Week 5: Cryptography
Use 'Print preview' to check the number of pages and printer settings.
Print functionality varies between browsers.
Printable page generated Sunday, 9 November 2025, 4:26 PM
Week 5: Cryptography
Introduction

Transcript
Cory explains the focus for this week: cryptography.
Cryptography is a specialised area of mathematics concerned with protecting information so that it can be transmitted and received securely even when there is a risk that a hostile third party might intercept or modify the data. You will recognise it as it’s been mentioned before as a technique that can help with protecting information.
We are now going to look at this important aspect of cyber security in a little more detail.
1 The secret of keeping secrets

This is a black-and-white photograph of a number of women in an office at machines.
There have been many applications of cryptography throughout history, ranging from simple ciphers used by Julius Caesar to send military orders to his generals, to the more sophisticated medieval ciphers that withstood most attacks until the late ninteenth century and the famous Enigma codes of the Second World War.
The development of computers in the twentieth century allowed for far more complex means of encryption. Computers could perform:
- the mathematical operations that underpin all cryptography
- much more complex mathematics than could be reasonably expected of a human
- much faster than a human
- on much more data than a human could handle.
Any data that could be represented in binary format, i.e. using 0s and 1s, can be encrypted by a computer. It is not an exaggeration to say that encryption makes much of the modern world possible. Some commonplace applications for cryptography include:
- secure banking and payments systems – cryptography ensures your money is safe when it is transferred between accounts, issued at ATMs or used to shop online
- protecting conversations made over mobile telephones
- safeguarding wireless networks that give access to the internet
- securing files on hard disks and memory sticks
- authenticating electronic documents
- electronic voting
- securing media files such as music or movies from piracy, where it is known as Digital Rights Management (DRM).
1.1 Plaintext and ciphertext

As in previous weeks, there is some terminology we need to introduce:
- plaintext – information that can be directly read by humans or a machine (this article is an example of plaintext). Plaintext is a historic term pre-dating computers, when encryption was only used for hardcopy text, nowadays it is associated with many formats including music, movies and computer programs
- ciphertext – the encrypted data
- a cipher – the mathematics (or algorithm) responsible for turning plaintext into ciphertext and reverting ciphertext to plaintext (you might also see the word ‘code’ used – there is a technical difference between the two but it need not concern us now)
- encryption – the process of converting plaintext to ciphertext (occasionally you may see it called ‘encipherment’)
- decryption – the process of reverting ciphertext to plaintext (occasionally ‘decipherment’).
1.2 Encryption keys

This is an abstract image of different coloured numbers and patterns.
Keys are pieces of information that determine the output from an encryption (or decryption) process. A single cipher can produce an almost limitless number of different outputs with different key values, allowing secure communication even if the cipher itself is known to hostile third parties.
It might surprise you to know that almost all ciphers are published in the scientific press or in standards documents. Having them available for widespread scrutiny allows many people to check that they are secure and do not contain weaknesses which could be exploited to compromise the security of the data encrypted using that cipher.
A computer encryption key is nothing more than a string of bits where each bit can have a value of either 0 or 1. The number of possible values for a key is simply the total number of values that the key can have. So our one-bit long key can only have two possible values – 0 and 1. If we choose to have a two-bit key it could have one of four possible values – 00, 01, 10 and 11. In fact every time we increase the length of the key by one bit we double the number of possible keys – so a three-bit key has eight possible values – 000, 001, 010, 011, 100, 101, 110 and 111.
The total number of keys can be written in scientific form as 2key length; so a key with a length of eight has 28 – that is 256 – values.
But how long should a key be? How short is too short?
The problem with short keys
Short keys are vulnerable to what is known as a brute force attack, just like you learned in Week 2 about passwords. A brute force attack is where a computer, or a number of computers, try every possible value for a key until they produce recognisable plaintext.
Since computers can work through key values extremely rapidly, keys must be sufficiently long that they offer a very large number of possible values.
Keys may be known to the user in the form of passwords, or they may be stored in a computer’s hardware (such as the decryption keys stored on a DVD player that allow it to play the encrypted data stored on the movie disk), or they can be generated by a computer as and when they are needed (such as conducting a secure transaction on a shopping site).
