Week 3: Malware
Use 'Print preview' to check the number of pages and printer settings.
Print functionality varies between browsers.
Printable page generated Thursday, 5 February 2026, 9:46 AM
Week 3: Malware
Introduction

Transcript
The two biggest threats to consumers online are malware and phishing. Cory introduces you to malware, which is the focus of this week.
Malware is the collective name for software that has been designed to disrupt or damage data, software or hardware. There are several types of malware, such as viruses, worms and Trojans, which you’ll learn more about in the next few sections.
However, as malware has evolved from its beginnings as demonstrations of prowess by individual programmers to sophisticated technologies developed by organised crime, the boundaries between the different categories are beginning to blur.
1 Viruses
The best-known type of malware is probably the virus; although many pieces of malware are called viruses, they are nothing of the sort.
A virus is a piece of software that has been written to insert copies of itself into applications and data and onto crucial parts of a computer’s data storage systems (e.g. hard disks, memory sticks, etc.). Viruses are said to be self-replicating programs and date back as far as the early 1970s, but they only became well known with the advent of microcomputers and later, the internet.
Viruses attach themselves to specific applications on a computer and are activated when the program is first run. At that point, the virus may make a copy of itself on the hard disk and continue to run, or it may only run each time the application is used. Early viruses, relying on floppy disks for transmission, spread quickly as infected data disks were shared around an office, or pirated software was passed around a playground. Nowadays, viruses rely on devices such as flash memory cards or are transmitted through internet connections.
Although some viruses are not intended to cause harm, the majority of these programs are designed to harm users, by corrupting their data or attacking the operating system itself or providing an exploitable ‘back door’, giving attackers access to the computer. Even where no harm is intended, viruses consume memory, disk space and processing power.
1.1 Worms

This image shows a small worm coming out of an apple.
Another type of self-replicating malware is the worm; like a virus it is designed to make copies of itself, but unlike a virus, a worm is a standalone application.
Worms spread through network connections, accessing uninfected machines and then hijacking their resources to transmit yet more copies across the network.
There are four stages in a worm attack:
- The first stage is when the worm probes other machines looking for a vulnerability that can be exploited to copy itself to.
- The second stage is to penetrate the vulnerable machine by performing the operations for exploiting the vulnerability. For example, the worm might detect an open network connection, through which it can get the remote machine to execute arbitrary instructions.
- In the third stage, the worm will download itself to the remote machine, and store itself there. This is often called the ‘persist’ stage.
- In the final stage, the worm will propagate itself by picking new machines to attempt to probe.
Worms were invented as a curiosity and have even been suggested as ways of testing networks or distributing software patches across a network; however their drawbacks far outweigh their benefits. Even the most ‘benign’ worm consumes resources and can affect the performance of a computer system.
1.2 Trojans

The image depicts a wooden Trojan horse being pulled along on a cart.
The final major type of malware is the Trojan (or Trojan horse) – named after the wooden horse that supposedly smuggled Greek soldiers into the ancient city of Troy.
A Trojan disguises itself as an entirely legitimate program (such as a screensaver), but behind the scenes it is causing damage – perhaps allowing someone else to gain control of the computer, copying personal information, deleting information, monitoring keystrokes, or using email software to pass itself on to other computers. Unlike viruses and worms, Trojans are not self-replicating − they rely on their apparent usefulness to spread between computers.
Some Trojans work in isolation. Some, however, rely on networks, either to transmit stolen information – such as passwords, bank account details or credit card numbers – or to act as back doors to compromised computers. They allow attackers to bypass the operating system’s security features and gain access to data or even control the machine over a network.
Trojans have become a serious problem with Android apps.
1.3 Defining terms

The image shows a person using a laptop which is sitting on top of a pile of books.
In addition to the types of malware described in the previous sections, ‘Adware’, that forces users to view advertising, and ‘Spyware’, malware that attempts to access personal information and user passwords, are other examples you may have heard about.
From the Sophos Threatsaurus PDF downloaded in Week 1 (https://ugc.futurelearn.com/ uploads/ files/ 3f/ d3/ 3fd36a66-d941-4595-b587-1a7b41998ae9/ Week_3_Sophos_Threatsaurus_AZ.pdf) , look for a term that you have not come across before.
Try to think of a way to define the term in your own words.
You could also look at examples or information from the sources recommended in Week 1, Section 2.2, How to keep up to date.
2 How malware gets into your computer

