2 Understanding current threats
This section is part of the amber and green pathways.
Now you know what information assets you have, you’ll look at how those assets can be compromised.
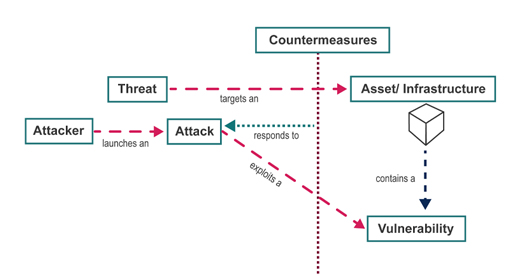
You will learn about some different kinds of threat, the vulnerabilities that they exploit and some countermeasures that can be put in place to guard against them. Figure 12 illustrates the context of these terms. When we use those terms we mean:
- vulnerability – a point at which there is potential for a security breach
- threat – some danger that can exploit a vulnerability
- countermeasure – action you take to protect your information against threats and vulnerabilities.
Threats can take many different forms, including unauthorised access to data with the intent of committing fraud against individuals or businesses. At its most extreme, there is the potential for the systematic disruption of computer networks and services, putting cyber security threats on a par with those associated with terrorism. In 2010, the UK government’s National Security Strategy highlighted cyber security attacks on the UK as a ‘Tier 1’ threat, which means they are one of the highest priorities for action.
New threats are being discovered all the time and they can affect any and every operating system, including Windows, Mac OS, Linux, Android and iOS.
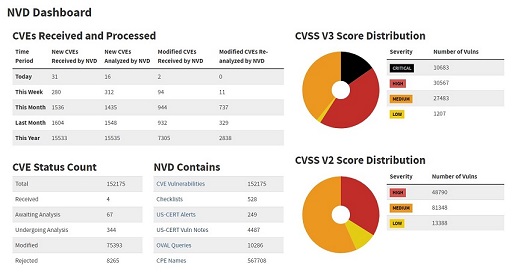
Vulnerabilities discovered are listed in the National Vulnerabilities Database (NVD) by the National Institute of Standards and Technologies (NIST), USA. The vulnerabilities are detailed in numbered documents termed ‘Common Vulnerabilities and Exposure’ (CVE), for example CVE-2020-1299 (A remote code execution vulnerability exists in Microsoft Windows). The dashboard on the NVD website provides comprehensive count of the vulnerabilities reported and their severity.
To protect ourselves it is important to keep ourselves up to date with the latest cyber security news.
Next, you will explore how a cyber security threat is described in the Windows and Mac OS platforms by watching a video relevant to your computer’s operating system if possible.