Next, you’ll learn about the key distribution problem.
1.3 The key distribution problem
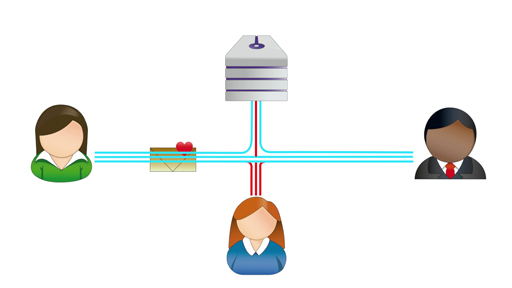
Transcript
Traditionally, symmetric encryption suffered one enormous shortcoming – it was necessary for either the sender or the recipient to create a key and then send it to the other party. While the key was in transit, it could be stolen or copied by a third party who would then be able to decrypt any ciphertexts encrypted with that key.
Another problem is that a large number of key pairs are needed between communicating parties. This quickly becomes difficult to manage the more there are. This can be calculated as n(n-1)/2 where n is the number of communicating parties.
For example, if ten parties want to communicate with each other securely they would need 45 different key pairs: 10(10-1)/2 = 45. This would increase to 4,950 if there were 100 communicating parties!
This problem, called the key distribution problem, affected anyone wishing to use encryption until the 1970s when a method of distributing keys without actually sending the keys themselves was developed independently by GCHQ in the United Kingdom and Whitfield Diffie and Martin Hellman in the United States. The British discovery was kept secret for many years, so today the solution is known as the Diffie–Hellman key exchange method.
Symmetric encryption methods have the advantage that encryption and decryption is extremely fast, making them ideal for transmitting large amounts of secure data. In the video you saw how key distribution was achieved between two people, Alice and Bob.
1.4 Asymmetric or public key cryptography
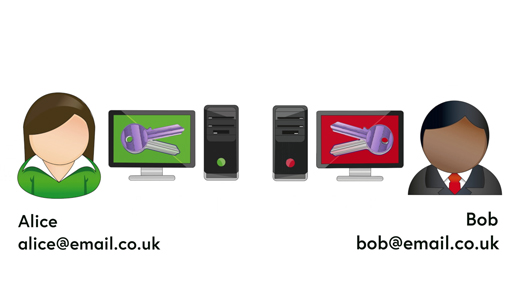
Transcript
Asymmetric cryptography, better known as public key cryptography, side-steps the key distribution problem as each user creates their own keys:
- the private key which they keep safe and never distribute
- the public key which can be sent to anyone with whom they want exchange encrypted information.
Together the two keys are known as a key pair, which is what was used by Alice and Bob.
Unlike symmetric encryption, the two keys behave differently; the public key is the only key that can decrypt ciphertext encrypted using the corresponding private key and the private key is the only key capable of decrypting files encrypted with the corresponding public key. Crucially, the value of one key cannot easily be determined from the other, so even if the public key falls into hostile hands, the value of the private key cannot be determined.
Public keys can be distributed using email attachments or through public key chain servers which act as distributors for large numbers of public keys. The creator of a public key uploads their key to the key chain server and it is freely available to anyone who wants to use it.
Although the mathematics behind public key cryptography is incredibly complex, the process of using it is relatively simple. To send a message using public key cryptography is simple. The sender obtains a copy of the recipient’s public key, either by email or from a key chain server, and uses it to encrypt the message. The resulting ciphertext is then sent to the recipient who uses their corresponding private key to restore the original plaintext.
Public key cryptography is popular because there does not have to be any initial secure exchange of secret keys for an encrypted message to be sent (remember, users only ever exchange their public keys). However, it is generally far slower than symmetric encryption; and because of a quirk in the underlying mathematics, traditional public key cryptographic techniques require far longer keys to offer the same level of protection as symmetric encryption.
A newer type of public key cryptography, known as ‘elliptic curve cryptography’, can be just as secure as symmetric encryption using similar key lengths.
In the next section you’ll discover why these encryption methods aren’t used to keep the internet more secure.