This abstract figure shows an open laptop and a number of circles and spheres with numbers floating around them.
Malware can get into a computer through a variety of mechanisms, most of which involve exploiting a combination of human and technical factors.
For example, a malware creator might get you to download their malware by putting a link in an email, or attaching the malware to an email. Alternatively, malware might be packaged with illegal copies of standard software so that it can get into the machines of people who choose to use these illegal copies rather than pay for the genuine versions.
However, before looking in detail at how malware gets into your computer, it’s worth thinking about why it does. What is malware for?
2.1 What is malware for?

The image shows a city at night, with curved lines connecting different parts of the city.
There are many reasons why malware is created including intellectual curiosity, financial gain or corporate espionage.
Many programmers thrive on the challenge of seeing what is possible, and set out to create a malware program even if they do not intend to do harm. Perhaps the most famous of these experiments was the 1988 Morris Worm – the first worm to spread over the internet. The supposed intent of this worm was to gauge the number of machines connected to the network. However, the result was to slow down the operation of infected machines to the point of being unusable.
Worms continue to represent a major threat, as shown by the case of the Conficker Worm of 2008.
Case study: Conficker
In 2008, Microsoft Windows computers began being infected by an advanced worm called Conficker, which spread when users shared files, either over networks or via USB flash memory drives. The malware disabled important security features, such as antivirus software and automated update systems and blocked users from downloading fixes. At the same time, Conficker would exploit a weakness in Microsoft’s server software to infect computers on the same network.
Conficker became the fastest-spreading malware known then, eventually being found in almost every country. Conficker outbreaks were reported from (among others) the armed forces of the UK, France and Germany, as well as the British House of Commons and UK police forces. In the US, Conficker’s impact was sufficiently serious that the Department of Homeland Security set up a Conficker Working Group of security experts tasked with creating strategies that could be used against similar outbreaks in the future.
Conficker’s authors were clearly not amateurs. They released new variants of Conficker on a regular basis to overcome weaknesses in the original malware and took steps, (including using digital signatures), to ensure that no one else could hijack their program.
Although Conficker caused a great deal of nuisance, it did not appear to do any actual harm to data, however, the program could have delivered other malware that would have attacked users. In many ways, Conficker was a harbinger of the advanced criminal malware – such as Cryptolocker – that is a major threat to today’s users.
A detailed analysis of the development of Conficker and how the source was identified was published by Mark Bowden in the New York Times in June 2019: https://www.nytimes.com/ 2019/ 06/ 29/ opinion/ sunday/ conficker-worm-ukraine.html
2.2 Phishing

This image shows a figurine of a fisherman standing on top of a computer keyboard. On the end of his fishing line is a piece of paper with the word 'Password'.
Phishing is any attempt by attackers to steal valuable information by pretending to be a trustworthy party – a form of social engineering attack.
So, an attacker might impersonate a bank to obtain credit card numbers or bank account details. It gets its name from ‘fishing’ – as in ‘fishing for information’, the process of luring people to disclose confidential information.
Phishing relies on people trusting official looking messages, or conversations with apparently authoritative individuals, as being genuine. It is widespread and it can be enormously costly to people who find their bank accounts emptied, credit references destroyed or lose personal or sensitive information.
Email phishing
The use of electronic technologies to perform phishing attacks was described in the late 1980s, but the term did not become commonplace until the mid 1990s when a program called AOHell allowed AOL users to impersonate other people (including the founder of AOL itself).
Phishing became increasingly common as more and more people connected for the first time and began receiving official looking messages that looked very much like those sent out by genuine organisations such as banks, stores and government departments. What most of these users did not realise was that not only could email addresses be faked, but that electronic data can be easily copied – just because an email claims to come from your bank and has your bank’s logo doesn’t mean that it is genuine.
Phishing emails may be indiscriminate. A phisher will create an email asking the user to get in touch with a bank or credit card company claiming that there is a problem with the account or that the bank may have lost some money. These sorts of messages make people justifiably worried and more likely to follow the instruction. The phisher will then include some plausible looking details such as the bank’s logo and address and then send it to millions of individuals. Among all the recipients, a few people will have accounts with that bank and will click the link in the message, or telephone a number, which will begin the process of eliciting further personal information.
What to do
If you do receive an email that worries you from an organisation such as a bank or shop that you use, do not click on or follow the links in the message. Get in touch with their customer services department, or log in to your account through their website. Type in their web address or use the address in your list of favourite sites, or use their published phone number. Most organisations will have a published policy of not asking for sensitive information such as your password through email or over the phone so you should be suspicious of anything that contravenes this policy.
Social media phishing
Although email still accounts for the majority of phishing attacks, the technique is also used in social media sites as well as in text messages. The same rules apply – if in doubt, go to the official site and make contact with the company through their published links.
As we saw in the first week of the course, phishing can sometimes be targeted at individuals or specific parts of an organisation. These attacks, commonly called a ‘spear phishing attack’, will depend on detailed information about the target. For example, an attacker might use information gleaned from recent emails to craft a plausible reply that appears to come from colleagues of the targeted user.
Attackers may also include links to malware-infected software in personal messages posted in social media. This is especially common after major disasters or during fast-breaking news when people are likely to click on interesting looking links without thinking carefully.
2.3 Trapping phishing emails

