1.4 Examples of high profile cyber security breaches
This section is part of the amber and green pathways.
Cyber security attacks take many forms from obtaining users’ personal information, to attacking critical national infrastructure and obtaining companies’ proprietary data. Here we describe four high profile cyber security breaches which caused major financial losses and damaged the reputations of the organisations concerned.
Attacking online identities
Adobe Systems is one of the more important companies in the digital economy. Its software is used to produce, publish and present an enormous amount of material – chances are your favourite magazines and books were laid out with Adobe software.
Over the years, Adobe had stored the names, addresses and credit card information of tens of millions of users on its servers. Then, in October 2013, Adobe admitted that data from 2.9 million accounts had been stolen. Later, that number was revised to 38 million accounts, but when the data file was found on the internet it contained no less than 153 million user accounts. Much of this data could be read and soon copies of the stolen accounts were in wide circulation. It also became clear that the people who had stolen user data had also gained access to Adobe’s development servers – program code, potentially worth billions of dollars, had also been stolen.
Adobe was forced to change the log in details of every one of its users and to greatly improve its own security. And, of course, users sued Adobe for not protecting their information.
Is Adobe alone, or are other companies holding valuable data but not protecting it properly?
Attacking industrial systems
Not many people want a uranium centrifuge, but those that do, really want a uranium centrifuge. The centrifuge was developed after the Second World War for enriching uranium so that it can be used either for generating nuclear power, or, as the heart of a nuclear weapon.
Under international treaty it is not illegal for countries to slightly enrich uranium for nuclear energy, but high levels of enrichment are forbidden to all but a handful of countries. As a consequence, centrifuge technology is tightly controlled, but still, centrifuges have gradually spread around the world. Most recently they have been developed by Iran, ostensibly for that country’s legal civil nuclear programme; but it is sometimes suspected it might possibly be for the development of an Iranian nuclear bomb.
In the summer of 2010, a new piece of malicious software for the Microsoft Windows operating system was discovered by an antivirus company in Belarus. The software was dissected and found to attack a very specific set of computer-controlled high-speed motors manufactured by Siemens. Left unchecked, the software, dubbed ‘Stuxnet’, would rapidly increase and decrease the speed of the motors causing irreparable damage to whatever was connected to them – among other things, uranium centrifuges.
The very specific nature of the systems targeted by Stuxnet make many believe that it was developed specifically to disrupt the Iranian uranium enrichment programme. By the autumn of 2010, reports were appearing that the Iranian centrifuge programme was in trouble. The Israeli paper Haaretz reported that Iran’s centrifuges had not only produced less uranium than the previous year, but that the entire programme had been forced to stop and start several times because of technical problems. Other sources reported that Iran had been forced to remove large numbers of damaged centrifuges from its enrichment plant.
Attacking specific targets
In December 2013, the American retailer Target announced that hackers had stolen data belonging to 40 million customers. The attack had begun in late November and continued for several weeks before it was detected. By then it had compromised more than 110 million accounts, including unencrypted credit and debit card information as well as encrypted PIN data. By February 2014, American banks had replaced more than 17 million credit and debit cards at a cost of more than $172 million. The amount of fraud linked to the attack is unknown, as is the damage to Target’s reputation.
Target was not the first major retailer to be hit by hackers, but this attack was different from most; the weakness that allowed the attackers into the Target computers lay outside of the company. The hackers had gained access through computers belonging to one of Target’s heating, ventilation and air conditioning services (HVAC) contractors. Like many large organisations, Target allows other companies to access its internal networks, to submit bills and exchange contracts.
The hack appears to have begun when an employee of the HVAC company received an email from one of their trusted partners. In fact, the email was fake and contained malicious software. Unlike traditional spam email, this message had been targeted at a very specific audience – the HVAC company. It was what is known as ’spear phishing’.
Once the email had been opened, the hidden software went to work and retrieved the HVAC company’s Target network authorisations, allowing them to log on to their real objective. In an ideal system, the HVAC company’s authorisations should have restricted them to a network responsible solely for billing and contracts, but, like a lot of big organisations, Target used a single network for all of its data, allowing the attackers to eventually locate, and steal, customer data.
The Target attack is an example of an advanced persistent threat. Rather than attempting to attack the retailer directly, the hackers had chosen an external company which was much less likely to have the resources to detect and defend against an attack. Their spear phishing email was directly targeted at the contractor, lulling them into a false sense of security and allowing the malware to retrieve the logon credentials needed to attack Target itself.
Phishing in the times of COVID-19
Since the declaration of COVID-19 as a pandemic, the term ‘COVID-19’ and ‘Coronavirus’ are being used by attackers to lure the users to specific websites to capture their personal credentials or to download malware on to their devices (CISA, 2020). The NCSC, UK and CISA, USA issued a joint alert on the 8th April 2020 after having observed phishing campaigns both via email and SMS. Some examples of the ‘Subject:’ lines of the phishing emails are:
- 2020 Coronavirus Updates
- Coronavirus Updates
- 2019-nCov: New confirmed cases in your City
- 2019-nCov: Coronavirus outbreak in your city (Emergency)
The emails had a web link, to persuade the victim to visit a website for stealing user data, such as usernames and passwords, credit card information, and other personal information (CISA, 2020).
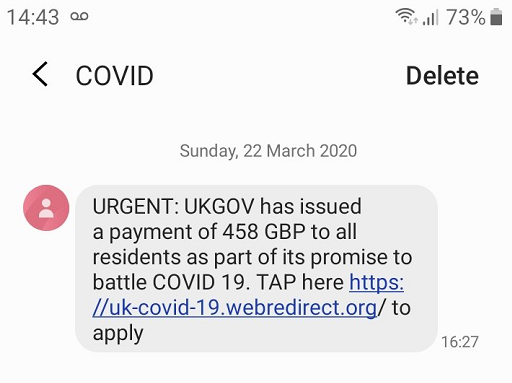
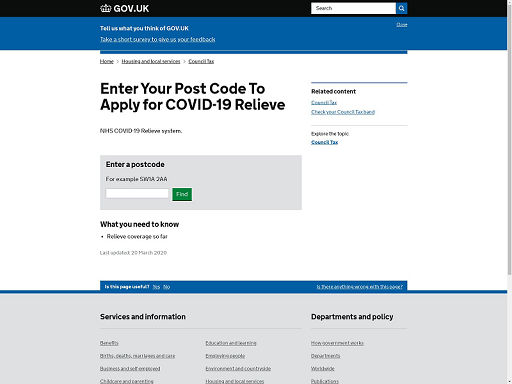
Similar messages were sent out via SMS. The messages contained an urgent call for action with a web link and requested the recipients to visit it. The destination website may present as a convincing clone to an unsuspecting user, as seen below.
In addition to SMS, CISA and NCSC have warned to look at other modes of messaging including WhatsApp and social networking platforms. CISA and NCSC mention ‘Malicious cyber actors are likely to continue using financial themes in their phishing campaigns. Specifically, it is likely that they will use new government aid packages responding to COVID-19 as themes in phishing campaigns’ (CISA, 2020).
Activity 1 Describing cyber security breaches
Choose one of the three example attacks outlined above. You can choose Adobe, Stuxnet or Target.
Try and relate the terminologies you’ve learned so far to the attacks and write responses to the questions below:
- Which of the CIA concepts is relevant to the example you have chosen?
- Was a malware involved in the attack? If so, what type of malware was it?
- What was the asset that was affected by the attack?
Please complete Quick poll #1 [Tip: hold Ctrl and click a link to open it in a new tab. (Hide tip)] now.
Open the poll in a new window or tab then come back here when you’re done.