3.5 Sandboxes and code signing
This section is part of the amber pathway.
In addition to keeping software up to date and using antivirus products, there are other technological innovations that can help mitigate the threats of malware.
Sandboxes and code signing are examples of some of the technologies that developers are integrating into the software we commonly use to help protect our computers.
Sandboxes ensure that the programs operate/execute in a limited resource environment, limiting the typical malware characteristic of resource probing and use. In contrast, code signing is a means for users to validate the integrity of program code or a software distribution (such as a software update or a new release) released for download. The signature (hash digest – recall what was done for passwords) of the software is also available, so the users can check the integrity and authenticity of the software before using it.
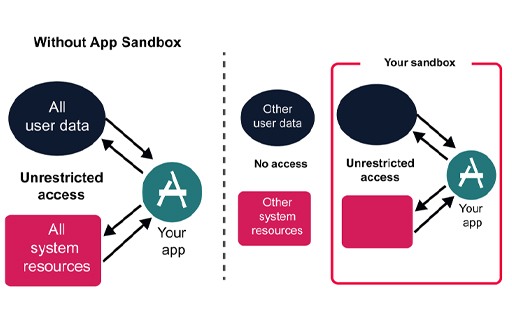
Sandboxes
A software sandbox is a way for computers to run programs in a controlled environment. The sandbox offers a constrained amount of memory and only allows very limited access to resources such as operating system files, disks and the network. In theory, the software cannot break out of the sandbox and affect other parts of the computer, so even if malicious software attempts to overwrite parts of the disk, the sandbox will prevent it from doing so.
Sandboxing is widely used in modern web browsers, such as Internet Explorer 10 onwards, and Chrome, to prevent internet content causing damage to files on the computer. Similar sandboxes exist for most browser plugins and the Adobe Acrobat PDF viewer.
Code signing
Code signing is a use of cryptography where software companies issue digitally signed copies of their programs that can be checked by recipients for its authenticity. You’ll discover more about digital signatures in Week 4.
Code signing is used by the designers of all three major operating systems (Microsoft Windows, Mac OS and Linux) to guarantee that operating system updates are genuine even if they are distributed using flash memory cards rather than directly from the publisher.
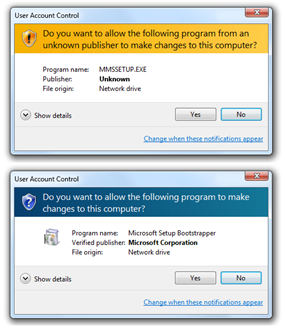
Microsoft Windows uses code signing on operating systems components, such as hardware drivers, which have direct access to the heart of the operating system. Apple has taken code signing even further. Versions of Mac OS from 10.8 onwards can restrict users to only running programs that have been certified by the Apple App Store. While this does offer greater security against malware, it may also restrict choice and prevent users from running certain unsigned apps from third parties.
Next, you have an opportunity to review what you’ve learned in the end-of-week practice test.