1.1 Worms
This section is part of the amber and green pathways.
Another type of self-replicating malware is the worm; like a virus it is designed to make copies of itself. But unlike a virus, which attach themselves to specific applications, a worm is a standalone application.
Worms spread through network connections, accessing uninfected machines and then hijacking their resources to transmit yet more copies across the network.
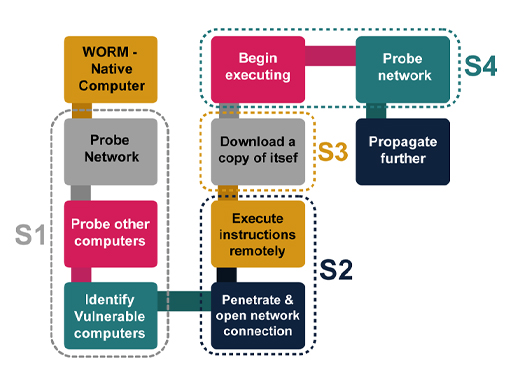
There are four stages in a worm attack:
- The first stage is when the worm probes other machines looking for a vulnerability that can be exploited to copy itself to.
- The second stage is to penetrate the vulnerable machine by performing the operations for exploiting the vulnerability. For example, the worm might detect an open network connection, through which it can get the remote machine to execute arbitrary instructions.
- In the third stage, the worm will download itself to the remote machine, and store itself there. This is often called the ‘persist’ stage.
- In the final stage, the worm will propagate itself by picking new machines to attempt to probe.
Worms were invented as a curiosity and have even been suggested as ways of testing networks or distributing software patches across a network; however their drawbacks far outweigh their benefits. Even the most ‘benign’ worm consumes resources and can affect the performance of a computer system.