This is a cartoon showing a fishing boat in the sea. In its net are a number of captured letters and pieces of paper.
Phishing is just one type of spam email which clutters our mailboxes and often delivers unsuitable or even illegal content to individuals.
Spam
Spam is yet another consequence of the early internet being developed by people who trusted one another. Just as we have had to protect computer networks against hackers – which you’ll cover in Week 6 – as more and more people have accessed the internet, email has become a tool that anyone can use for good or bad.
Most internet email is moved around the world using the Simple Mail Transfer Protocol (SMTP) which defines a standard template of commands and formatting that allow different mail programs, on a huge range of computers, to understand one another. Protocols are used to specify a set of special messages that should be exchanged between computers to achieve a particular functionality, in this case the delivery of email.
SMTP was defined when the internet had only a tiny number of users, so the original specification did not include any way for computers to authenticate one another, i.e. there was no way of knowing if the message claiming to come from TrustedBank actually came from TrustedBank’s computers. This weakness was addressed in a later extension to SMTP called SMTP-AUTH, but crucially it was not required, and so almost all mail servers still accept unauthenticated messages.
Spoofing
Spammers can attack a mail system by changing the information stored in email ‘envelopes’ which enclose the messages themselves. This is known as ‘spoofing’ and allows a spammer to disguise their actual address by writing new addresses for the sender (such as replacing their own address with that of TrustedBank) and the destination for receipts. Since SMTP servers do not perform any authentication, they simply pass on the email without checking that it was sent out by TrustedBank.
Simple spoofing is now being challenged by technologies that allow genuine senders to authenticate messages which can be checked by the recipient’s mail server, however only about half of all mailboxes have any protection against spoofing.
Provided a spammer has access to a fast network (or increasingly to a botnet), spam costs the sender almost nothing and although only a tiny fraction of users will respond to a spam message, sufficiently vast numbers of emails are sent that the rewards far outweigh the costs. It has been estimated that seven TRILLION spam messages, making up more than 85% of all email, were sent during 2011 alone. In 2018, spam was estimated to be down to 55% of all messages. Such is the torrent of spam that internet service providers and companies have to buy far more bandwidth and storage than they will ever need for legitimate purposes.
2.4 Spotting a phishing email
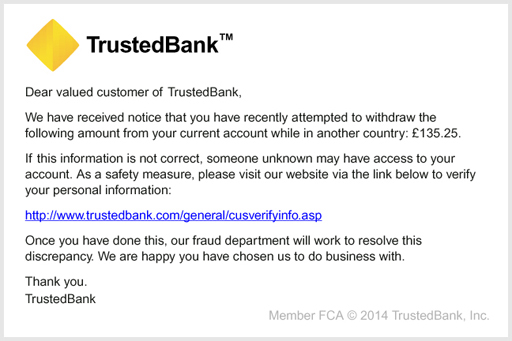
This is an example of what could be a phishing email.
Although a phishing attack may appear plausible at first glance, there are some tell-tale signs that should make you very cautious about clicking on any links or giving any personal information to the supposed sender.
Read through the points below to find out what to look out for.
Spelling mistakes: Most English-language phishing expeditions are sent from countries where English is not the primary language. Attackers often give themselves away by imprecise use of English, even with quite common phrases, and including spelling errors. So read the message carefully. However, there are many phishing emails that use excellent English.
Who is it to? Many, but not all phishing attacks do not use your name in the introduction – preferring ‘Dear valued customer,’ or ‘Dear user,’. This is because they cannot personalise the emails sufficiently. Your bank or online store can do this and should address you as ‘Dear Bob,’ or ‘Dear Mrs Jones,’ (or whatever your name is). However, note that because so many millions of user details have been revealed by data breaches it is quite possible for a phishing email to use your personal details.
Poor quality images: Sometimes, the images used in the emails are fuzzy, or your information may appear as an image rather than type. These images have been copied from screens and would not be used by original companies. It is easy to obtain images every bit as good as the originals though, so a high quality image should not persuade you the message is genuine.
Content of the email: In almost all countries, banks and other financial bodies will not email you to tell you about problems with your account. They recognise that email is fundamentally insecure and that personal information should not be sent by email. So, even the method of communication will give you a clue about whether it’s genuine. The email may give a false sense of urgency, claiming that your account is at risk if you do not act quickly. This is not the case.
Links: The text of a web link is not the same as the destination of the link itself – the link might say it is taking you to, for example http://www.trustedbank.com, but in fact it can take you anywhere on the web – including to a phisher’s computer impersonating that of a reputable company. You can spot some fake links by hovering your mouse pointer over the link – but do not click the button. The actual destination of the link will appear at the bottom of the window or in a small floating window next to the link. In a phishing email, the link will probably be to an address you aren’t familiar with. Other fake links may display a genuine destination when you hover over them, but still take you to a fake website because code in the page intercepts the link and sends your click elsewhere.
The example message below claims to come from a fictional site called ePay and is about unauthorised activity on the account. The link says it goes to ePay’s site, but the address is slightly different and is unlikely to be owned by ePay.
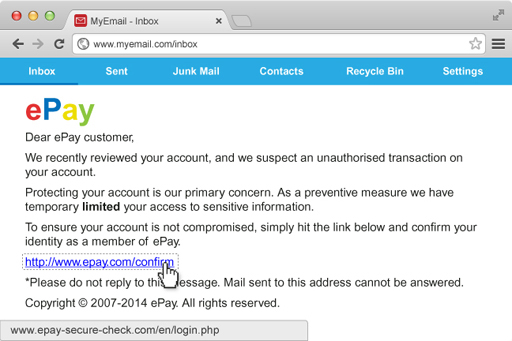
So the rules are to be suspicious and to look at the details of the message, the language, the quality of the images and where the links actually take you. Banks and shops will always prefer you to call them and check rather than risking your security.
If you have not already done so recently, check you email address on https://haveibeenpwned.com/. Email addresses that are on a breached list are much more likely to receive spam than those that are not listed. If your email address is on the list you need to assess what related data may have been revealed. You may need to change passwords that use that email address, especially if you have reused the same passwords in the past, or even stop using that email address
2.5 Emails are not the only phish