1.5 Why isn’t the internet encrypted?
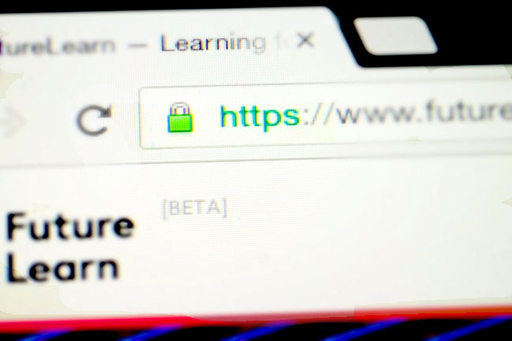
This is a screenshot of a web browser - our attention is drawn to 'https' at the start of a web address.
Crucially, one part of everyday life that is not routinely protected by cryptography is the internet itself. The majority of emails and web pages are sent in plain view and can be intercepted and read by a malicious third party.
In theory, the whole of the internet could be protected using cryptography, but this is unlikely to happen because it takes a certain amount of computer power to encrypt and decrypt information so there would be significant costs if it were to be used throughout. Also there are a range of web applications, such as reading news sites or browsing online shops, that do not involve any sensitive information and therefore do not need to use encryption.
Applications running over the internet selectively use cryptography for key tasks (such as processing payments for online shopping) and users may choose to use cryptography for additional purposes (such as securing email).
The data sent by many websites you visit is encrypted in transit. This is sometimes shown by a padlock symbol in the address bar of the web browser. You’ll learn more about this later in the course.
Review the list of digital information and online services you compiled in Week 1 of the course. Based on the threats you associated with each item in your list, think about some examples of how you could use cryptography to improve your security.
2 Putting cryptography to use

In the background is a large image of a human eye. Overlaying this is a set of number ones and zeroes.
So far this week you have studied the basic cryptographic techniques that can be used to protect the confidentiality and integrity of your information. Now let’s examine how these techniques can be used in practice.
Transport-level encryption encrypts the text of the message between your device and the server that receives the data. One of the most common is STARTTLS. However, your messages may not be encrypted while sitting on a mail server.
End-to-end encryption ensures that the message remains fully encrypted all the way from the sender to the recipient.
Many websites, such as those for internet banking and online shopping, routinely use encryption to ensure that the data sent to and from your computer is safe from eavesdroppers. However, configuring the same technologies to protect activities such as email communication can be quite difficult because the tools involved are complicated to install and configure.
Most end-to-end encryption tools depend on a collection of cryptographic techniques, commonly called ‘Pretty Good Privacy’, PGP for short. PGP includes algorithms for symmetric and asymmetric cryptography. In order to help software vendors develop systems that can easily exchange encrypted information, a standard called OpenPGP was developed and agreed on by the Internet Engineering Task Force (IETF).
Some examples of tools available for encrypting emails include:
- GPG4Win – provides a set of standalone tools that can be used to encrypt and digitally sign emails, documents and other files. It provides some plug-ins to integrate these features into standard email software, such as Microsoft Outlook and Mozilla Thunderbird.
- GPGMail – this tool is designed to integrate with the Mail software provided by Apple. It can be used to both encrypt and digitally sign your email. It is easier to configure and use than the Windows tools, but is only useful if you use a computer running OSX.
- Enigmail for Thunderbird – this is a plug-in for the Thunderbird email client software that works across all operating systems. However, it requires manual installation of the GNUPG software, an open source implementation of the OpenPGP standard.
- Mailvelope – this is a browser plug-in that uses an implementation of the OpenPGP standard. It works with a variety of browsers and web-based email systems, such as Gmail or Yahoo Mail. However, there is a security problem with such web-based email systems. Although you may have encrypted the message from end to end, the details of the email address it is sent to, as well as who it is from, and the time the message was sent can be logged, and this metadata may compromise your security and that of the recipient.
A secure email service like Proton Mail or Tutanota can hide the metadata that links the sender to the recipient of the message.
In its most secure usage pattern, a user logs in to Proton Mail and leaves an email message for another Proton Mail user to log in and collect. The metadata about the users is never revealed and the message is also securely encrypted from end to end.
