4.4 Phishing
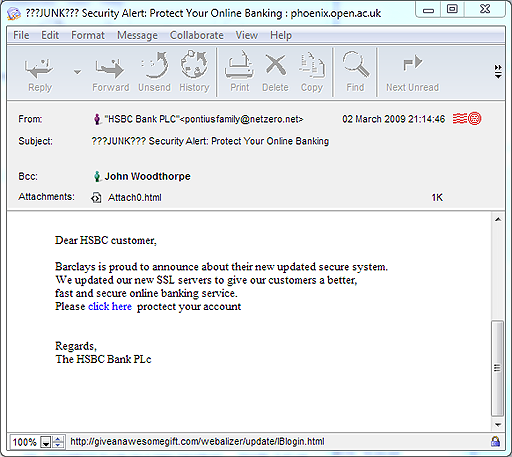
A particular kind of hoax message aims to persuade users to disclose private information such as their credit card details and PIN (Personal Identification Number). This is described as phishing. The recipient of the message may be directed to a hoax website where they are requested to part with their details. Figure 10 shows an example of an email that I received.
Activity 9 (exploratory)
Looking at the email in Figure 10, what warning signs are there that might alert you to the fact that this is an attempt at phishing?
Comment
Below are the warning signs I noted when I received this email.
- Although the sender’s email address is described as ‘HSBC Bank PLC’, the actual address – pontiusfamily@netzero.net – appears to have nothing whatsoever to do with the bank; instead it sounds like a private email address.
- The email address of ‘netzero.net’ refers to an internet service provider – NetZero – based in the USA. I can’t imagine that a bank based in the UK would contact me from an email address supplied by an internet service provider in another country.
- There is confusion about which bank this email is meant to be from, as the message refers to both HSBC and Barclays.
- The message exhibits poor grammar and spelling – ‘proctect’, for example. I think it unlikely that such errors would be present in genuine messages from my bank.
- The message is not addressed to the recipient (me) by name. This can indicate a message sent randomly to large numbers of email addresses.
The above points, along with the fact that I don’t actually manage my bank account online, convinced me not to follow the instructions in the message. Yet despite all these warning signs, some people do hand over their details in this way.
It’s very important not to click on any links in these sorts of messages. Even if you don’t enter your account details, making any response at all may confirm to the phisher that your email address is valid, leaving you open to further hoaxes and spam. Simply clicking on a link also risks your computer being infected with malware that could distribute the same message to all the email addresses – including those of your work colleagues, family and friends – stored on your computer.
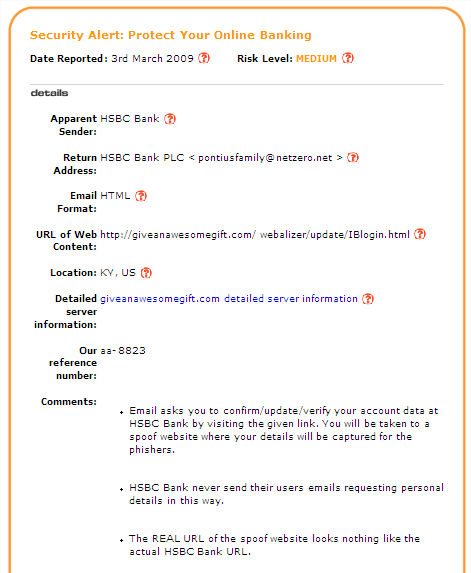
One way to check this kind of message is to position your mouse pointer over the link (‘Click here’ in the Figure 10 example) and look at the web address that appears either as pop-up text or at the bottom of the message window. If it seems to be unrelated to the sender of the message then you should be even more suspicious. After receiving the email shown in Figure 10, I searched online and found a reputable site (millersmiles.co.uk) that contained the information shown in Figure 11.
Most phishing messages try to get you to provide some personal information (Figure 12). Clearly those trying to get your online banking details are aiming to get access to your money. However, others could be trying to access your email, blog, instant messaging or online auction accounts (if you have any), then use these accounts to distribute more phishing emails.
If you have a job that provides you with an email account then you have probably also seen messages claiming to be from your company’s IT department, asking you to enter your username and password into a website to reset your email account. I’ve certainly had them sent to my Open University email account. As with requests for you to disclose your financial details, you should be careful when disclosing your username and password. A phone call to the relevant people in the company should be sufficient to find out whether or not the request is genuine.