This image shows a computer keyboard. Instead of letters and numbers, on each key is an emoji.
Please don’t think that malware is spread solely through email. Malware will be spread through any means possible.
Malware can be distributed by including it with pirated material such as illegal copies of software, video games and movies. Malware can also be installed on your computer by clicking links on websites – especially sites that distribute illegal copies of software, videos and pornography – or by annoying pop-up windows that claim to have identified problems with your computer (quick tip – they probably haven’t! But it’s a great prompt to run your antivirus software and remind yourself what a genuine alert looks like on your computer).
A recent trend is for malware to be spread through social networking services, like Cory’s experience of the direct message on Twitter that you heard about in Week 1. Once it is on a machine running social networking software, the malware masquerades as the real user and posts messages containing links to sites that distribute yet more malware.
Once again, this type of malware relies on social engineering to multiply – users of social networks are highly likely to click on links they think have come from friends and spread the infection. Most of these social networking infections have exploited weaknesses in client software rather than the web versions of the networks, so it is important to keep social networking client software, such as the Facebook App for mobile devices, up to date.
2.6 The role of malware in click fraud

This is an image of a pile of notes of different currency, for example American dollars and Euros.
The majority of modern malware has been designed with malicious intent; to cause damage to a computer’s operating system or its data, or to steal information from a user, or increasingly, from online advertisers.
As you will have seen, many large websites rely on advertising for their revenue. The amount of money spent on online advertising is growing rapidly with more than £16 billion spent in the UK alone during 2011. This is expected to exceed £26 billion in 2020. Advertisers like online advertising because it can be relatively cheap compared to a printed advertisement and because software allows for individuals to be targeted with specific adverts for products they are likely to buy.
The most common type of advertising is ‘pay per click’ where advertisers only pay the owners of a site when a user clicks on an advert. This system can be subverted by either generating clicks that don’t come from genuine customers, or by hijacking a click intended for a genuine advertiser. This is known as click fraud, it accounts for more than 20% of all clicks and it can be aided by malware. Computers all around the world, operating as a botnet, can generate false clicks, siphoning money from advertisers through multiple layers of publishers and redistributors to hide its eventual destination.
There are two frequently used modes of click fraud – both can use botnets to generate the clicks.
- Clicking on targeted company ads on genuine sites to waste their advertising revenue. The perpetrator doesn’t collect any income.
- The criminal sets up many hundreds or thousands of websites, often just copying other website content. They sign up for advertising e.g. adsense with google. Then they commission a bot network to click on the ads on their own pages and collect their share of the ad revenue.
While an individual click will only raise a tiny amount of money, done millions of times, click fraud can raise serious amounts of money. In 2011, the FBI broke a click fraud operation based in Estonia that had infected more than four million computers in 100 countries and stolen in excess of $14 million from advertisers.
In 2016, a Russian criminal group created 6,000 websites with over 250,000 pages containing video advertising. Their bot network ‘watched’ over 300 million video ads each day. They were defrauding the advertisers of close to four million dollars a day.
2.7 Botnets

Transcript
You heard about botnets briefly in Week 1, when we said that botnets are created using malware that give an attacker control over a group of computers and commonly use them to gather information from the computers (e.g., usernames and passwords), launch attacks against others. These attacks might be sending spam emails, or flooding a website with so many requests for content that the server cannot cope, which is known as a denial-of-service attack.
A single piece of malware can cause enormous damage, but when thousands, or even millions of computers run the same program, their effects can be devastating. So a botnet is a group of computers that coordinate their activity over the internet. There are a number of harmless botnets used for such purposes as the Internet Relay Chat (IRC) text messaging program, but the vast majority are created by malware.
Botnets spread through viruses and worms and once installed on the victim’s computer they use the internet to make contact with a control computer. At this point, the infected computer (often called a zombie) will do nothing more except periodically check for instructions from the control computer. Over time, more and more computers are recruited to the incipient botnet until it may contain tens of thousands of zombies, but they don’t raise suspicion as they appear to be doing nothing.
At some point in the future, the control computer will issue a command for the botnet to wake up and begin doing something. Often the people who created the botnet itself have either sold or rented the botnet to another group who want to use its capabilities.
Botnets have been used to flood the internet with spam messages, to commit fraud against advertisers and to perform so-called distributed denial-of-service attacks on companies and governments. Botnets are so large, and so widely distributed across the internet that they can be very hard to tackle and the effects of a coordinated attack on critical parts of the network can mean even very large websites struggle to remain online while the botnet targets their computers.
2.8 Confessional

This is an illustration of two laptops sitting opposite each other, with various robots shooting lasers at each other.
It’s time to confess! Think about the following:
- Has your computer ever been infected with malware?
- Do you know the name of the malware that was involved?
- Was it a virus, worm or Trojan?
- What happened, and what were the consequences?
If you discuss this with others, remember not to share any personal information including the name of the company you work for.
3 Keeping yourself protected

