Learning Outcome 1: Gather Data
Information Sheet 1.1-1:
Identifying Data Sources & Ethical Gathering
The TESDA National Competency Assessment is not just an evaluation of a candidate's skills; it is a rich data-generating process. The integrity of the entire competency-based system relies on the accurate identification of data sources and the ethical gathering of information.
The importance of high-quality input data in the TESDA National Competency Assessment cannot be overstated. It is the fundamental bedrock upon which the entire system's credibility, fairness, and effectiveness are built.

Think of it this way: Garbage In, Garbage Out (GIGO). If the data entering the system is flawed, every certificate, and policy based on that data will be compromised.
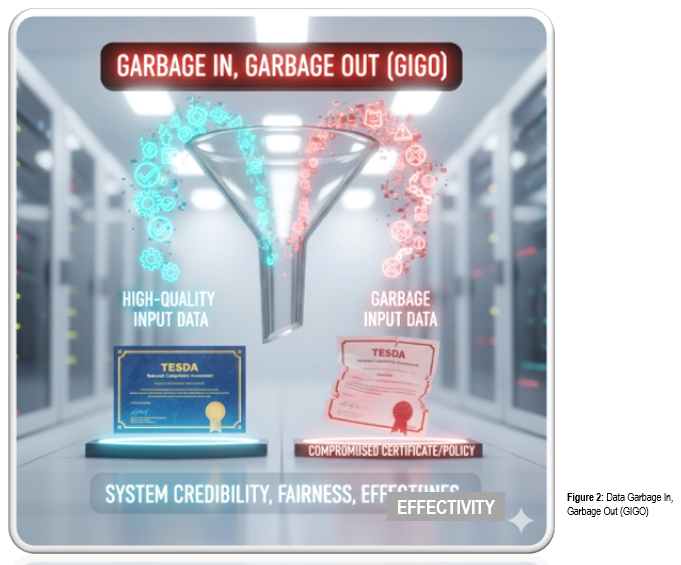
The first step in any data gathering project is to gather the raw materials. The quality of your data input directly determines the quality of your output.
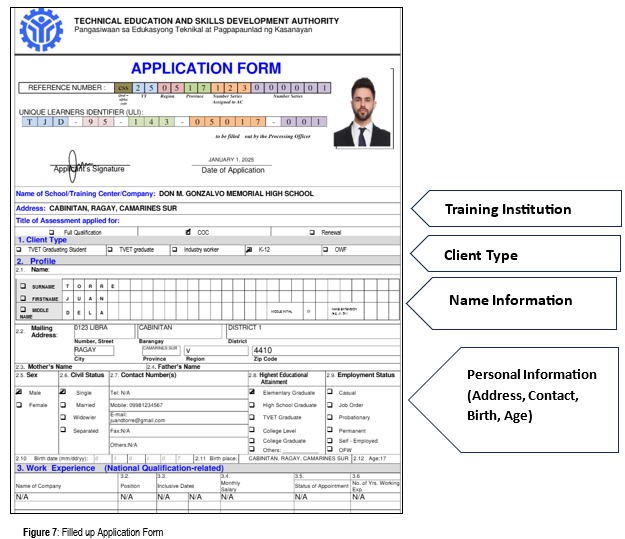
Identifying Data Sources: Data sources are identified based on the requirements, which are often specified in input forms. Common data sources include:
TESDA National Assessment Application Form (TESDA-OP-CO-05-F26)
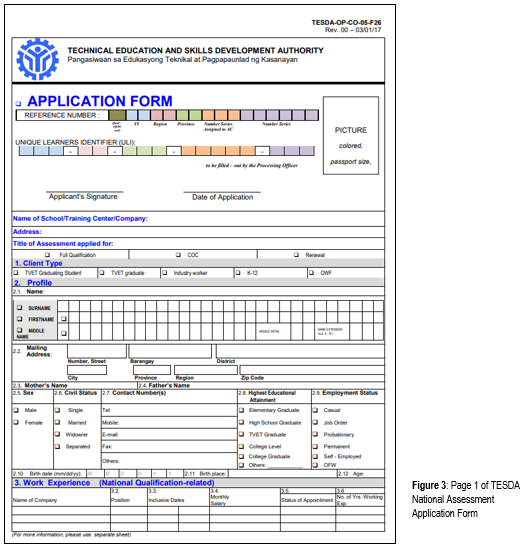
Data input sources can also be any of the following:
- Certificate of Training (Graduate of formal, non-formal, and informal, including enterprise-based training programs);
- Certification from a TVET provider/institution that the candidate completed the training requirements of the qualification;
- Certificate of Employment for experienced workers; and
- Certification from the Local Government Unit for Practitioners.

