2.1 Understanding security notices
Windows
Watch this video if your computer runs Windows operating systems. If you have a Mac, you will find a video for the Mac operating system below. You do not need to watch both Windows and Mac videos.
Transcript
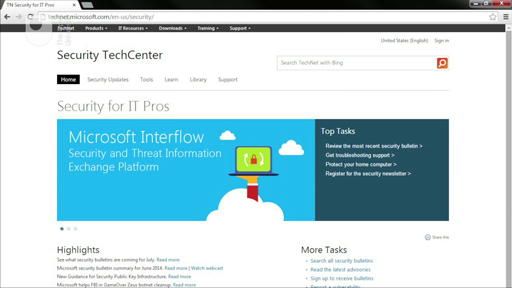
Large software companies publish security notices when they discover a threat. It can be hard to read these notices to find the important bits. Therefore it’s helpful to know where to find them and what to look out for.
Visit the Microsoft Security Response Center [Tip: hold Ctrl and click a link to open it in a new tab. (Hide tip)] to see the latest security threats.
Mac OS
Watch this video if you have a Mac and run a Mac operating system. (If your computer runs a Windows operating system and you have watched the video in the previous section, you do not need to watch this video.)
Transcript
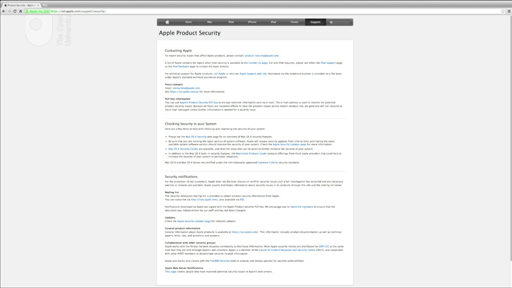
Large software companies publish security notices when they discover a threat. It can be hard to read these notices to find the important bits. Therefore it’s helpful to know where to find them and what to look out for.
Visit the Apple Product Security website to see the latest security notifications.