This shows a needle being injected into a bottle.
The growth in malware has been accompanied by an explosive growth in software designed to prevent it spreading.
So-called antivirus software (which actually targets a range of malware) is a multi-billion pound business with a large number of commercial and free packages available for all computer users ranging from individuals to large corporations.
At the same time, the developers of computer operating systems are incorporating a wider range of security features that try to stop malware running at all.
And there is a lot you can do yourself to keep yourself protected such as installing antivirus software, keeping your software up to date, looking out for the signs of phishing emails and implementing new security developments.
Before you install or change anti-malware software you should check the reviews from a number of reputable and independent organisations. Look at how they rate the free packages as well as the paid for packages.
3.1 Antivirus software

This image shows numerous toy soldiers guarding a laptop.
Antivirus software aims to detect, isolate and if necessary, delete malware on a computer before it can harm data. Antivirus software uses several techniques to identify malware – the two most common are known as signatures and heuristics.
Signatures
A malware’s signature is a distinctive pattern of data either in memory or in a file. An antivirus program may contain thousands of signatures, but it can only detect malware for which a signature has been identified and published by the antivirus program’s authors. As a result there is a period between a new piece of malware being released ‘into the wild’ and when its signature can be incorporated into antivirus products. During this period, the malware can propagate and attack unprotected systems, exploiting the so-called ‘zero day’ vulnerabilities that exist until the systems are fixed and antivirus signatures are updated. It is not uncommon for several variants of a malware program to be published at intervals, each sufficiently different that they possess different signatures.
A second weakness of signatures is that more sophisticated malware has the ability to change its program (it is said to be polymorphic or metamorphic), disguising itself without affecting its operation.
Heuristics
Complementing signatures, heuristics use rules to identify viruses based on previous experience of the behaviour of known viruses. Heuristic detection may execute suspicious programs in a virtual machine (a software recreation of a physical computer) and analyse the program for operations typical of known malware (such as replicating itself or attempting to overwrite key operating system files); or it might revert the program back to its original source code and look for malware-like instructions. If the heuristic analysis considers that the file acts in a malware-like manner, it is flagged as potentially dangerous.
Unlike signatures, heuristics do not require specific knowledge about individual types of malware – they can detect new malware, for which signatures do not exist, simply by their behaviour. The drawback of heuristics is that they can only draw conclusions based on past experience; radically new malware (which appears all too regularly) can pass unnoticed.
Issues with antivirus software
Although antivirus software is an essential part of protecting your computer, it is not a complete solution to malware problems.
Despite the best endeavours of its makers, antivirus software has occasionally proved to contain bugs with consequences like being inaccurate, failing to update itself or simply consuming huge amounts of computer power. Fortunately, these problems are rare, easily fixed and much less serious than the risk from a malware attack.
Note that not all anti-malware software is equally good. There is even fake anti-malware offered for sale, especially for mobile devices.
Check the reviews of anti-malware software by reputable organisations:
In October 2019, the BBC reported that a combined operation by British Police, Indian police and Microsoft had shut down two Indian call centres using web pages and phone calls to sell fake computer security services. Victims were conned out of thousands of pounds. The City of London Police say it is one of the most common online scams, with over 2,000 cases reported to Action Fraud every month.
The police offered these tips to avoid being scammed:
- Always check out callers, especially cold callers who claim to be Microsoft, your telephony provider or internet service provider.
- Legitimate organisations will encourage you to call back via a number you've obtained from a trustworthy source.
- Do not assume that the number displayed on your phone is accurate, these can be spoofed, leading you to believe that the caller is in the UK or from a trusted organisation.
- Don't call phone numbers on pop-up messages which indicate there is a problem with your computer.
3.2 Installing antivirus software

