1.3 Risk analysis in practice
Let’s think about a practical example of how qualitative risk analysis could be done for Lewis’s information assets.
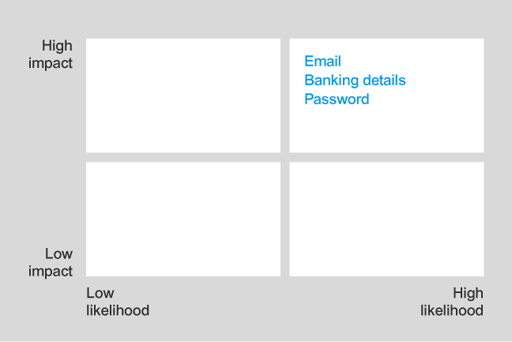
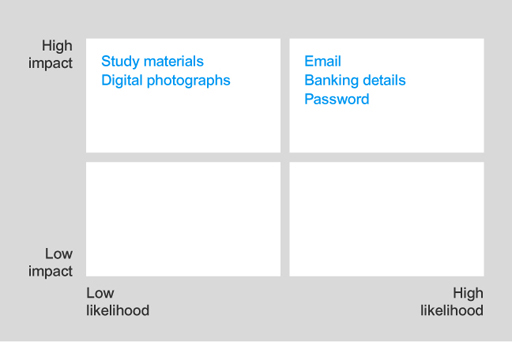
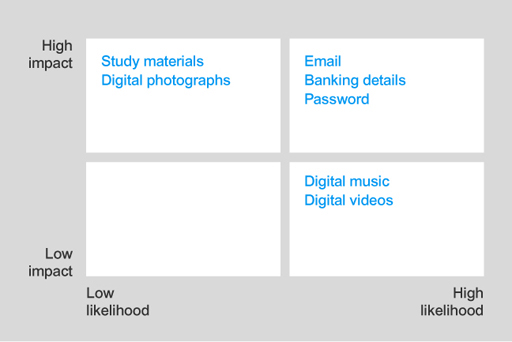
Any successful attack on email, banking details and password information will have high impact and there is a high likelihood that these attacks will be targeted due to their high value. So they should go in the high-high box.
An attack that affects the study materials or digital photographs will have high impact, but there is a low likelihood given that these assets have minimal financial value to an attacker. These should be placed in the high-low box.
An attack on the digital music or videos will have low impact, since these can be downloaded again easily. However, this will have high likelihood because these assets can be easily copied and sold, this making these attractive to an attacker. Therefore, they go in the low-high box.
Conducting a risk analysis is an important part of protecting your information assets. Following Lewis’s example consider your own list of information assets and carry out a similar risk analysis to determine the impact and likelihood of attack for each type of information.