1.3 Cyber security attacks and phishing
This section is part of the amber and green pathways.

Transcript
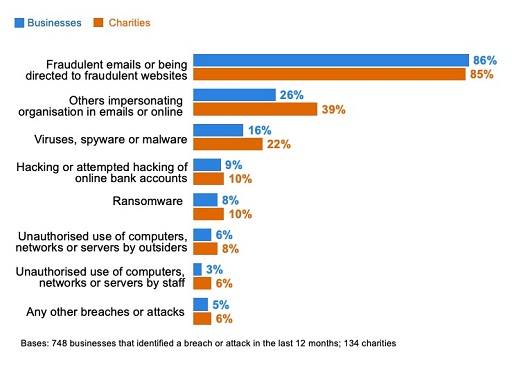
The nature of cyber attacks has changed since 2017 (see Figure 5). Over this period, there has been a rise in businesses experiencing phishing attacks (from 72% to 86%), a fall in viruses or other malware (from 33% to 16%), and a fall in ransomware (from 17% to 8%) (DCMS, 2020). Let’s now look a little into what phishing is.
Phishing
It may be surprising that many cyber security breaches do not result from technical failures. In fact, it is commonplace for attackers to exploit the goodwill and trust of people to gain access to systems, using a form of attack that is known as ‘social engineering’. Pretending to be technical support personnel or crafting emails that ask for usernames and passwords are common forms of social engineering attacks. You may have heard the term ‘phishing’ used to describe these kinds of emails. Phishing is a form of social engineering. In the video, course guide Cory explains how it happened to him.
In the next section you’ll find out about three high profile cyber security breaches.