This image shows six computer screens, each displaying images related to antivirus software, such as images of locks and the words 'privacy, 'password' and 'protection'.
If you don’t already have antivirus software on your computer, it should be a high priority to install some. Windows 10 has Windows Defender built into the OS and got a top rating in June 2019: https://www.av-test.org/ en/ antivirus/ home-windows/.
There are a number of good, free packages available but you should always check that it meets your needs before installing it. Some important features to consider are:
- Is it compatible with your computer? You will have to make sure the antivirus software is appropriate for the operating system and computer that you have.
- Does it come from a reputable source? For example, it may have been developed by one of the major computer security companies, such as Norton, Kaspersky, Sophos or AVG. Alternatively, it may have been provided or recommended by your bank or internet service provider.
- Does it provide updates that allow it to protect you against the latest malware? New malware is being developed all the time, and it is important that you use an anti-malware application that will update itself.
- Have you checked the reviews? Use: https://www.av-test.org/ en/, https://selabs.uk/ or https://www.av-comparatives.org/.
Use the above criteria to research antivirus products available so that you can choose the one that is best for you. If you already have an antivirus application, answer the questions for the program you have.
3.3 Keeping your software up to date
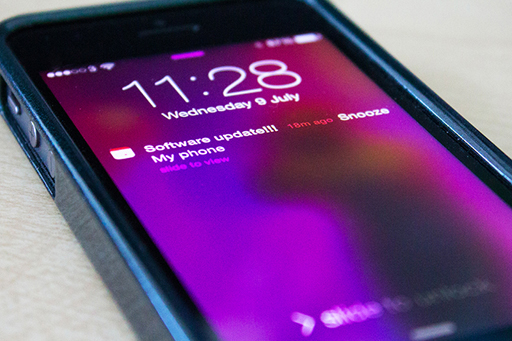
This is an image of a smartphone. On the screen is a calendar alert for a software update.
Computer operating systems and application programs are so large that they inevitably contain bugs, some of which could compromise your security.
The majority of companies issue regular updates to their programs to fix known problems. Major operating systems and some application packages (such as Microsoft Office and the Adobe productivity suite) automate most of the process of updating software by automatically checking for updates, prompting the user to install them and then actually performing the update itself. This process is sometimes called ‘patching’.
Activity 1 Keeping your software up to date
How do you go about keeping one of the software applications on your computer or device up to date? Reseach the application online to find out if there is any additional information about keeping it up to date.
3.4 End-of-life software

