Unit 3: Prevention
| Site: | OpenLearn Create |
| Course: | Introduction to Safeguarding in the International Aid Sector |
| Book: | Unit 3: Prevention |
| Printed by: | Visiteur anonyme |
| Date: | Friday, 27 February 2026, 11:01 PM |
Table of contents
- Introduction
- 3.1 Safeguarding risks and preventative measures
- 3.2 What is a risk assessment?
- 3.3 Safe recruitment
- 3.4 Recruitment
- 3.5 Safe recruitment
- 3.6 Safe selection and recruitment in your organisation
- 3.7 Codes and standards
- 3.8 International safeguarding standards
- 3.9 Empowering beneficiaries and service users
- 3.10 How to safely use images and the personal data of beneficiaries
- 3.11 What safeguarding measures are organisations implementing to prevent harm?
- 3.12 Unit 3 Knowledge check
- 3.13 A mid-course review
Introduction

In Unit 3, we return to the Safeguarding Cycle introduced to you in the last unit. In the previous unit we looked at identifying the different types of harm. In this unit we will be looking at putting in place preventative safeguarding measures.
The content for Unit 3 will look specifically at:
- Preventing exploitation, abuse and harassment by identifying safeguarding risks
– Action: Developing Risk Assessment. - Preventing those with intent to harm from working or representing our organisation
– Action: Developing safe selection and recruitment practices. - Being clear about what is appropriate and inappropriate behaviour for organisational staff and representatives
– Action: Developing an organisational Code of Conduct. - Reducing risk of harm in the use of images and data practices
– Action: Developing safe use of images and personal data.
3.1 Safeguarding risks and preventative measures
It is essential to be able to identify safeguarding risks and understand how to develop a risk assessment to support you in putting in place safeguarding measures to mitigate against those risks.
|
Activity 3.1 What is a safeguarding risk?
A risk can be described as something that exposes someone to danger and harm. A ‘safeguarding risk’ would be when organisations expose their staff, representatives and beneficiaries to danger and harm. To understand this, read the case study below and then answer the questions that follow it in your learning journal. Case study Organisation X is setting-up a three-year programme called ‘Hear our Voices!’ in Country Y, a country with a large, displaced population due to heavy flooding. This programme is to empower communities to receive food parcels in Year 1, develop new farming techniques in Year 2 and in Year 3 to build up their skills to campaign for better support from local government. The programme is funded by the institutional donors that have signed up to strict safeguarding standards. The project will benefit children, women and older people. These communities suffer from low literacy and high domestic violence rates. Donors expect quarterly reports with photographic evidence of outputs and outcomes. You anticipate that you will be recruiting new staff (paid, part-time and full-time) and associated personnel (people who represent your organisation in some way but who may not be employees) such as consultants, researchers, volunteers and community-based workers. Questions:
|
3.2 What is a risk assessment?
Once you have identified the risks related to this programme, it is important to carry out a risk assessment to gauge the risks and think of the mitigation measures to prevent harm and danger to your organisation as well as to beneficiaries of the ‘Hear our voices’ programme.
A risk assessment is a systematic process of evaluating the dangers that may occur.
![]()
Watch the video animation above ‘How to Complete a Risk Assessment’. This outlines the steps you will practise when completing your own risk assessment in the activity that follows below.
|
Activity 3.2 Using a risk assessment tool Once you’ve watched the video, complete this downloadable risk assessment template in relation to the ‘Hear our Voices’ programme. Consider all risks and mitigation measures you have identified. You may include ones not considered in the video. We will cover these risks in the different parts of this course. A reminder of the stages is below: Step 1: Identify risks
Step 2: Assess each risk
It is important to monitor the risk assessment and this responsibility does lie with programme managers. |
In the next section, we will look at the first of these mitigation measures that is, safe recruitment and selection of staff and associated personnel.