When the Proton Mail user sends an email to an external email address the metadata of the sender remains secure. Proton Mail sends an invitation to the recipient to view the encrypted message on the server. The mail service of the recipient may record that a message was sent by the Proton Mail server. If the user of Proton Mail uses the free service to send encrypted email to an outside email address they will have to send a key to the encryption to the recipient by some other means for the recipient to log in, such as a text message or phone call. This may reveal a link between sender and recipient.
A paid for service with Proton Mail allows use of PGP, so that a message can be sent to an external address using the recipients public key. No link need be created between the sender and recipient. However, the subject line isn’t encrypted.
In the next few sections we will explore an alternative way of using cryptography to protect your email communications.
2.1 Setting up a PGP email client
Zoomed in shot of a computer screen with what looks like encrypted text.
This section is optional. You’ll need to be able to install software on the computer you are using for this course to complete this. If you’re not able to do this then please still read through the steps so that you understand the process.
Select one of the PGP email clients described in the previous section and explore how to set it up and use it to send mail encrypted with PGP.
For example if you already use Thunderbird for your email client you could investigate the use of Enigmail. If you use Outlook for your emails you could investigate using Gpg4win. If you use a browser based email you can install a plugin from https://www.mailvelope.com/ en/
Follow the instructions on the Mailvelope website.
One of the best ways to test sending and receiving encrypted emails is to use two separate, free, web-based email accounts and open each one in a different browser. For example, use Firefox for one and Brave for the other. Install Mailvelope in both Firefox and Brave and set up one email account in Firefox and a different email account in Brave
Now follow the Mailvelope instructions to create and send an encrypted email from one of your accounts to the other.
Disclaimer: The Open University and partners associated with this course have found this software to be robust at the time of checking. However, installing software is done at your own risk and The Open University and their partners cannot be held responsible for any resulting damage to your computer.
2.2 Sending signed and encrypted email
Below is an optional activity.
Activity 1 Optional activities
As an alternative to exchanging encrypted emails with a colleague or friends, if you have set up Mailvelope or another PGP email client you can send an encrypted email to an automated mail box at The Open University:
- First send an email that simply says ‘public key’ to: cybersecurity-mooc@open.ac.uk
- The server will send back an automatic reply that includes the current PGP public key for this mail box.
Again follow the instructions on the Mailvelope website, or for the PGP encryption software that you are using, use this public key to create a new email with a message ‘testing encrypted content’
Note that you need all the characters including -----BEGIN PGP PUBLIC KEY BLOCK----- and -----END PGP PUBLIC KEY BLOCK-----
- Send your email to: cybersecurity-mooc@open.ac.uk. You will receive an email back from us to say that we’ve successfully decrypted your message! If you don’t receive an email within 2 hours, please try again.
To find out more about Mailvelope’s features or get help with specific problems visit Mailvelope help.
End-to-end encryption as a service
It can be a problem for organisations and individuals to set up the software for encrypted emails on all the devices that they use.
End-to-end encryption can be provided as a service. At the time of writing, Proton Mail and Tutanota both have a good reputation and also offer a free service.
Follow the instructions at https://proton.me or https://tutanota.com/ to set up two FREE accounts with the same service in two separate browsers. Then use these accounts to send a message from one account to the other.
In the last few sections you have explored what is involved in using cryptography to encrypt and sign email communications.
- What seemed to be the hardest parts of the process?
- What would you want to improve to make it easier?
- How does the use of Proton Mail or Tutonota compare with the use of Mailvelope or other secure email software?
You may find it useful to compare your experience with the instructions for one of the other tools mentioned in Section 2, Putting cryptography to use.
3 Comparing different cryptographic techniques
The field of modern cryptography is steadily growing with its increased use in everyday life when surfing the internet, using your card in a cash machine etc.
There are hundreds of different cryptography schemes each with different applications, some of the most notable are described below.
DES (Data Encryption Standard)
DES was first developed in the 1970s and was adopted by the United States National Bureau Of Standards as the US government standard for encrypting sensitive information. It is a symmetric cipher using 56-bit keys.
