12 Activities
Activity: Investigating your home network
Activity: Network devices and protocols – Packet Tracer
We connect our devices to the Internet and the Internet connects them all together. But what is the Internet made of? We say it interconnects all the devices, but how?
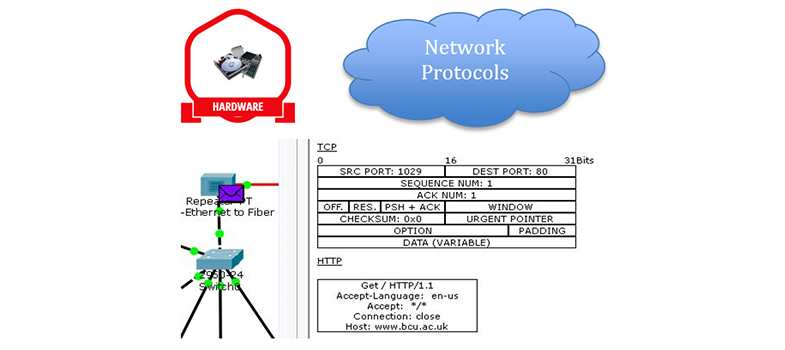
Network devices are mainly hubs, switches or routers. There are lots of other specialist bits, but the bulk of the interconnectivity is done by switches and routers. In this course you have looked at client server models, web requests and emails. What do these messages look like and how are they sent?
For each type of communication over the network there are a set of rules and specifications as to what format and order the information is sent. These are called protocols and they are fundamental in understanding how the Internet works.
This Packet Tracer lab explores the devices and protocols used in computer networks. You will need:
- Lab Book: Identify Devices and Protocols Used in Computer Networks [Tip: hold Ctrl and click a link to open it in a new tab. (Hide tip)]
- Packet Tracer
- CASBIT.pkz
Activity: Password hints
Companies do not store a user’s passwords in clear text – they send it through a scrambling algorithm to produce a 'hash', and the hash is then saved. The hash algorithm does not work in reverse, so you can't unscramble a hash to get the original password. When you enter your password the site uses the same algorithm to make a hash, which it then compares to the hash saved against your details.
Some sites allow you to store password hints, and they save these as clear text. Adobe was hacked in 2013, and its hashed passwords and hints were stolen for thousands of customers. The hackers looked at all the hints that gave the same hash (hence were the same password). Because they had lots of hints for the same password it was easy to guess what they were.
Can you guess the passwords used in this puzzle based on the stolen hints?
11 Phishing