3.3 Safe recruitment

© Sudtawee Thepsuponkul / Shutterstock
In order to prevent prospective staff and associated personnel from harming each other or the beneficiaries for this programme, it is important to consider how they are recruited and selected in the first place.
By putting in place robust selection and recruitment processes, your organisation will be a safer organisation to all those it has contact with.
This requires an understanding of how and why potential recruits might pose a risk, and what steps can be put in place to mitigate and prevent these risks.
Even if your organisation already has a Recruitment Policy, you should use this opportunity to critically review what it contains, whether it is fit for purpose, and whether it’s applied rigorously and consistently.
|
Activity 3.3 Identifying the potential risks associated with different roles in your organisation In the example you have just used to practise your risk assessment skills there would have been a range of staff and associated personnel involved. This may include:
- Consultants to build capacity on livelihoods. In this activity you will now focus on your own organisation. Using the table below, make a list of everyone who is employed, engaged or represents your organisation in any way. Then fill in the other columns – we have filled in a few in advance as examples. It is important not to just focus on formal appointments, although they are vital, you also need to think as broadly as possible about all those who work, volunteer or are associated with your organisation. Making this list will continue to be useful because, as you will explore later, recruitment is only the start of prevention in relation to the risks you are identifying. For your information, the following applies: i. Direct contact – usually face-to-face or online ii. Indirect contact – when the person has access to images or personal information iii. Your organisational duty to safeguard is not diminished just because someone is not paid, so add everyone you know who represents or is associated to your organisation Complete all the headings for each person identified. Use this downloadable PDF version of this table to help you complete the table.
|
3.4 Recruitment
|
Activity 3.4 The power imbalance during recruitment Watch the video above about a woman’s experience of trying to get a job with an organisation working in the Ebola crisis in the Democratic Republic of Congo.
When you have watched the video, consider this question:
Make some notes in your learning journal. |
3.5 Safe recruitment
