3.2 Important terminology and information for making the most of this section
Before we move on to consider specific issues of network security, I need to introduce some important terms that I shall use when describing how data is stored, processed or transmitted to other locations. These are:
Confidentiality, in terms of selecting who or what is allowed access to data and systems. This is achieved through encryption and access control systems. Even knowledge of the existence of data, rather than the information that it contains, may be of significant value to an eavesdropper.
The integrity of data, where modification is allowed only by authorised persons or organisations. The modifications could include any changes such as adding to, selectively deleting from, or even changing the status of a set of data.
The freshness of data contained in messages. An attacker could capture part or all of a message and re-use it at a later date, passing it off as a new message. Some method of incorporating a freshness indicator (e.g. a time stamp) into messages minimises the risk of this happening.
The authentication of the source of information, often in terms of the identity of a person as well as the physical address of an access point to the network such as a workstation.
The availability of network services, including security procedures, to authorised people when they are needed.
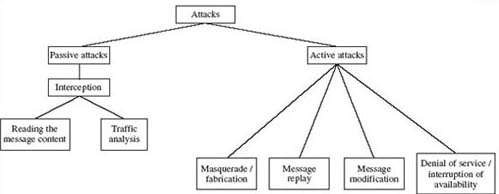
In general, attacks on data networks can be classified as either passive or active as shown in Figure 2.
This is a suitable point at which to listen to the audio track ‘Digital dangers’. This provides some additional perspectives to supplement your study of this unit.