1.1 How data moves around the internet
Transcript
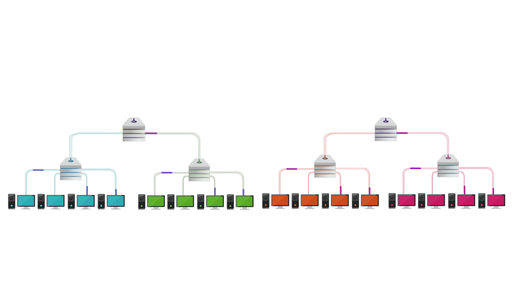
The video explains how data is routed across a network of computers and how the internet is resilient to failures of individual computers, known as nodes of the network, or connections between computers, known as the links.
Instead of using a dedicated circuit for all of the information, internet traffic is split up and may take any number of routes through the network moving from its origin to the destination by a series of hops.
Note: Early in the above the video [2:05], an example packet is shown with destination address 6.7.8.104. However, there are subsequently two separate examples of different packets being routed. In the first example, the packet is being sent to a host on the local network, 1.2.3.104 and in the second example it is being sent to a remote host, 6.7.8.101.