![]()
Hasan is a Human Resources Manager and is very interested in safe recruitment, but he has a question.
Watch the video above to find out more about his question and the answer that Aneeta gives.
3.6 Safe selection and recruitment in your organisation
Recruiting safely for your organisation is an essential safeguarding measure to prevent harm and abuse from happening as a result of any potential misconduct from occurring.
|
There are many parts within this topic, and we will go through them in the next few sections. Before proceeding, think about the following questions:
|
|
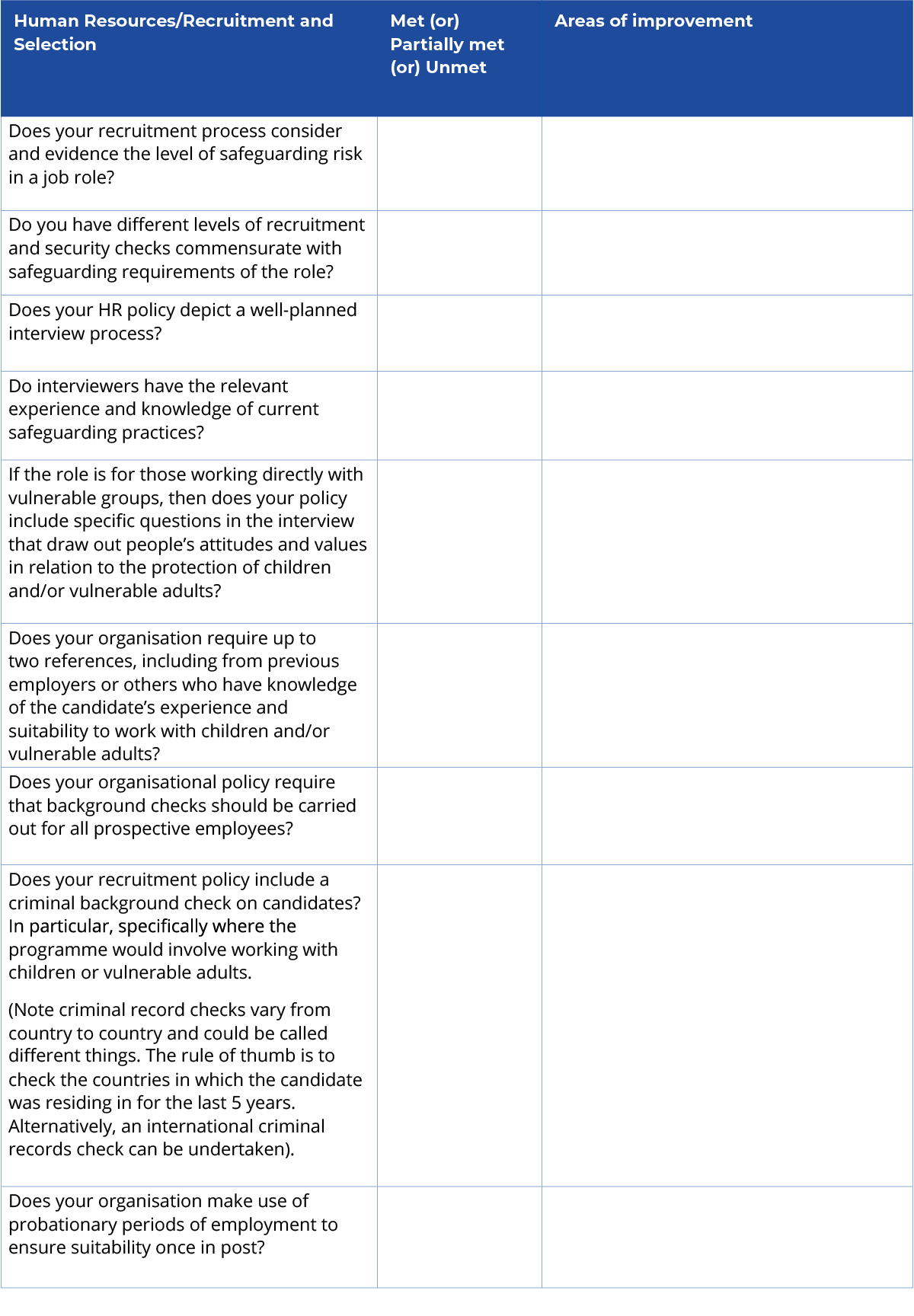
Activity 3.5 Recruitment through a safeguarding lens This activity demonstrates the use of a safeguarding lens (like using spectacles) for the recruitment of staff and associated personnel. This is important if you are a safeguarding lead as you may be able to influence your organisation to strengthen recruitment practices. For those of you who work in HR or who are recruiting managers, this exercise will be very relevant. It may be that to be able to fully complete this activity and identify areas for improvement you will need to discuss it with other people in your organisation. You will remember you were introduced to the international safeguarding standards in Unit 2 of this course. We will return now to the HR principle under FCDO’s Enhanced Due Diligence Standards, which will help you to gauge any risks on current organisational practices. Study the table below, then download this Selection and Recruitment Checklist and complete the second and third column.
© (Adapted from FCDO’s Enhanced Due Diligence Standards. Reproduced under the terms of the OGL) |
![]()
Want to find out more?
If you are interested in learning more about safe recruitment, follow the links below:
- There are now international voluntary disclosure schemes in the international sector for agencies to share information if they have concerns about any worker. This is to try and prevent perpetrators from being employed in different agencies.
- Webinar on Safe Recruitment (December 2020).
- Recruitment Guidelines.
- If your organisation receives funding from Department of Foreign Affairs and Trade (DFAT), this resource may be useful on the need to obtain criminal records checks.
- If you work with child beneficiaries, this resource from the NSPCC may be helpful.
3.7 Codes and standards
There is an expectation that all staff will adhere to certain standards of behaviour. These standards should be laid down in every organisation’s Code of Conduct.

