4.3.4 Security devices
Some of the devices in the security architecture that can be used to control access, inspect content, and enforce policies include:
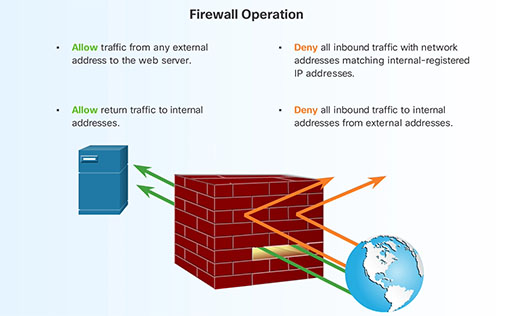
- Firewalls – A firewall creates a barrier between two networks. The firewall analyses network traffic to determine if that traffic should be allowed to travel between the two networks based upon a set of rules that have been programmed into it, as shown in the following animation. (Click on the full screen button for a clearer view.)
Download this video clip.Video player: screen_4_3_2_2.mp4

Interactive feature not available in single page view (see it in standard view).
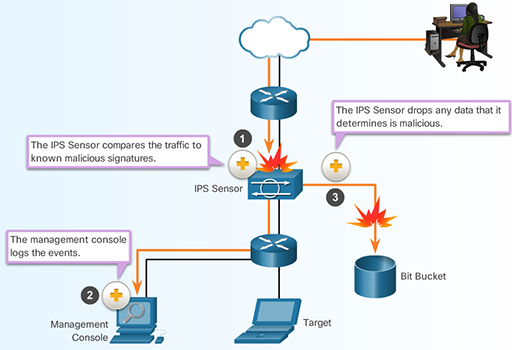
- Intrusion prevention systems (IPS) − The IPS monitors the activities on a network and determines if it is malicious. An IPS will attempt to prevent the attack by dropping traffic from the offending device or resetting a connection. Figure 22 shows more about how an IPS works.