Due to DES’s relatively small key size it was discovered that it was possible to crack the encryption with a brute force attack. Although this was a theoretical risk when first proposed, the great increases in computing power over recent years have shown that DES can be brute forced in less than a day. It was this weakness that led to official adoption of other encryption standards, such as AES, by the US government.
A variant of DES, called Triple DES was developed to provide additional security, and be compatible with the previous version, without the requirement to develop a completely new cipher. Triple DES uses three rounds of DES encryption and three separate 56-bit DES keys.
Triple DES was widely used in e-commerce and online payment applications, as well as securing data in Microsoft Outlook, until 2018. When this course was first written it was thought that Triple DES would remain secure from a brute force attack until at least 2030. However, it is now considered to be insecure and was deprecated by NIST (the US National Institute for Standards and Technology) in 2017.
AES (Advanced Encryption Standard)
The realisation that the DES standard was no longer adequate led the United States government to call for a replacement. After an open competition lasting five years, AES was adopted as a US government standard in 2001. AES uses a combination of symmetric ciphers and either 128, 192 or 256-bit keys providing enhanced security over DES. Although some potential weaknesses have been identified in AES, most are theoretical, with the encryption being easiest to break in a situation where it has not been implemented correctly rather than in the case of a brute force attack where every possible key combination must be tried.
AES is now widely used in commercial applications since the underlying specification is freely available for personal or commercial use. It is used to protect archive files, encrypting computer file systems (such as Windows 2000 onwards), encrypting hard disks and for secure file transmission. Such is its importance that many microprocessors now include AES in their instruction sets to speed up encryption and decryption.
Blowfish
Blowfish was developed in the early 1990s as a potential replacement for DES, though AES ultimately became the agreed standard form of encryption. It is a cipher supporting variable key lengths from 1 to 448 bits. To date there has been no known successful attempt to break the encryption in its full implementation, although weaknesses have been identified when Blowfish is used with relatively weak keys. The related twofish and threefish ciphers have been designed to overcome these weaknesses, although most users have switched to AES.
Next, you’ll find out how cryptography is used to prove identity online.
3.1 Using cryptography to prove identity

This is an image showing a a substantial number of numbers in rows, of different colours.
Cryptography isn’t just used to hide secrets, it can also be used to authenticate data sent on an insecure network – such as the internet. The process begins by checking that your copy of a piece of data is an exact match for the one you requested.
Hashing
Hashing is the mathematical process of converting data of any size into data of fixed length known as the ‘hash’ (alternative names include message digest, hash codes, hash sums or hash values).
Hashing operates in one direction only, making it impossible to deduce the original data from the resultant hash. The intention of hashing is not to preserve the contents of the data but to create a unique identifier for every single piece of data. When a file is published on the internet, the author may choose to publish the hash value for that file. For instance, here is some information published by the GnuPG encryption software authors on their website:
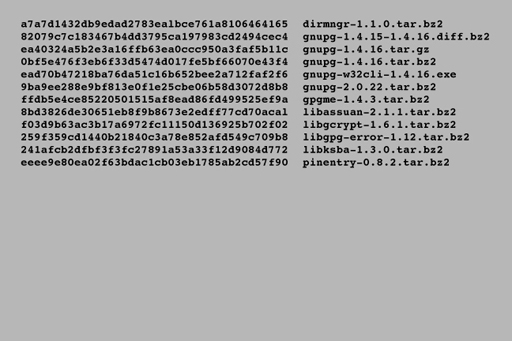
This shows a number of letter and number combinations.
Each long line of numbers and letters on the left is a hash (in this case from a hashing program called SHA-1), the text on the right is the name of the file. If you download one of these programs, you can then run your own copy of SHA-1 on your download and obtain a hash – if your file exactly matches the original the two hashes will be identical.
A variation of a single bit of data between two otherwise identical files will result in vastly different hash values, so any edits to a file between two hashing operations will result in different hash values revealing that the data has been tampered with and should not be trusted.