This image shows an old-fashioned typewriter, but with a DVD drive and a mouse attached.
Software is continually being developed and replaced by a new version. The lifespan of software begins when it is released and ends when it’s no longer supported and updated.
Software doesn’t become completely unsafe as soon as it reaches the end of its lifespan; in many cases you can continue to use it, but you should be aware that security risks may not be addressed by its authors. If you work for an employer, you may be required to move to an updated version of the software as part of their security management process.
The first effect you will feel from end-of-life software is that companies will cease telephone and internet support for queries. So if you have problems using a product you won’t get any help. The manufacturer may also withdraw bug reporting, so you won’t be able to tell them about problems. At the same time you might also find that cheap upgrades to later versions of paid software are no longer available.
Most large software companies will continue to offer critical software support to obsolete products for a period of time. However, they will not prioritise these programs, instead they will concentrate on fixing problems in up to date software and releasing patches; only then testing older products to see if they are affected and if they can be fixed. This means that users of older products might be exposed to vulnerabilities for longer than those using more modern software. Developers of malicious software, who know about unpatched bugs in older products, are likely to attack these older, weaker programs in preference to more secure programs.
In 2019, Windows 10 was used by 55.77% of Windows OS computers. Windows 7 was still used by 33.42% and Windows 8 and XP and older by 10%. Windows 7 loses extended support on 14 January 2020. Windows 8.1 loses extended support on 10 January 2023.
For example, Windows XP is now no longer supported by Microsoft (since April 2014), despite being widely used. Windows XP and Windows Vista, the two oldest operating systems, have much higher incidences of infection than the newer operating systems that feature much greater levels of security.
If you are using end-of-life software, security applications such as up-to-date firewalls and antivirus software are essential as well as keeping up to date with key applications, such as web browsers and email programs which are used to send and receive personal data. Good information security will help keep you safe. Even if you take these precautions, you should begin planning for a transition to more modern applications. Upgrades are relatively cheap from one version to another (or even free), and any expense should be considered in the light of what you stand to lose if you do not use more secure software.
Finally, don’t forget that even supported software can be vulnerable if it is not updated regularly. In 2017, the WannaCry ransomware infected thousands of computers globally and it was later determined that most infected systems were running Windows 7, an operating system that was still supported by Microsoft. Indeed, months before the global infection of systems, an update to fix the vulnerability exploited by WannaCry had been released, but many systems had not been updated.
3.5 Sandboxes and code signing
In addition to keeping software up to date and using antivirus products, there are other technological innovations that can help mitigate the threats of malware.
Sandboxes and code signing are examples of some of the technologies that developers are integrating into the software we commonly use to help protect our computers.
Sandboxes
A software sandbox is a way for computers to run programs in a controlled environment. The sandbox offers a constrained amount of memory and only allows very limited access to resources such as operating system files, disks and the network. In theory, the software cannot break out of the sandbox and affect other parts of the computer, so even if malicious software attempts to overwrite parts of the disk, the sandbox will prevent it from doing so.
