1.2 Risk analysis
This section is part of the amber and green pathways.
We use the term ‘risk’ in everyday speech, but a whole science has grown up around the identification, analysis and management of risks. You will now look briefly at how to apply some of these ideas to identifying, assessing and reducing risks that affect the security of your information.
Risk can be thought of as the chance of adverse consequences or loss occurring. Generally, risks can be identified and the likelihood of them occurring assessed.
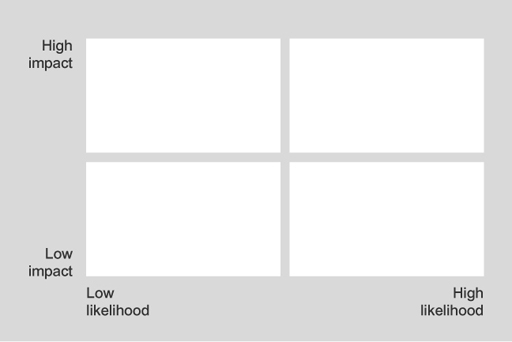
The main technique for a qualitative analysis of risk is to construct a likelihood–impact matrix in which the likelihood and impact of each risk event are assessed against a defined scale and then plotted on a two-dimensional grid. The position on the grid represents the relative significance of each risk. The simplest matrix is formed by classifying both likelihood and impact as either high or low, which leads to a 2 by 2 grid. This basic classification of a high or low value leads to the following rank order for tackling risks:
- high-impact, high-likelihood risks
- high-impact, low-likelihood risks
- low-impact, high-likelihood risks
- low impact, low-likelihood risks.
Low-impact, low-likelihood risks are probably not worth expending much effort on (but see the discussion of risk acceptance later this week). You can then look at these high-impact or high-likelihood risks one by one to determine whether there are ways either to reduce the impact if the risk occurs or to reduce the likelihood of the risk occurring, or both.
The next stage is to apply quantitative techniques, based on a financial assessment of the impact of each of the risks, to put the risks into order, with the greatest risks at the top of the list.
It is beyond the scope of this course to discuss these techniques. Sometimes it is hard to reach a decision about the importance of some risks until a corresponding response has been identified as well as any possible interactions between risk events and responses, so risk management is usually iterative in practice.
Next, you’ll do some risk analysis on your information.