© Rei Imagine / Shutterstock
Recruitment needs to be backed-up by safe working practices and an expectation that all staff will adhere to certain standards of behaviour. Collectively, these will normally be enshrined in a ‘Code of Conduct’ which everyone in the agency must sign up to.
In this section, you will explore why establishing such working practices are important, be introduced to international standards and consider how these issues can be made relevant to your own organisation.
Why do we need rules around behaviour?
To understand why such rules are so essential it is important to understand the behaviour of those who will be looking to take advantage of any weakness in your organisation’s safeguarding cycle.
|
Activity 3.6 Why do we need a code of conduct? After reading the transcript below, consider the following questions. Reflect and record your answers in your learning journal:
Tim: “I volunteered to help out with the disabled kids in this project I know… it’s usually really easy to get at these types of kids because you can touch them and be pretty confident that they can’t speak out. It turned out though this set up had some kind of code of conduct with all these rules about what I could and couldn’t do and how I should behave. Worse still, when I eventually got into the project, they never left me alone with them, not even for a minute. Although none of the children could speak, the staff had this way of communicating with them to check they were OK. I left there pretty quickly. I’ll find somewhere else that doesn’t have all these rules, you know… it should be easy.” |
![]()
Want to find out more?
For further examples of Codes of Conduct, follow the links below:
3.8 International safeguarding standards
![]()
Sherine is interested in what the international standards are and why they are important to safeguarding policy development.
Watch the video above to find out more about her question and the answer that is given.
|
Activity 3.7 International safeguarding principles This is an opportunity to introduce you to key international safeguarding principles which can be applied globally regardless of where you work. These principles should underpin standards of behaviour. The list below represents some of the key standards in the field. Has your organisation signed-up to any of these standards? If so, have they been included into your Codes of Conduct? Download the first two short documents in the links below and at least one other from the list below. If you have not officially signed up to them, can you identify standards that could inform those of your agency? Make some notes that you may want to discuss with colleagues in your organisation:
|
|
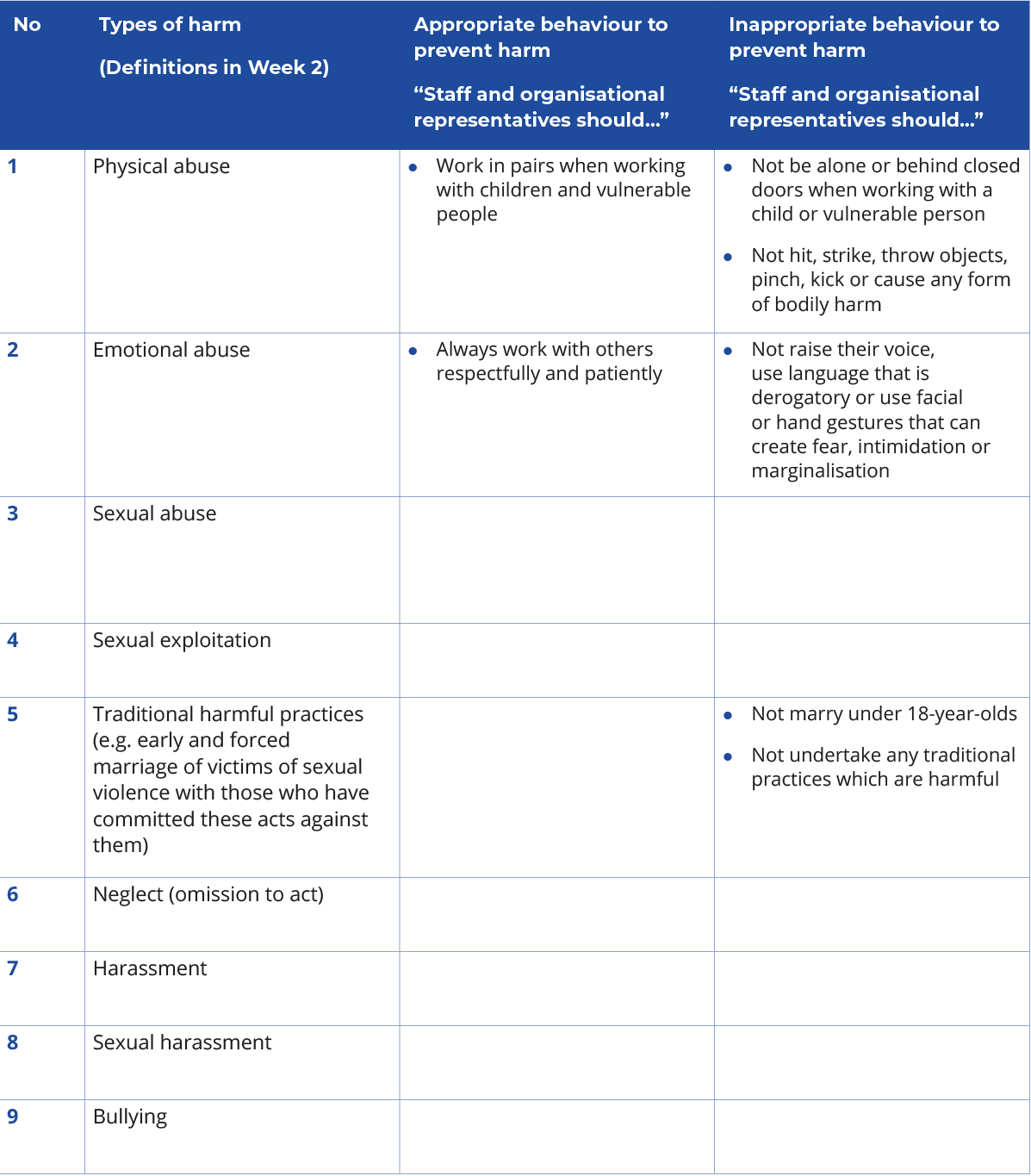
Activity 3.8 What is appropriate and inappropriate behaviour? The example of Tim in the previous section highlights the need to establish safe working practices to prevent those who work for or represent our organisations from crossing the boundaries and misusing their power in order to cause harm to another. Complete the table below by listing all forms of behaviour that are appropriate (including safe working practices) and inappropriate to prevent the various forms of harm from occurring (the list can be found in section 2.7). A few examples have already been completed. You may find that forms of appropriate and inappropriate behaviour may be stated more than once. When you consolidate your responses, just mention it once. Use the IASC PSEA 6 Core Principles which you read in the last activity as a basis for developing this. Here is a downloadable version of this table.
|
|
Activity 3.9 Reviewing the code of conduct in your own organisation To conclude your review of your own agency’s documentation, use the checklist below to review current practice. Here is a downloadable version of this table.
Once you have completed this exercise, you might find gaps in your organisation’s policies and Code of Conduct. |
![]()
Want to find out more?
If you would like to find out more about how to ensure those gaps in your organisation’s policies and Code of Conduct are addressed and strengthened, follow the links below:
- See Safeguarding Resources on Bond’s website for an example of a Code of Conduct template.
- If your organisation works with people with disabilities, this inclusive Code of Conduct might be useful.
- If your organisation works in humanitarian settings and has signed up to the Core Humanitarian Standard, the PSEA Implementation Quick Reference Handbook (downloadable below) outlines how the commitments can be used to develop safe standards for recruitment and behaviour.
- The Minimum Operating Standards for Implementing the Inter-agency Standing Committee 6 Core Principles of PSEA
3.9 Empowering beneficiaries and service users
Recruitment, meaningful codes of conduct, policies and practices are all key elements of prevention. This work can be complemented by thinking about how prevention can be further strengthened by work with your beneficiaries and their communities.
It is important that this is not a matter of passing responsibility for safeguarding to them as it is the organisation which must exercise its duty of care to keep all people safe. Empowering beneficiaries and their community to speak out is a positive protective mechanism.