A large number of hashing algorithms have been developed; the most widespread are algorithms called MD5, SHA-1 and SHA-2. Although MD5 and SHA-1 are in common use, both have been found to be flawed. Under certain circumstances ‘collisions’ can occur where two pieces of different data can generate the same hash value (albeit under specifically controlled conditions).
This weakness in the MD5 hashing algorithm has been used in malware targeting Microsoft Windows computers. Since neither algorithm can be guaranteed to generate unique hashes they can be considered ‘broken’ and should not be used. The United States government requires all hashes to be generated using the newer SHA-2 algorithm which has not shown any such weaknesses.
Next, you’ll find out how digital signatures and certificates use cryptography.
3.2 Digital signatures and certificates

Transcript
Hashing can show that data has not changed in transmission, but on its own cannot demonstrate that the data originated with its supposed author. To do that, a digital signature should be used.
Digital signatures use the sender’s private key to encrypt the hash. Previously, you learned how documents can be encrypted with a public key which can be used by anyone, but can only be decrypted using the corresponding private key known only to the owner.
Encrypting data using the private key isn’t suitable for securing secrets (as anyone with access to the public key could decrypt it). However, it is perfectly possible to encrypt a hash using the private key so that the hash can be decrypted and compared by anyone possessing the matching public key. This can be used to provide authenticity since the encrypted hash must have been produced by the holder of the private key – hence the name digital signature.
Case study 1: Alice and Bob
Imagine that Alice wants to send the company’s quarterly profit statement to Bob, who works in the financial markets, for public announcement. Both Alice and Bob want confidence that the quarterly profit statement has not been intercepted by Eve en route and altered.
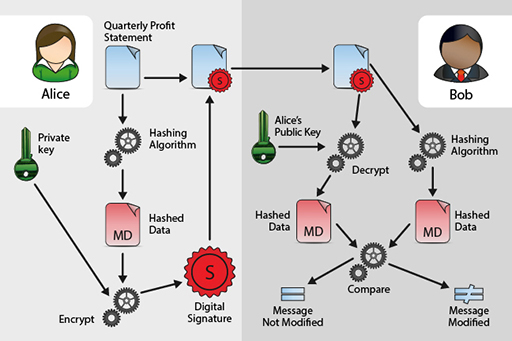
This is an illustration of how Alice would send her quarterly profit statement to Bob. It shows the different stages it would go through.
Alice will therefore produce a hash of the quarterly profit statement and then encrypt this with her private key to produce a digital signature. Alice will then include the digital signature with the quarterly profit statement and send this to Bob. Alice may also encrypt the quarterly profit statement and the encrypted hash with Bob’s public key so that all details of the message remain secret.
Upon receipt Bob will, if Alice sent the message encrypted with his public key, decrypt the message using his own private key. This will then reveal the encrypted digital signature. He will decrypt the digital signature using Alice’s corresponding public key to reveal the hash. Bob will then calculate a hash of the quarterly profit statement and then compare this with the encrypted hash that he received from Alice. If the hashes are the same then both Bob and Alice can be confident that the quarterly profit statement was not altered en route by Eve.
Digital signatures do not provide us with complete confidence of the author or originator. Just because a digitally signed document claims to come from a person or a company it doesn’t mean that it actually did, a malicious individual could masquerade as the sender by producing their own public/private key pair and using these to produce digital signatures.
Case study 2: Alice and Bob
Imagine that a digitally signed business invoice arrives in Alice’s mailbox from Bob. She uses Bob’s public key from a public key server to decrypt the digital signature and validate the business invoice by comparing the hashes. Alice, assuring herself that it is Bob (as the hashes are the same), follows the instructions and transfers money to the account details in the business invoice.
A few weeks later, Alice receives an angry email from Bob because he has not been paid. After a bank investigation she finds out that she had transferred the money to Eve by mistake – so what went wrong?
It’s clear that the business invoice and the associated signature did not come from Bob, instead the signed business invoice actually came from Eve. Eve used Bob’s personal information to create a new key pair in Bob’s name and placed a copy of the public key on a public key server. Eve then used her corresponding private key to sign the business invoice and send it to Alice.
