Privacy Threat Modeling Frameworks
LINDDUN
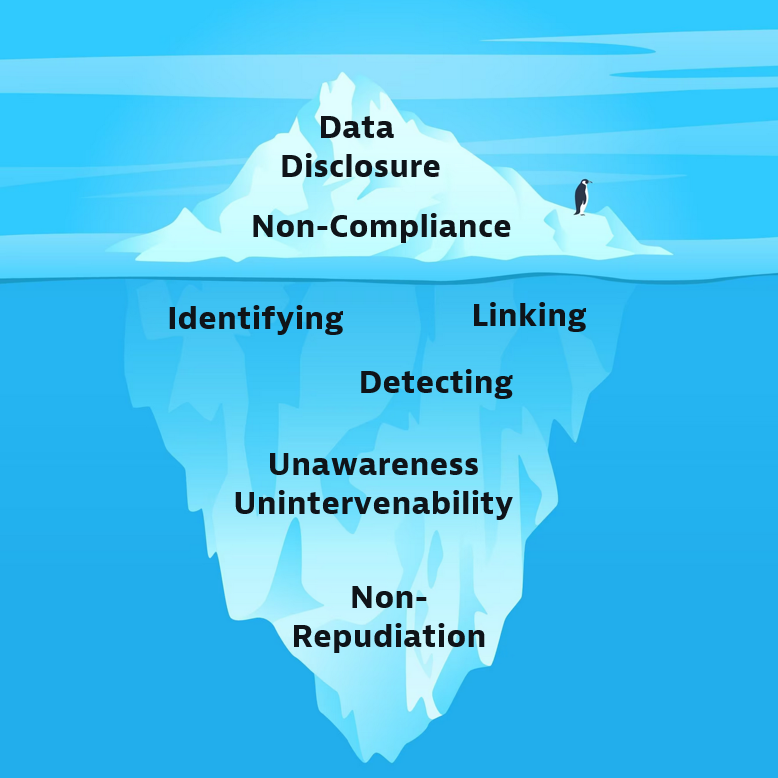
LINDDUN is a threat modeling framework for privacy threats developed at KU Leuven. It categorizes privacy threats into 7 types: Linking, Identifying, Non-Repudiation, Detecting, Data Disclosure, Unawareness, and Non-Compliance. It is by far the most widely-known privacy threat modeling framework, and has been included in the ISO 27550 standard on privacy engineering for system life cycle processes and in the European Data Protection Supervisor's Preliminary Opinion on Privacy by Design. A simplified threat model is available as cards (LINDDUN Go) to gamify the threat modeling process. To learn more about each threat type, click on its card below.
💻 Exercise: check out the detailed LINDDUN threat trees, which include specific threats and a range of examples for each of the threat categories above. Have you encountered any of these threats as a tech user? How did that make you feel? What could the product have done differently to make you feel safer and reduce the risk of harm to you?
Models of Applied Privacy
The MAP framework combines LINDDUN with other threat and harm taxonomies to categorize threat actors, threat mechanisms (i.e. categories, such as Linkability from LINDDUN), and threat impacts (i.e. privacy harms). The framework's unique aspect is that it is persona-based. Rather than just thinking about broad categories of threat actor like 'malicious insider' or 'data protection regulator', investing the time to imagine your actor's motivation, skill level, and cultural context using MAP's persona cards can help you better anticipate their behavior. MAP's categorization also encourages you to think about threat actors acting with good intentions who may still cause privacy harms, such as a developer who simply doesn't consider privacy, or who thinks they are handling personal data appropriately but actually is not. Such non-malicious threat actors can sometimes pose the highest risk to your users.
Plot4AI
The Plot4AI framework is based around a library of threats across 8 categories:
- Non-Compliance
- Technique & Processes
- Accessibility
- Identifiability & Linkability
- Security
- Safety
- Unawareness
- Ethics & Human Rights
As the categories suggest, it also considers threats beyond privacy in the broader space of trust & safety. It was created with the goal of expanding LINDDUN's scope into artificial intelligence and machine learning. Even if you don't work with this, the framework is worth checking out, because many other threats are broadly applicable. The threat library is phrased as a series of very specific questions, which are a helpful starting point if you're struggling for ideas when threat modeling. They can also help you identify your threat "blind spots". For example, perhaps you routinely assume your users are adults and forget to consider threats to children: the library has a question ready to remind you.
Further Reading
- LINDDUN privacy threat modeling: a tutorial - Kim Wuyts and Wouter Joosen (2015). There's a lot more to LINDDUN than the categorization, and this tutorial dives into detail about how you could document and mitigate the identified threats. Note that, depending on your development context, the more formal requirements engineering aspects may be unnecessary. Make sure your threat modeling process works for you: it can be as informal or as formal as you need.
- A detailed list of LINDDUN threat examples
- A LINDDUN-Based Privacy Threat Modelling for National Identification Systems by Nweke et al. (2022) describes in detail how they applied LINDDUN to identify and mitigate privacy threats.