For example, they need to know what your organisation’s Code of Conduct says so that they can hold your organisation to account for the behaviour of your staff and representatives.
|
Activity 3.10 Promoting your organisational Code of Conduct in communities Watch the video above, an extract from the UN video To Serve with Pride, about community members in Cambodia.
When you have watched the video, consider these questions and note your answers in the learning journal.
|
![]()
Want to find out more?
If you are interested in learning more about the participation of children in safeguarding, follow the link below.
- A Bond article on Facilitating meaningful child participation in safeguarding.
- A New Humanitarian article, 50 women accuse aid workers (September 2020), which is a reminder that the international sector still needs to do more to safeguard vulnerable women and girls.
3.10 How to safely use images and the personal data of beneficiaries
Children, vulnerable adults and staff can still be harmed when their personal information and images are taken and used without their explicit informed consent.
This exercise introduces you to the importance of safeguarding the dignity, respect and the right to confidentiality of people your organisation works with and consequences of shame and stigma that may result.
|
Activity 3.11 Case Study Now we return to the fictional case study that we were discussing earlier in section 3.2 and consider the second part of it. The fundraising team of Organisation X has engaged a freelance photographer to take some photographs of children and collect some personal information. Your web designer uploads this photo on social media with a caption below it. [Note: This is a fictional case study, and the image below has only been presented in order to illustrate poor practice]
This is Aisha Ahmed – her mother has just died of HIV, and she’s now orphaned. She was nearly recruited by armed rebels in town A in country X where she lives. She likes to attend St. Mary’s childcare. Help Aisha to stay in school by donating as little as $5 today. We at Organisation X need your support. Click here now! Consider the questions below and then read the examples that follows:
Development and humanitarian organisations have long struggled with how not to stereotype or sensationalise images of their beneficiaries. There are examples of good practice and lots of resources to look at. Example of good practice Development organisations in Ireland have committed to the Dorcas Code of Conduct on Images and Messages to ensure they avoid stereotypical or sensational images. The adoption of the Code means that aid agencies will choose images and messages that represent the full complexity of the situations in which they work, and that they will seek the permission of the people portrayed in the photos they use. What this means is that children and vulnerable adults need be fully informed of:
If there are any risks in doing so, then using a risk assessment, we have a duty to put in place mitigation measures to reduce any risk of harm. |
![]()
Want to find out more?
If you would like to find out more, follow the links below:
- The People in the Pictures, Save the Children research (2017).
- Informed Consent: Why conversations are so crucial (2019).
- Comic Relief stops sending celebrities to African Countries (2020).
- The UK Fundraising Code clearly states that organisations should not use emotive language or bombard the public with distressing images when eliciting funds (Standard 9).
- Bond: Putting the people in the pictures first
3.11 What safeguarding measures are organisations implementing to prevent harm?
![]()
Watch the video above to hear what safeguarding leads in International NGOs are doing to prevent harm from occurring.
|
Reflect on what additional points were raised in this video that may be useful to your organisation. |
3.12 Unit 3 Knowledge check
The end-of-unit knowledge check is a great way to check your understanding of what you have learnt.
There are five questions, and you can have up to 3 attempts at each question depending on the question type. The quizzes at the end of each unit count towards achieving your Digital Badge for the course. You must score at least 80% in each quiz to achieve the Statement of Participation and Digital Badge.
Enter quiz3.13 A mid-course review
![]()
Congratulations on getting halfway through the course.
Watch the video above to review what you’ve learnt so far and find out what you will learn in the second part of this course. Remember there are no forums on this course as indicated in the video, but some of the discussions and learning from those facilitated forums have been integrated into this version of the course through activities and enhanced teaching content.
Now go to Unit 4: Reporting.
References
Craven, S., Brown, S. and Gilchrist, E. (2006) ‘Sexual grooming of children: Review of literature and theoretical considerations’, Journal of Sexual Aggression, vol. 12, no. 3.