Alice, convinced that the document was a genuine business invoice from Bob (as it included what she believed to be his digital signature), followed the instructions and paid money into an account belonging to Eve – oh dear!
Digital certificates help us overcome this problem. A digital certificate is a means of binding public keys to their owner. These are issued by Certificate Authorities (CAs) who validate the owners of public keys. The CA does this by validating (through various processes), the identity of the owner of the public key. Once it has done this it will bind the public key to a digital certificate and sign it using its private key to attest authenticity. The CA’s public key is available to all parties who need to validate the CA’s assertion of public key ownership.
However, digital certificates still require a chain of trust to confirm that the certificate belongs to the person or organisation that you think it does and have not been compromised. Criminals have been known to obtain certificates that were then used to sign software that included malware. Stolen certificates have also been used to sign malware. For example, the Stuxnet code was signed with certificates that belonged to Realtek Semiconductor and JMicron Technology Corp.
Case study 3: Alice and Bob
So, using a Certificate Authority prevents Eve from creating a key pair of her own, and claiming that the corresponding public key is Bob’s. If Eve were to now send a business invoice appearing to be signed by Bob, when Alice uses Bob’s validated public key to try and decrypt the hash and compare them, this will not work; she would know that something was wrong, and (hopefully), not transfer money to Eve.
Note that scams are increasingly being reported where fake invoices are being sent to businesses, or a senior manager is being impersonated to persuade people in the business to make payments to the scammer’s account.
All businesses should ensure that all managers, directors etc. have private and public encryption keys, and that their public keys are stored and displayed locally to be used by everyone in the business.They must use their keys in order to sign and validate all non routine instructions for making payments. This is about the only way to avoid the scam reported by the BBC:
‘Hey, the deal is done. Please wire $8m to this account to finalise the acquisition ASAP. Needs to be done before the end of the day. Thanks.’
The employee thought nothing of it and sent the funds over, ticking it off his list of jobs before heading home.
But alarm bells started to ring when the company that was being acquired called to ask why it had not received the money.
An investigation began - $8m was most definitely sent, but where to?
For the rest of the report see: https://www.bbc.co.uk/ news/ technology-49857948
3.3 Encrypted network connections

This shows two people shaking hands (it shows their hands and part of their forearms only). There are symbols around them, for instance @, an envelope, a speech bubble and a padlock.
As you learned earlier, web traffic is not encrypted by default. Web pages pass as plaintext across the internet and are vulnerable to interception.
Obviously, this was a problem when companies first began to consider online shopping. At first companies had to ask customers to browse online and then make a telephone call so the company could accept credit card information.
The solution came in 1995 when the web browser pioneer Netscape announced the Secure Socket Layer (SSL) protocol, which has now been replaced by Transport Layer Security (TLS)), which allows web browsers to exchange secure data. It is supported by all modern browsers and allows confidential information to be exchanged over an insecure link.
TLS/SSL
TLS/SSL uses a combination of asymmetric and symmetric encryption to exchange data. When a web browser connects to a server and requests a secure communication the two computers first engage in what is known as a handshake and agree how future communications will be conducted, including the type of cryptography that will be used.
After agreeing how to communicate, the server transmits its own public key and a digital certificate of authenticity to the user’s computer which checks that the certificate is genuine and has not expired. If the certificate is genuine, the user’s computer then generates a master secret, encrypts it with the copy of the server’s public key and sends that to the server.
The server decrypts the encrypted master secret with its own private key. Both the server and the computer now have copies of the secret and use that to generate identical copies of a symmetric encryption key. Crucially, the key itself has not been transmitted across the network.
Each computer now informs the other that all other transactions in this session will be conducted using the symmetric key (called the session key), by sending ‘finished’ handshake messages using each other’s session keys. The two computers can now perform the secure transaction itself, including sensitive information such as bank account details, addresses, credit card numbers and receipts using the high-speed symmetric key.
At the end of the secure session, the two computers say goodbye to one another and each deletes their copies of the symmetric session key. If the user starts another secure session a completely new key will be used.
