3.1 Introducing the TCP/IP protocols
This section is part of the amber and green pathways.
The standards that allow different networks and differing communications equipment to talk to one another are formalised in digital rules known as ‘communications protocols’.
For the internet the two most important are the Transmission Control Protocol (TCP), and the Internet Protocol (IP). They are so inextricably linked that they are often written together as TCP/IP.
TCP
The TCP protocol is responsible for ensuring data can be sent reliably over the internet. It works through a number of software ports that act to keep data separate on the same computer – so it is possible to browse a web page, collect email and listen to streaming music at the same time.
To understand how TCP works you need to know something about ports. A port can mean different things depending on the context. A port can be a physical connection on a device such as the USB port into which you plug your printer or flash drive. But for TCP, it means a number which indicates how data is handled when it reaches its destination. Many ports represent specific protocols such as port 80 representing the well-known port of HTTP.
Common TCP ports include the following:
- port 20 and 21 – File Transfer Protocol (FTP) for sending and receiving files (port 20) and control (port 21)
- port 22 – Secure Shell (SSH) for secure logins to computers
- port 25 – Simple Mail Transfer Protocol (SMTP) for sending email
- port 80 – HyperText Transfer Protocol (HTTP) for browsing web pages.
Data being sent from an application on your computer is divided into TCP segments each containing the TCP port number. The TCP application running on the recipient’s computer will then examine this port number to determine which application should receive the information in the segment.
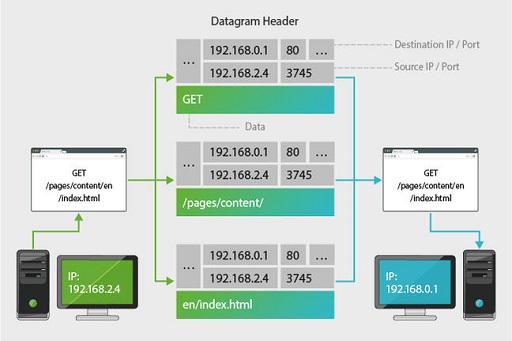
TCP’s second major task is ensuring that all data sent from a computer is received by its destination. It waits for acknowledgements from the remote computer, and in the event that a segment gets lost or damaged in transit, it can resend the missing segment. For this reason TCP is reliable – but relatively slow. (Note: each portion of data handled by TCP is called a ‘segment’. When these segments are passed down to the network, they are called ‘datagrams’.)
Applications where timeliness is more important than absolute accuracy – such as streaming media, video games and video conferencing – will use less reliable, but faster, protocols such as UDP (User Datagram Protocol) to send and receive their data. (Note: unlike in the case of TCP, each portion of data handled by UDP is called a datagram. This distinction is made due to the way TCP and UDP process the data.)
If you are receiving an email, you want the whole message to arrive with no gaps, but if you are streaming a TV programme, it doesn’t greatly matter if a few datagrams get lost.
TCP is not responsible for sending and receiving information; that is performed by a second protocol – most commonly, IP, that we will look at next.

