2.2 Cloud architecture
SOA is well placed to take advantage of a recent development known as ‘cloud technology’ based on what is often termed ‘the cloud’. Cloud technology has changed how organisations use technology to provide computing services. However, there is a lack of clarity as to what the term will really come to mean. Some definitions restrict the cloud to mean that virtual servers are made available and used over the internet, but more generally the cloud is seen as consisting of a wide range of different resources.
The National Institute of Standards and Technology (NIST, 2013) provided a wider definition of cloud computing:
Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g. networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.
Cloud computing is the practice of delivering computing services – servers, storage, databases, networking, software, analytics and more – on-demand over the Internet. It is a means of providing computing services as a utility to consumers in the same way as other utilities such as gas and electricity. Companies offering these computing services typically charge for cloud computing services based on usage.
You might take the view that whereas SOA provides services on a network, the cloud extends the principle to other resources such as processing power and storage facilities and is not limited to the provision of services. There are, of course, quite a lot of details that are not covered here. How resources are charged for, made secure, ‘cleaned’ after use, etc. are just some of the aspects that need to be considered.
Activity 3 Benefits and potential problems of using cloud architecture
Take a look at the Amazon Web Services (AWS) website What is Cloud Computing? [Tip: hold Ctrl and click a link to open it in a new tab. (Hide tip)]
What do you see as the benefits and potential problems of using cloud architecture?
Answer
Benefits of the cloud
There are numerous benefits claimed for the cloud. Here’s one possible list – you may have come up with something different.
1 Cost
A major benefit claimed by many cloud service providers is cost. Data centres are expensive to build and operate, and cloud technology can result in significant reduction in the infrastructure (capital expenditure) and operational costs.
For example, if an IT project requires significant investment in equipment, or investment in a building to house the equipment, the organisation will have to make a case for the capital expenditure and approve funding. It could take months just to get approval and then the actual work must be completed. The cloud alternative could be set up within a few days and be paid for from an operational budget. For a small organisation the running costs could be covered by the cash flow generated by the application.
2 Elasticity
One of the core benefits of the cloud is elasticity – that is, the ability to automatically expand resources as demand increases and shrink resources as demand wanes. The expectation is that cloud applications and services are continuously monitored to ensure they are responding to requests and that they perform within operational limits. Should applications or service fail to respond to a request, or should it exceed its performance limits, a new instance of that applications or service will be launched, either to replace the failed instance or to supplement the existing one.
3 Resilience
Another one of the core benefits of the cloud is resiliency – that is, the ability of cloud applications and services to recover quickly and continue operating even when there has been an equipment failure, power outage or other disruption. Such failures may originate at any of the major components in a cloud architecture: (1) the servers hosting the application or service; (2) the network interconnecting them, local or wide-area connections; or (3) the application or service itself.
Resiliency is often achieved through the use of redundant components, subsystems, systems or facilities. When one element fails or experiences a disruption, the redundant element takes over seamlessly and continues to support computing services to the user base. Ideally, users of a resilient system should not be aware that a disruption has even occurred.
Risks of the cloud
Moving applications, services and data from a closed private environment onto the public cloud presents a complex set of issues for developers. Instead of dedicated IT equipment under close supervision, applications, services and data are hosted on shared resources with little direct control of where those resources are located.
Arising from this move to shared resources, here’s one possible list of risks – you may have come up with something different.
1 Unauthorised access to applications, services and data
Once an organisation moves applications, services and data onto a public cloud, they now have to worry about not only unauthorised access by their own staff but also the vendor’s staff. More people have access to the applications, services and data, and systems that support these, which means the organisation has to extend trust to people they have no control over.
The risk of intrusion by other organisations resulting in the loss or theft intellectual property, for example, also increases when they use a public cloud.
2 Legislation and regulation
Organisations that are subject to data security legislation are required not only to protect the data, but also typically required to know: (1) Where the data resides; (2) Who is allowed to access it; and (3) How it is protected.
If an organisation moves the processing and storage of data that it is required to protect onto a public cloud, then it is relying on a cloud service provider to maintain their compliance. If the organisation does not have adequate legal protections, then it may be liable when there is a data breach at the cloud service that exposes the organisation’s data.
In other words, although an organisation’s data is residing on a provider’s cloud, the organisation is still accountable to their clients for any security and integrity issues that may affect their data and therefore the organisation must know the standards and procedures the provider has in place to mitigate the organisation’s risk.
Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable hardware, software and network computing resources and services that can be rapidly provisioned and released with minimal management effort or service provider interaction.
NIST (2013) defines five essential characteristics:
- On-demand self-service – A consumer can automatically and unilaterally provision computing capabilities such as server time and network storage as needed, without requiring human interaction with each service provider.
- Broad network access – Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g. mobile phones, tablets, laptops, and workstations).
- Resource pooling – The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. There is a sense of location independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify location at a higher level of abstraction (e.g., country, state, or data enter). Examples of resources include storage, processing, memory, and network bandwidth.
- Rapid elasticity – Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. To the consumer, the capabilities available for provisioning often appear to be unlimited and can be appropriated in any quantity at any time.
- Measured service – Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g. storage, processing, bandwidth, active user accounts). Resource usage can be monitored, controlled, audited, and reported, providing transparency for both the provider and consumer of the utilized service.
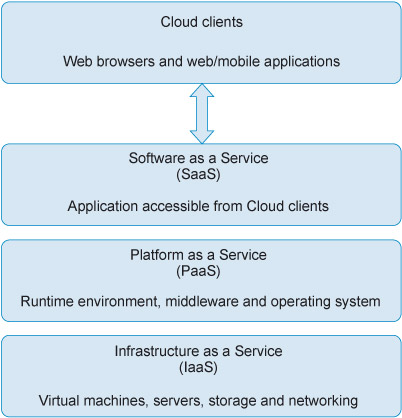
NIST (2011) defines three service models:
- Software as a Service (SaaS) – provides applications designed for end-users, delivered over the web.
- Platform as a Service (PaaS) – provides tools and services for developing and deploying applications.
- Infrastructure as a Service (IaaS) – provides servers, storage, network services and virtual machines.
As these service models offer increasing levels of abstraction they are often depicted as a stack of service layers – infrastructure, platform, and software-as-a-service layers – though they may not be physically implemented by a tiered architecture (Figure 3).