TLS/SSL is now used by most websites. It is an automatic process between the browser and the server that keeps data safe in transit. It doesn’t mean that any site is genuine. Any website, including criminal ones, can now implement TLS/SSL for free. However, its use means that end users can benefit from the confidentiality and integrity provided by cryptography without having to worry about the technical details of configuring their software or managing keys.
In the next section you’ll see TLS/SSL in action.
3.4 How secure is your browsing?
This shows a padlock with a combination lock, attached to a chain.
Web browsers have made it easy to determine if a website is using TLS/SSL by:
- Making all secure addresses begin ‘https://’ (rather than ‘http://’) with the s standing for ‘secure’. Examples include Gmail, at https://mail.google.com/; Google defaults to Google Safe Search at https://www.google.com/, which means that your search requests and results cannot be seen by others.
- Showing a closed padlock symbol in or near the top of your browser window.
Activity 2 Your own browsing security
Visit a website that you use regularly (it could be this one!) and find a page that you would expect to use a secure network connection. A common example would be your webmail account or online banking website. Use your browser’s help feature and click on the padlock icon to find out about its meaning.
Research browsing security online. You might find that your browser shows different versions of the padlock to highlight potential problems with the secure connection.
Encrypted DNS
Up until 2019, the DNS information requested was sent as plain text and could be intercepted even when the data being sent or requested was encrypted. From 2019, it has become possible for DNS requests to be encrypted. In a Firefox browser go to settings, then network settings and select the enable DNS over HTTPS checkbox.
As mentioned in Week 4, Chrome 78 is also experimenting with this feature, which can be enabled by browsing to ‘chrome://flags/’ in your Chrome browser, searching for ‘dns-over-https’ and enabling this feature. You will have to restart the browser for this change to take effect.
4 Week 5 quiz
This quiz allows you to test and apply your knowledge of the material in Week 5.
Complete the Week 5 practice quiz now.
Open the quiz in a new window or tab then come back here when you’re done.
5 Summary of Week 5
This shows a number of coloured blocks, numbered either 0 or 1, on top of each other. This collection of blocks hovers over a laptop.
This week has focused on cryptography – a key security technique that allows you to ensure confidentiality and integrity of your data.
You have learned how to use cryptography tools to secure your email and can explain the use of cryptography in common applications, such as the world wide web. As a result, you should now be able to identify where you could use cryptography to improve the protection of your digital life. One example of this, the use of cryptography to protect computer networks, is the topic for the next week of the course.
You can now go to Week 6: Network security.
Acknowledgements
This course was written by Arosha K. Bandara.
Except for third party materials and otherwise stated in the acknowledgements section, this content is made available under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 Licence.
The material acknowledged below is Proprietary and used under licence (not subject to Creative Commons Licence). Grateful acknowledgement is made to the following sources for permission to reproduce material in this course:
Images
Figure 1 © Bletchley Park Trust (via Getty Images)
Figure 2 © Bob Lord - Licensed under Creative Commons Attribution-Share Alike 3.0 via Wikimedia Commons - http://commons.wikimedia.org/wiki/File:Enigma-plugboard.tif#mediaviewer/File:Enigma-plugboard.tif
Figure 3 © agsandrew (via Shutterstock Photos)
Figure 5 © peterhowell (via iStock Photo)
Figure 6 © GlobalP (via iStock Photo)
Figure 7 © blackie (via iStock Photo)
Figure 10 © Wavebreak (via iStock Photo)
Figure 11 © choicegraphx (via iStock Photo)
Figure 12 © Vertigo3d (via iStock Photo)
Audio visual
2.1 and 2.2 © The Open University
Every effort has been made to contact copyright owners. If any have been inadvertently overlooked, the publishers will be pleased to make the necessary arrangements at the first opportunity.
Don't miss out:
1. Join over 200,000 students, currently studying with The Open University – http://www.open.ac.uk/ choose/ ou/ open-content
2. Enjoyed this? Find out more about this topic or browse all our free course materials on OpenLearn – http://www.open.edu/ openlearn/
3. Outside the UK? We have students in over a hundred countries studying online qualifications – http://www.openuniversity.edu/ – including an MBA at our triple accredited Business School.
Copyright © 2015 The Open University
