2.2 How did it work?
WannaCry belongs to a class of malware known as ‘worms’. As you saw in Activity 2, these are stand-alone, self-replicating programs that spread through network connections, accessing uninfected machines and then hijacking their resources to transmit yet more copies across the network.
Similar to a typical malware worm, WannaCry contains an infection module and a ‘payload’. The infection module is responsible for spreading the malware, while the payload module undertakes the actual attack. The payload module of WannaCry locks data files using encryption and handles the process for demanding a ransom. Once the malware is executed, both modules work at the same time.
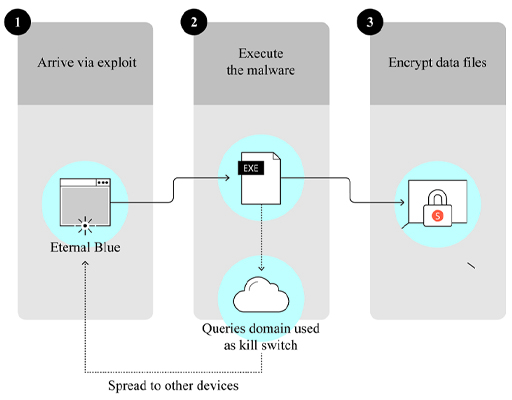
However, compared to other worms, WannaCry spread much more quickly. How did it achieve this rapid spreading? The security experts who analysed the malware believed it employed a powerful hacking tool known as EternalBlue. This exploited a vulnerability in Microsoft Windows operating systems, allowing the malware to install and execute itself on a vulnerable computer without any action from the computer user.
The vulnerability exploited by EternalBlue existed in almost all versions of Windows operating systems including Windows XP, Windows Vista, Windows 7, Windows 8 and Windows 10, as well as some server and embedded versions. EternalBlue is believed to have been developed by the US National Security Agency (NSA) and then stolen by a hacking group known as the Shadow Brokers, who had been trying to sell it on the black market for a number of months before the WannaCry attack (Woollaston, 2017).
EternalBlue exploited a defect in Microsoft’s implementation of the Server Message Block (SMB) protocol, which allows applications on a computer to access files and services on other computers. This remote access to files and services usually happens within the same local area network (LAN), but it is possible for a computer outside the LAN to access files and services too if firewall settings allow it to do so (e.g. through the internet). However, allowing computers outside your LAN access will significantly increase the risk of attacks.
Once the WannaCry malware infects a computer, it will scan all computers within the same local network and some computers on the internet for the EternalBlue vulnerability. When vulnerable computers are found, it installs itself on these computers and executes the malware. Therefore each infected computer becomes an attacker and will keep looking for new victims. This is how the malware can spread so quickly. Figure 1 illustrates how WannaCry infects a computer.
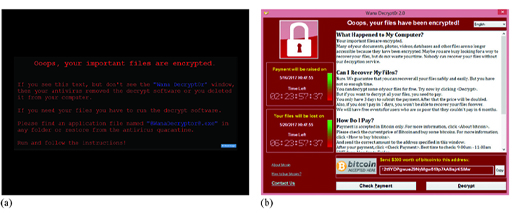
Once installed, the payload module will look for a range of data files, including documents and images, on the infected computer and encrypt them using a complex combination of symmetric and asymmetric methods to ensure the files cannot be unencrypted easily. It then executes the ‘Wana Decrypt0r 2.0’ and displays a black Windows desktop background image with instructions in red text. Figure 2(a) shows the desktop background image, while Figure 2(b) shows the interface of the ‘Wana Decrypt0r 2.0’. This tells the victims that their data files have been encrypted and that they have to pay a ransom of $300 to a given address if they want to recover all their files. The ransom is to be paid in bitcoin, which is a digital currency but can be bought with real money at bitcoin exchanges. The interface also has three-day and seven-day countdown timers – these are used to create a sense of urgency, as the note in the interface states that the ransom will be doubled after three days and the data files will be deleted after seven days. To convince the victims that the ‘Wana Decrypt0r 2.0’ can recover their files, it offers a free demonstration of a few files being decrypted.
When the attack broke out, security experts generally advised users not to pay the ransom, as it was not guaranteed that the files would be recovered after payment (Baraniuk, 2017). It might also encourage more attacks if attackers saw this as an easy way to make money.