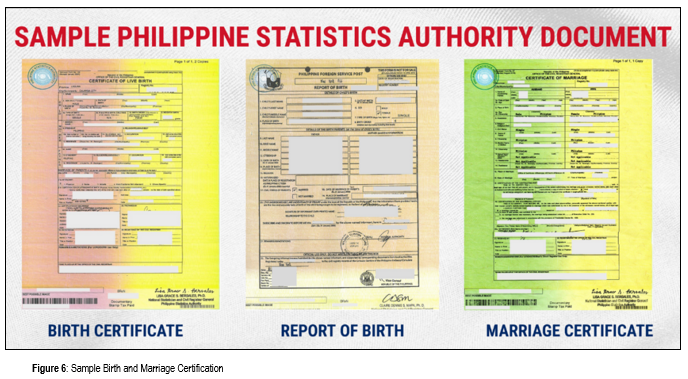
Birth Certificate, if necessary
Data Collection and Organization: Once sources are identified, you must collect the relevant information and organize it into logical categories. For example, if you are gathering student profiles, you would categorize the data into fields like 'Full Name', 'Date of Birth', 'Address', etc.
The Data Privacy Act (R.A. 10173): This is the most critical legal consideration in data gathering. You have an ethical and legal responsibility to protect any Personally Identifiable Information (PII) you handle. Always ensure that you have the proper consent to collect data and that you store it securely.
“Personal Information” (PI) refers to any information, whether recorded in a material form or not, from which the identity of an individual is apparent or can be reasonably and directly ascertained by the entity holding the information, or when put together with other information would directly and certainly identify an individual.
Examples: Name, address, contact details, biometric data, financial records, or any data that can link to a specific person (e.g., IP addresses combined with browsing history).
Coverage: Applies to all types of personal data processed for legitimate purposes, such as contracts, legal obligations, or public functions, but must adhere to principles like fairness, accuracy, and minimal retention.

Sensitive Personal Information (SPI) Sensitive personal information is a subset of personal information that requires stricter consent and protection due to its potential for harm if misused. It includes:
About an individual’s race, ethnic origin, marital status, age, color, and religious, philosophical, or political affiliations;
About an individual’s health, education, genetic or sexual life of a person, or to any proceeding for any offense committed or alleged to have been committed by such individual, the disposal of such proceedings, or the sentence of any court in such proceedings;
Issued by government agencies peculiar to an individual, which includes, but is not limited to, social security numbers, previous or current health records, licenses or their denials, suspension or revocation, and tax returns; and
Specifically established by an executive order or an act of Congress to be kept classified.

Processing Restrictions: Sensitive data can only be processed with explicit consent, for legal obligations, to protect life/health, or in specific public/medical contexts, and must be secured against breaches.
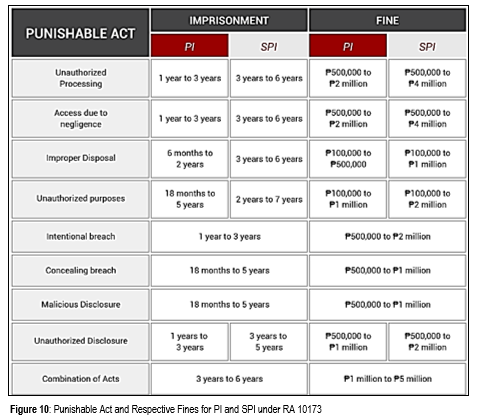
Punishable Act under R.A. 10173 for Personal Information (PI) and Sensitive Personal Information (SPI) violations
Verifying Authenticity: How do you know the data you received is real? TESDA Provincial Offices and Assessment Centers should have operating procedures for verification. This may include:
- Cross-referencing with other known sources.
- Contacting the source directly to confirm details.
- Checking for official seals or signatures on physical documents.
For TESDA, data is the lifeblood of a credible certification system. By meticulously identifying data sources through its structured forms and adhering to strict ethical gathering principles. This process not only certifies individuals but also generates the trustworthy data needed to strengthen the entire Philippine TVET ecosystem.
