c120 e40a 7a9e 2a16 42a6 |
Almost all online services and computer systems store passwords as hashes – but surprisingly, errors still happen. The problems described in the following case study could have been avoided if hashing had been used.
Case study: Zynga
The mobile game company Zynga, creator of Farmville, suffered a major data breach in 2019 when user information from 218 million user accounts was accessed.
Zynga confirmed that email addresses, hashed passwords, phone numbers, and user IDs for Facebook and Zynga accounts were stolen. The information was stolen from accessing the databases of ‘Draw Something’ and ‘Words with Friends’ players and then gaining access to the user information. Information from up to 170 million accounts was reportedly that of users on a platform ‘OMGPOP’ that went out of production in 2013. Plaintext passwords of seven million former users of OMGPOP were available to attackers.
It is expected that the attackers will use the information to compromise user accounts on other services. They would predominantly use the information to contact users with phishing emails, making it appear as if it came from Zynga. The breach was engineered by a user/agency named ‘Gnosticplayers’.
Even when hashing and encrypted communications are used, there are still ways in which attackers can successfully learn your password.
Over the years many billions of accounts have been breached and the data collected by criminals. These criminals then try the same user name and password on other accounts. If you have reused the same password then they may take over your account.
In 2016, a list of 593 million unique email addresses together with multiple passwords for each address was being circulated by criminals. This list was known as ‘Exploit.In’
You can check to see if your own email has been part of a data breach by visiting https://haveibeenpwned.com/ [Tip: hold Ctrl and click a link to open it in a new tab. (Hide tip)] . Later this week you will look at how to improve your password security.
Even when hashing and encrypted communications are used, there are still ways in which attackers can successfully learn your password.