1 Online, the new frontline
This section is part of the amber pathway.

Transcript
We shop online. We work online. We play online. We live online. More and more, our lives depend on online, digital services. Almost everything can be done online – from shopping and banking to socialising and card making – and all of this makes the internet, also known as cyberspace, an attractive target for criminals. Yes, theft, fraud, bullying, victimising and other such activities extend into the online world. We need to protect ourselves from threats – our identity being used by someone else, our information being seen by those that you didn’t intend to share with, and our online resources being used by anyone other than us.
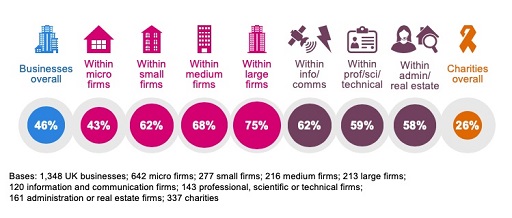
Large-scale cyber security breaches often make the headlines but about 70% of organisations are keeping their worst security incidents under wraps, so what makes the news is just a small proportion of the breaches that are actually taking place. Larger businesses are more likely to identify breaches or attacks (see Figure 1) than smaller ones – this has been a consistent pattern in each year of the survey. Charities follow the same pattern, with 57 per cent of high-income charities (with incomes of £500,000 or more) recording any breaches or attacks.
Britain is being targeted by up to 1,000 cyber attacks every hour. It is the case that most often commercial organisations or services are the targets for cyber security breaches (also termed as cyber attacks) for the obvious commercial gains. The average damage cost per breach is estimated at £4380 (DCMS, 2020).
| All businesses | Micro/small businesses | Medium/large businesses | All charities | |
|---|---|---|---|---|
| Across organisations identifying any breaches or attacks | ||||
| Mean cost | £1010 | £919 | £3070 | £1560 |
| Median cost | £0 | £0 | £0 | £0 |
| Base | 710 | 432 | 278 | 129 |
| Only across organisations identifying breaches with an outcome | ||||
| Mean cost | £3230 | £3110 | £5220 | Too few |
| Median cost | £274 | £244 | £935 | charities to analyse |
| Base | 160 | 88 | 72 |
Behind the numbers
Cyber security is definitely one of those areas where you need to evaluate the validity of any information you find online before accepting it. The figures about the prevalence and under-reporting of cyber attacks comes from a 2010 CyberSecurity Watch survey carried out in the US by a number of organisations, including the US Computer Emergency Response Team. The survey states that ‘the public may not be aware of the number of incidents because almost three-quarters (72%), on average, of the insider incidents are handled internally without legal action or the involvement of law enforcement’ (CERT Insider Threat Center, 2010).
The estimate of 1,000 attacks per hour is based on the BIS Cyber Security Breaches Survey 2014. We took the number of organisations that reported that they were attacked ‘hundreds of times a day’ in different ways, and assumed that each of these responses were attacked a minimum of 100 times per day, we worked out that there were at least 24,156 attacks per day across the 1,098 organisations surveyed. Dividing this by 24 suggests that there are a minimum of 1,000 attacks per hour. According to a UK-based ISP’s survey, ‘… companies with internet connections experienced 157,000 attacks each, on average … the equivalent of more than one a minute’ (Beaming, 2020). These costs can occur as direct financial losses due to fraud or theft; the loss of productivity due to time spent recovering from the effects of a successful attack; or the loss of trust and reputation
We all have a responsibility to protect services from being maliciously disrupted or misused, through our vigilance, through our own security measures and through reporting events when they arise.
The knowledge, tools and best practices relating to protecting the computers, communications networks, programs and data that make our digital lives possible are collectively referred to as cyber security, or information security. For the purposes of this course, we use the two terms interchangeably .
Let’s get started by learning some of the basic terminology used when discussing cyber security.