Sandboxing is widely used in modern web browsers, such as Internet Explorer 10 onwards, and Chrome, to prevent internet content causing damage to files on the computer. Similar sandboxes exist for most browser plugins and the Adobe Acrobat PDF viewer.
Code signing
Code signing is a use of cryptography where software companies issue digitally signed copies of their programs that can be checked by recipients for its authenticity. You’ll discover more about digital signatures in Week 4.
Code signing is used by the designers of all three major operating systems (Microsoft Windows, Mac OS and Linux) to guarantee that operating system updates are genuine even if they are distributed using flash memory cards rather than directly from the publisher.
Microsoft Windows uses code signing on operating systems components, such as hardware drivers, which have direct access to the heart of the operating system. Apple has taken code signing even further. Versions of Mac OS from 10.8 onwards can restrict users to only running programs that have been certified by the Apple App Store. While this does offer greater security against malware, it may also restrict choice and prevent users from running certain unsigned apps from third parties.
Next, you have an opportunity to review what you’ve learned in the end-of-week practice test.
4 Week 3 quiz
This quiz allows you to test and apply your knowledge of the material in Week 3.
Complete the Week 3 practice quiz now.
Open the quiz in a new window or tab then come back here when you’re done.
5 Summary of Week 3
This image shows silver spider-like robots on a patterned image.
You have also taken a closer look at ways of keeping attackers from impersonating you online or infecting your devices with malware.
In the next part of the course, you will delve a little deeper into the technologies that underpin information security, first focusing on how to protect the networks that we depend on for transmitting our digital information and accessing online services.
There is some optional further reading in the next section relating to some basic precautions you should take before you go online.
You can now go to Week 4: Networking and communications.
Further reading
Keep a clean machine Basic precautions to take before you go online.
References
Acknowledgements
This course was written by Arosha K. Bandara.
Except for third party materials and otherwise stated in the acknowledgements section, this content is made available under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 Licence.
The material acknowledged below is Proprietary and used under licence (not subject to Creative Commons Licence). Grateful acknowledgement is made to the following sources for permission to reproduce material in this course:
Images
Figure 1 © Eraxion (via iStock Photo)
Figure 2 © JordiRoy (via iStock Photo)
Figure 3 © Colin Anderson (via Getty Images)
Figure 4 © vadimguzhva (via iStock Photo)
Figure 5 © Carol and Mike Werner/Visuals Unlimted, Inc. (via Getty Images)
Figure 6 © Yugi Studio (via Getty Images)
Figure 7 © Stephan Zabel (via Getty Images)
Figure 8 © Trina Dalziel (via Getty Images)
Figure 9 © Andrew Levine http://commons.wikimedia.org/wiki/File:PhishingTrustedBank.png
Figure 11 © Dimitri Otis (via Getty Images)
Figure 12 © enjoynz (via iStock Photo)
Figure 13 © ryccio (via Getty Images)
Figure 14 © aydinmutlu (via iStock Photo)
Figure 15 © John Lamb (via Getty Images)
Figure 16 © Danil Melekhin (via Getty Images)
Figure 18 © FreezeFrameStudio (via iStock Photo)
Figure 20 © webking (via iStock Photo)
Figure 21 © addimage (via iStock Photo)
Every effort has been made to contact copyright owners. If any have been inadvertently overlooked, the publishers will be pleased to make the necessary arrangements at the first opportunity.
Don't miss out:
1. Join over 200,000 students, currently studying with The Open University – http://www.open.ac.uk/ choose/ ou/ open-content
2. Enjoyed this? Find out more about this topic or browse all our free course materials on OpenLearn – http://www.open.edu/ openlearn/
3. Outside the UK? We have students in over a hundred countries studying online qualifications – http://www.openuniversity.edu/ – including an MBA at our triple accredited Business School.
Copyright © 2015 The Open University

