11 Phishing
- Many criminals will try to get you to reveal passwords and other account information by pretending to be someone else. This shouldn’t be an issue if you follow the advice already covered in this course – in particular that you should never share your passwords. However, some criminals are very skilled, and send emails and texts that appear to come from legitimate sources, such as a bank or a government agency:
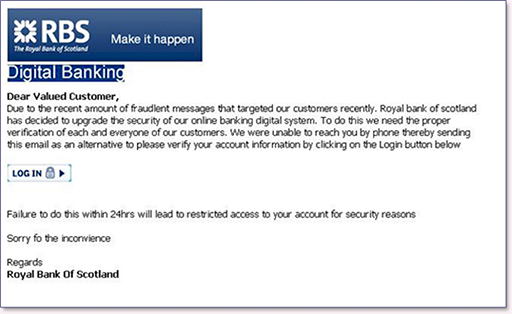
Figure 26
- These messages will normally direct you to a website, which may appear very convincing but is designed to capture all your login information. To protect yourself from phishing, remember that legitimate organisations do not conduct sensitive business via email or text – they will generally use the telephone or send a letter. When they do email, it will be a request for you to login to your account securely, so be suspicious of any links to websites that could be run by fraudsters.
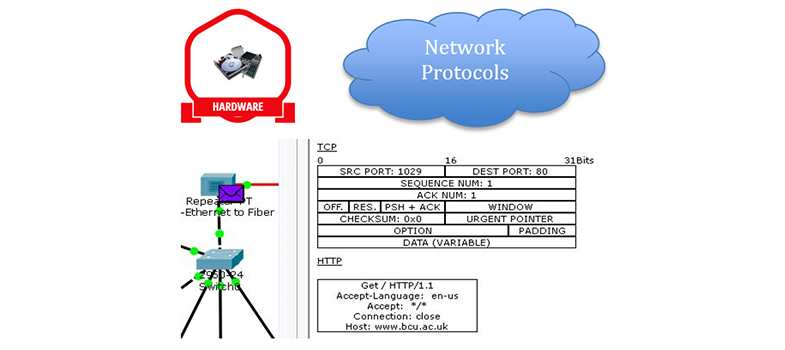
- Always check the address bar of your web browser to see which application layer protocol is being used to send your sensitive information to a website. Responsible organisations will use HTTPS, which is a secure version of HTTP and can prevent your data being intercepted by Internet-based criminals:
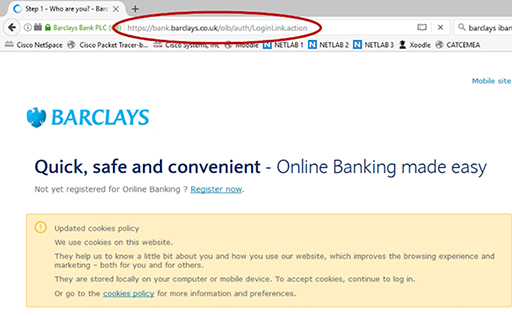
Figure 27
Back to previous pagePrevious
10 Malware