3 Intrusion detection system (IDS)
This section is part of the amber and green pathways.
So what happens when there’s an attack on a computer network? Chances are that you’ve seen a movie or TV programme where the administrators rush to their keyboards and frantically begin typing, lights flash, sirens sound – it’s all very exciting – but does anything like this happen in real life?
As you might suspect, the answer is, no, not really. Computer networks are regularly attacked, but the response is rarely as exciting as filmmakers would like you to believe.
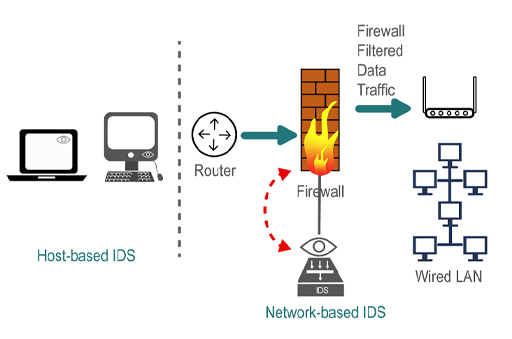
Intrusion detection systems (IDS) may be a dedicated device or software and are typically divided into two types depending on their responsibilities:
- Network Intrusion Detection System (NIDS), which is responsible for monitoring data passing over a network.
- Host Intrusion Detection System (HIDS), which is responsible for monitoring data to and from a computer.
An IDS can support a network firewall. Ideally the firewall should be closed to all traffic apart from that which is known to be needed by the organisation (such as web traffic, email and FTP). An IDS can then be used to scan any traffic passing through the firewall for potential attacks using a NIDS, as well as being able to detect those coming from within – such as from a personal computer infected with malware – using a HIDS.
Intrusion detection may be considered passive; it identifies that an intrusion is taking place and informs an administrator who must take appropriate action. However, they can also be reactive – as well as informing the administrator, the IDS can actively attempt to stop the intrusion, in most cases by blocking any further data packets sent by the source IP address. These systems are also referred to as an Intrusion Prevention or Protection System (IPS). The following table illustrates the functional differences between IDS and IPS. Notice where these devices are deployed.
| IDS | IPS | |
|---|---|---|
| Where in the network? | Supporting the firewall and with the capability of inspecting all the incoming and outgoing data traffic | Between the firewall and the router connecting to the internet |
| Operation | Passive – inspects the data traffic and alerts a companion device such a Firewall | Active – performs IPS functions and also blocks suspicious traffic from reaching the firewall |
| Detection | Anomaly detection – statistical anomaly, signature-based or rule-based, and misuse detection | Anomaly detection – statistical anomaly, signature-based or rule-based, and misuse detection |
Weaknesses
Automated intrusion detection systems have a number of weaknesses. They can be too sensitive, falsely reporting that an intrusion is under way, for example if a network is incorrectly configured or a buggy program begins issuing large numbers of packets.
Conversely, they are sometimes not sensitive enough to certain types of attack that proceed very slowly and do not generate enough traffic data to raise the alarm. Finally, signature IDS relies on the software suppliers issuing regular updates to the list of known signatures, until the IDS receives the update it is effectively blind to the attack.
How does a Firewall differ from an IPS?
The primary differences are in what they are purposed for. A firewall is an independent device that is positioned at the entry/exit point of the network. It inspects the IP datagrams and “filters” them based on a set of rules. These rules are configurable and can be changed as required. Based on the rules, the firewall either permits the IP datagrams access to the network it protects or it denies access to the network.
The following table illustrates the difference between a firewall and an IPS. Notice that the IPS is typically deployed between the internet router and the firewall. That way, it can block the data traffic it finds suspicious and prevent it from reaching the firewall.
| Firewall | IPS | |
|---|---|---|
| Where in the network? | At the perimeter of the network, before the internet router | Between the firewall and the router connecting to the internet |
| Operation | Active – inspects incoming IP datagrams and blocks or permits them through | Active – performs IPS functions and also blocks suspicious traffic from reaching the firewall |
| Detection | Rule-based blocking of IP datagrams based on source and destination addresses and service port numbers | Anomaly detection – statistical anomaly, signature-based or rule-based, and misuse detection |
| Integration | Firewalls deployed for small networks could have the IPS functionality integrated | Dedicated functionality |
In the next section you’ll learn how IDS works in practice.